Articles tagged oauth
Develop a XAA-Enabled Resource Application and Test with Okta

From an enterprise resource app owner’s perspective, Cross App Access (XAA) is a game-changer because it allows their resources to be “AI-ready” without compromising on security. In the XAA model, resource apps rely on the enterprise’s Identity Provider (IdP) to manage access. Instead of building out interactive OAuth flows, they defer to the IdP to check enterprise policies and user groups, assign AI agent permissions, and log and audit AI agent requests as they occur....
Introducing xaa.dev: A Playground for Cross App Access
AI agents are quickly becoming part of everyday enterprise development. They summarize emails, coordinate calendars, query internal systems, and automate workflows across tools. But once an AI agent needs to access an enterprise application on behalf of a user, things get complicated. How do you securely let an AI-powered app act for a user without exposing credentials, spamming consent prompts, or losing administrative control? This is the problem Cross App Access (XAA) is designed to...
Okta Developer Connect Recap

Identity has become one of the most important control points in modern systems. As applications grow more distributed and AI-driven automation becomes part of everyday workflows, identity increasingly defines how secure, predictable, and trustworthy those systems are. Decisions about access, scope, and lifecycle now shape not only the user experience, but also how well security holds up as systems scale. With this shift in mind, we hosted our first flagship Okta Developer Connect event in...
Introducing the Okta MCP Server

As AI agents and AI threats proliferate at an unprecedented rate, it becomes imperative to enable them to communicate safely with the backend systems that matter the most. A Model Context Protocol (MCP) server acts as the bridge between an LLM and an external system. It translates natural language intent into structured API calls, enabling agents to perform tasks like provisioning users, managing groups, or pulling reports, all while respecting the system’s security model. Establishing...
Build Secure Agent-to-App Connections with Cross App Access (XAA)

Secure access with enterprise IT oversight between independent applications that communicate with each other is a recognized gap in OAuth 2.0. Enterprises can’t effectively regulate cross-app communication, as OAuth 2.0 consent screens rely on users granting access to their individual accounts. Now, with the advent of AI agents that communicate across systems, the need to solve the gap is even greater – especially given the growing importance of enterprise AI security in protecting sensitive data...
Secure Your Express App with OAuth 2.0, OIDC, and PKCE

Every web application needs authentication, but building it yourself is risky and time-consuming. Instead of starting from scratch, you can integrate Okta to manage user identity and pair Passport with the openid-client library in Express to simplify and secure the login flow. In this tutorial, you’ll build a secure, role-based expense dashboard where users can view their expenses tailored to their team. Check out the complete source code on GitHub and get started without setting...
Integrate Your Enterprise AI Tools with Cross-App Access
SaaS apps not only have to meet the rigorous demands of managing users at an enterprise level but must also be secure and resilient by design. In “An Open Letter to Third-party Suppliers”, Patrick Opet, Chief Information Security Officer of JPMorgan Chase, writes: “Modern integration patterns, however, dismantle these essential boundaries, relying heavily on modern identity protocols (e.g., OAuth) to create direct, often unchecked interactions between third-party services and firms’ sensitive internal resources.” Modern identity...
How to Build Secure Okta Node.js Integrations with DPoP

Integrating with Okta management API endpoints might be a good idea if you are trying to read or manage Okta resources programmatically. This blog demonstrates how to securely set up a node application to interact with Okta management API endpoints using a service app. Okta API management endpoints can be accessed using an access token issued by the Okta org authorization server with the appropriate scopes needed to make an API call. This can be...
Why You Should Migrate to OAuth 2.0 From Static API Tokens
Static API tokens have long been used to call external APIs and access the resources of third parties such as software vendors. As API standards have evolved, OAuth 2.0 emerged as the option offering more robust security, greater flexibility, and a better developer experience. Let’s explore the advantages of moving away from static tokens in favor of OAuth 2.0. Table of Contents Static API token landscape Shift from static API tokens to OAuth 2.0 for...
Selecting the Best Authorization for Your API Integrations
Integrating with an API lets you power up your code by knowing what the API knows and doing what the API can do. The catch is that most APIs can’t and shouldn’t let just anybody access your important resources. Just as humans log in to access resources, programs accessing APIs must obtain proper authorization. Your application can use two types of authorization mechanisms when calling Okta APIs from your Okta integration, each with its pros...
How Authentication and Authorization Work for SPAs

Adding authentication to public clients such as Single Page Applications (SPA) and JavaScript applications can be a source of confusion. Identity Providers like Okta try to help you via multiple support systems. Still, it can feel like a lot of work. Especially since you’re responsible for way more than authentication alone in the applications you work on! As part of authentication, your client application makes multiple calls to an authorization server, and you get back...
The Identity of OAuth Public Clients

I recently got back from a series of events filled with lots of interesting discussions around various OAuth-related topics. At the official IETF meeting in Vienna back in March, I presented the latest work on OAuth 2.1 and we discussed and made progress on some of the current open issues. At the OAuth Security Workshop a few weeks later, I presented a session on client authentication for mobile apps, and there were many more presentations...
Authenticate from the Command Line with Java
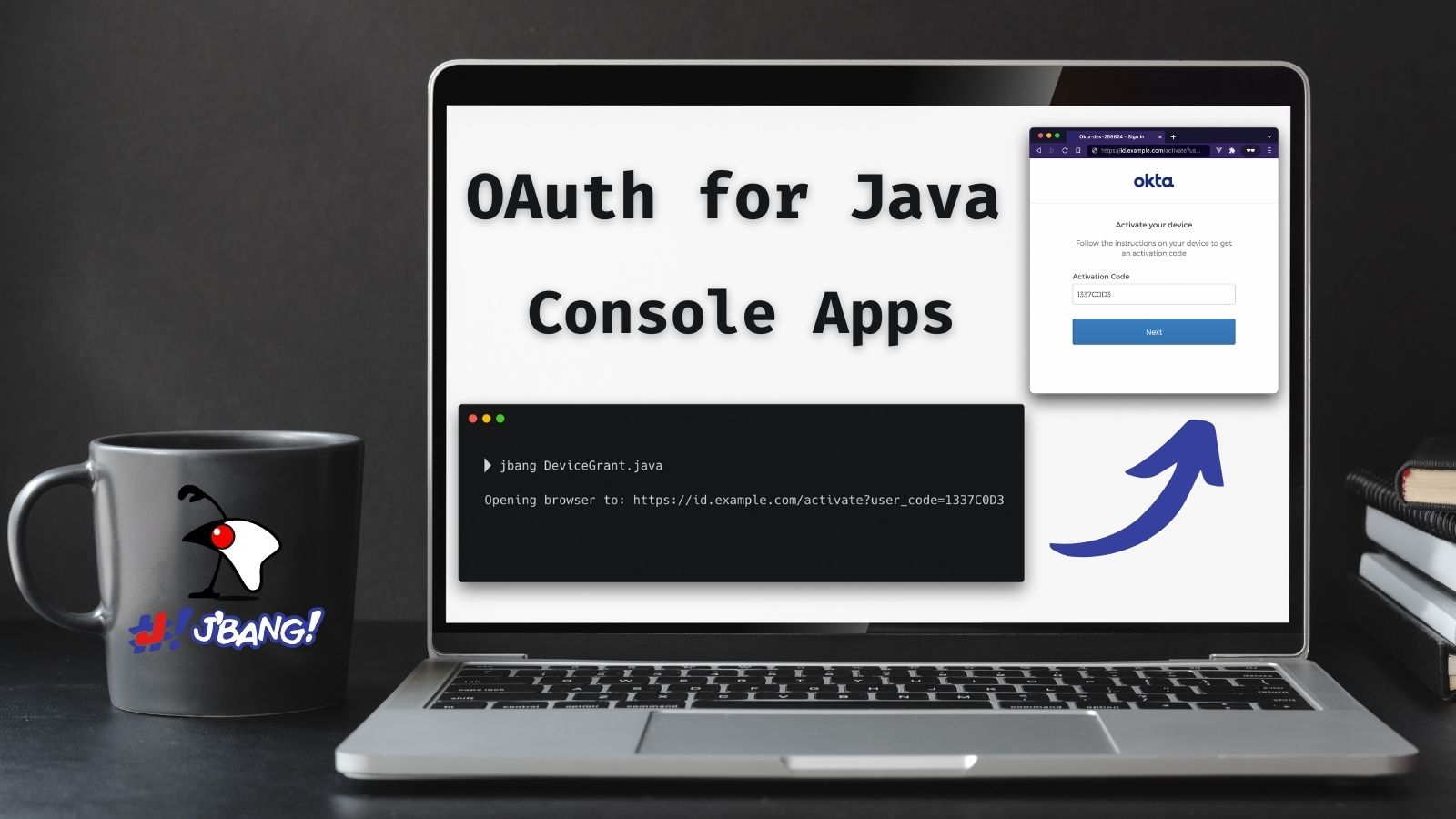
Anyone who has tried to type a password using a television remote can tell you what a pain it is. Not only will you be frustrated with the keyboard, but it’s not secure; everyone else in the room can see what you are typing. Fortunately, the OAuth 2.0 Device Authorization Grant gives you an easier way to sign in. The name is a mouthful, but if you have ever logged in to a TV by...
Set Up the Private Key JWT Flow in Three Python Commands

The Private Key JWT flow is one of the more complicated OIDC flows to set up. At Okta, it’s commonly used to get OAuth4Okta access tokens which enable you to perform managementr tasks on your org. If you already know HOW it works and just want to get to the code, click here to skip ahead. If you’re looking to gain a better understanding of how it works, here’s a high level explanation: Once you’ve...
Native SSO: Desktop and Mobile Apps Single Sign-On

When you hear SSO (Single Sign-On), you probably immediately think of web apps, and how you only need to sign into one web app first, then all other web apps give you seamless access. Unfortunately, for desktop and mobile applications (often referred to as “native apps”), the seamless web SSO experience (also referred to as native SSO) has not caught on. This is partly due to the lack of an industry standard or best practice...
The Things to Keep in Mind about Auth
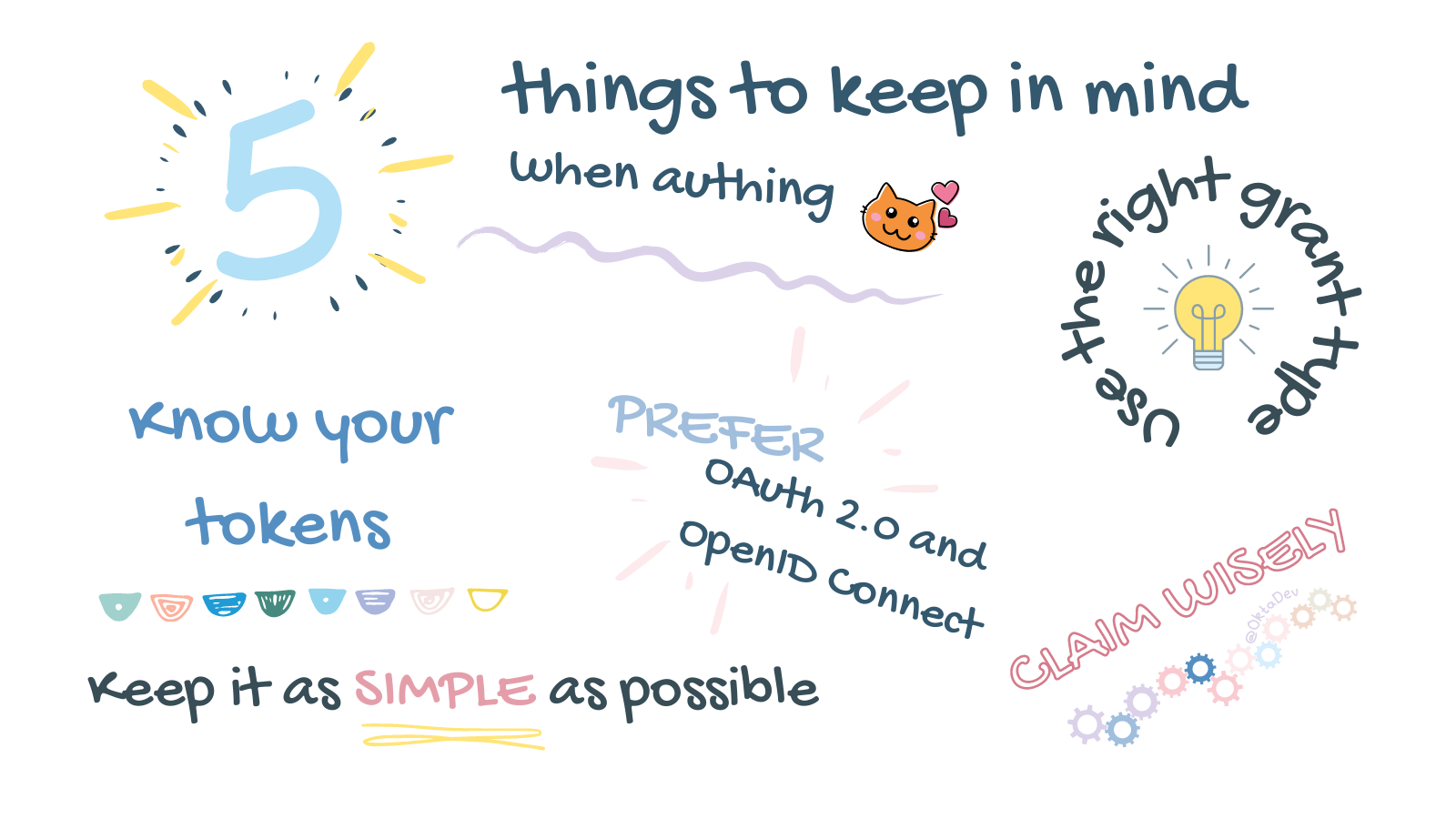
There’s a lot of information out there about adding authentication to your app, which is helpful! But also overwhelming. It can be hard to find relevant and up-to-date information. Security best practices and technologies change, so refreshing your understanding and keeping up with current best practices is a good thing. Here are some notes I took while I reviewed my knowledge and applied my experience implementing auth. Prefer OAuth 2.0 and OpenID Connect If you’re...
Command Line Login with the OAuth Device Grant

Even if you’ve never heard of the OAuth 2.0 Device Authorization Grant, formerly known as the Device Flow, you’ve probably seen it in action on a smart TV or other streaming device. The Device Authorization Grant is commonly used on devices with limited keyboard input ability. The process allows you to log in to an account more easily via a separate browser on your laptop, mobile phone, or other companion rich-input device. For instance, if...
What Apple's App Tracking Changes Mean for Developers
You know how you will see an ad on Instagram for something that you just searched for hours earlier? This is in no small part due to a special API for iOS that allows app developers to track your behavior across apps, even those by different developers. Well, all of this is changing with the rollout of iOS 14.5, so let’s take a look at what exactly is changing and what this means for app...
OAuth Patterns and Anti-Patterns - a DZone Refcard

I’m happy to announce the release of a brand new OAuth cheat sheet published through DZone’s Refcardz, “OAuth Patterns and Anti-Patterns”. This five-page reference guide covers the latest in OAuth and clarifies some common misunderstandings of applying it to real world use cases. With a focus on OAuth 2.0, OpenID Connect, and best practices, you’ll quickly learn how to avoid some common mistakes and how to make your applications and APIs more secure. The “OAuth...
Unity WebGL + PlayFab Authorization in 20 Minutes
As game creators, we hold a fundamental responsibility to protect and secure any and all data that our players entrust to us. Historically, security in games has not been high on the priority list because games were enjoyed anonymously and offline. But with our society becoming ever more connected, demand for social gaming experiences and online gaming features has increased exponentially. This has led to the development of cloud-based gaming platforms, such as PlayFab, that...
OAuth Sketch Notes - Live Q&A
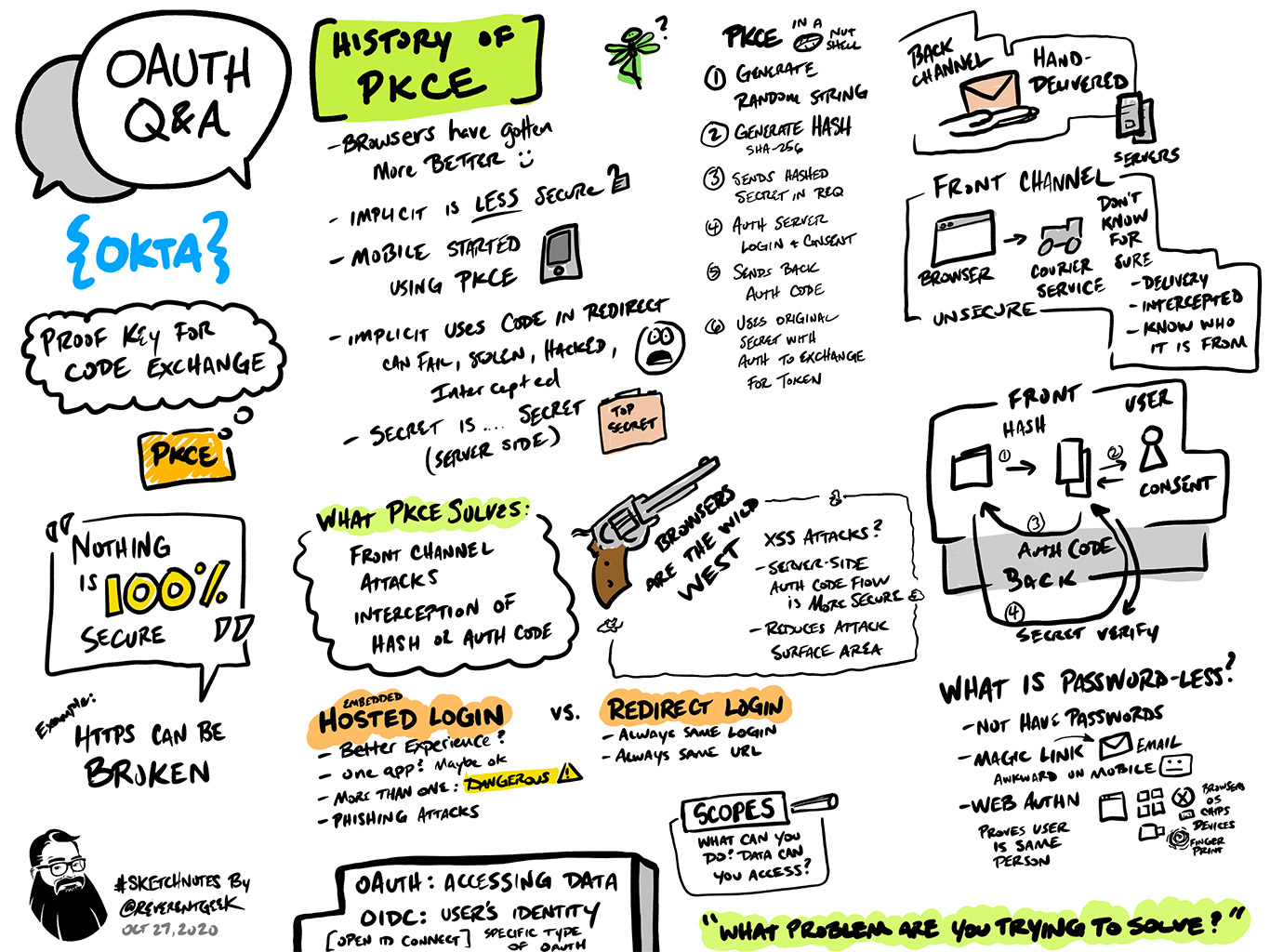
Why do we need PKCE in OAuth? How does PKCE work? What’s the difference between the front channel and back channel? Can SPAs even use a back channel? These are just a few of the things we talked about during this sketch notes livestream! Developer advocates Lee Brandt and Aaron Parecki discuss PKCE, cross-site scripting, OAuth vs OpenID Connect and more, all while David Neal sketched notes live! Some of the other topics covered include...
JWT vs Opaque Access Tokens: Use Both With Spring Boot

The topic of validating an OAuth 2.0 access tokens comes up frequently on this blog. Often we talk about how to validate JSON Web Token (JWT) based access tokens; however, this is NOT part of the OAuth 2.0 specification. JWTs are so commonly used that Spring Security supported them before adding support for remotely validating tokens (which is part of the OAuth 2.0 specification.) In this post, you will build a simple application that takes...
Build a Secure Java Application with Apache Shiro and OAuth 2.0
Apache Shiro is a Java security framework that can perform authentication, authorization, session management, along with a host of other features for building secure applications. In this tutorial, you will build a simple Java REST application using JAX-RS. JAX-RS, like many Java APIs, is a set of interfaces, and you will need to pick an implementation. For this post, I’ll use Jersey (the reference implementation of JAX-RS), but you can use Apache CXF, RESTeasy, or...
Build an Android Application with Authentication

With mobile apps becoming ever-present in users' lives, following best security practices has become essential in protecting your users and your apps. Implementing security alone and from the ground up can be costly for your development team, create a less-than-ideal user experience, and be susceptible to design/implementation errors. The easiest path to strong security, and a positive user experience, is to turn to the experts. The Okta OIDC SDK can help with this in many...
What's New with OAuth and OpenID Connect?

In this video you'll learn about the latest developments in the OAuth and OpenID Connect specs from Aaron Parecki, a regular contributor to the OAuth working group. The latest additions to the specs enable richer experiences and better security for applications using OAuth.
OpenID Connect Logout Options with Spring Boot

On the Okta blog, we spend much of our time talking about logging in. That is because once you configure your application to log in, the log out just works. But there are a few things you should consider when you’re thinking about your app’s logout configuration. In this post, I’ll walk through examples of the two logout options you have with Spring Security: the "default" session clearing logout, and relying party initiated logout. If...
Build Single Sign-on in Java
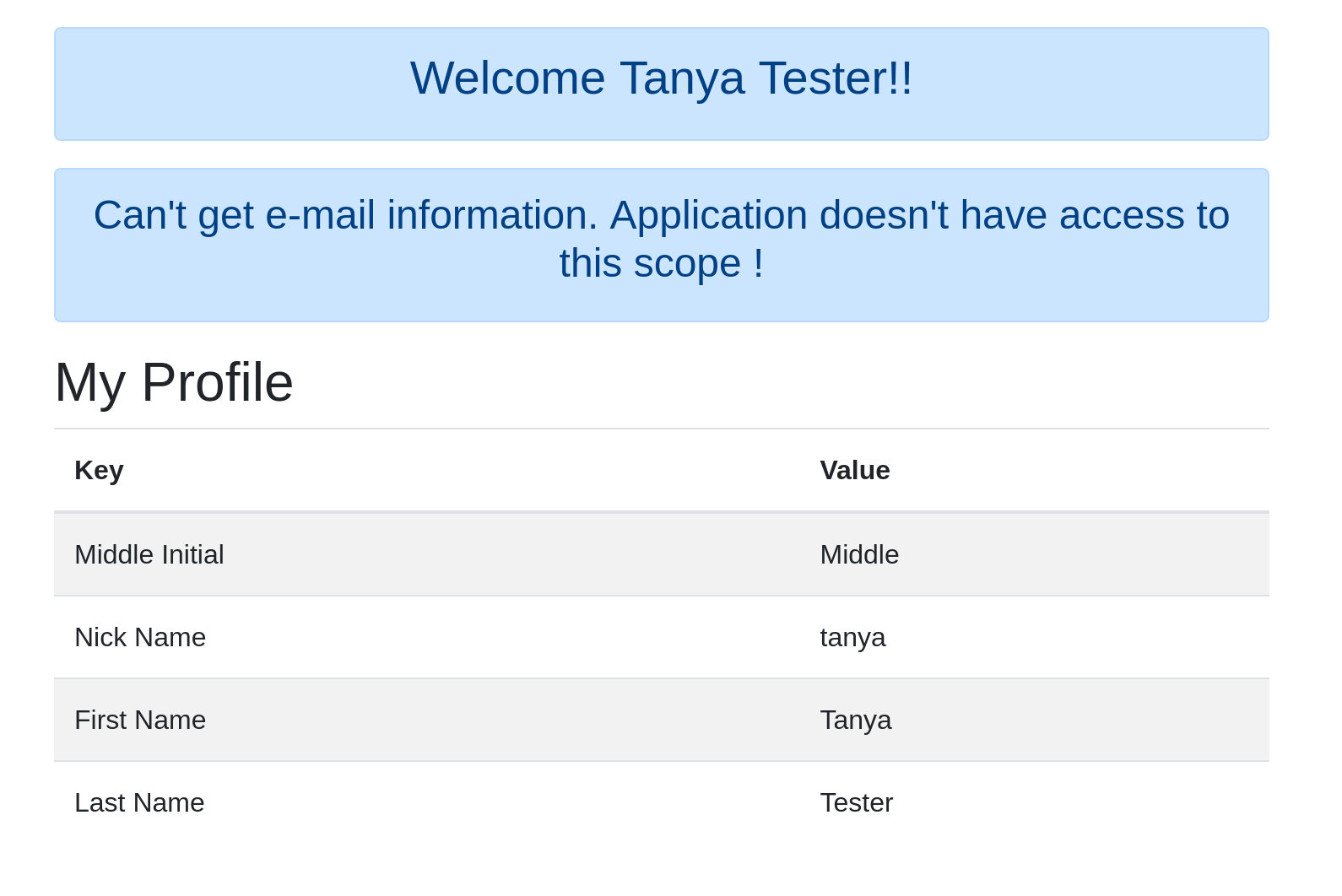
In modern app development, you quite frequently have a single resource server that provides data to multiple client applications. These applications may share a similar set of users, but need to enforce different permissions. For example, it’s possible that not all users of the first application should be allowed to access the second (think of, for example, an admin console application versus a client or user application). How would you implement this? One way to...
Use PKCE with OAuth 2.0 and Spring Boot for Better Security

Browser and mobile feature enhancements move fast. Often times, these technologies move faster than security standards designed to protect them can keep up. OAuth 2.0 offers the best and most mature standard for modern applications. However, there hasn’t been an official release of this standard since 2012. Eight years is a very long time in Internet technology years! That doesn’t mean that its contributors have been sitting idly by. There is active work on the...
Protecting a PHP API Using OAuth
REST APIs are a big part of today’s Internet. Some of the everyday use cases of REST APIs are: driving the backend of single-page Web applications/mobile applications integrating different applications to exchange data and automate workflows providing the communication channel for the different parts of a complex service-oriented architecture connecting IoT devices. REST API security is essential because an API can expose powerful, mission-critical, and outright dangerous functionality over the Internet. For example, a fintech...
Secure Legacy Apps with Spring Cloud Gateway
One of the biggest challenges of adding OAuth 2.0 support to legacy applications is a lack of support in the underlying framework. Maybe it’s homegrown, or maybe it’s just old? Either way, migrating away from an old form-based login doesn’t need to be so painful. In this post, I’ll walk you through a low-code option using Spring Cloud Gateway and Okta. You’ll learn how to setup Spring Cloud Gateway running as a stand-alone application that...
Build a Secure REST Application Using Jersey

REST is one of the most used architectural styles when it comes to developing web services. In Java, we have the JAX-RS specification that defines how to create a RESTful application. To show the power of the spec, Jersey, the reference implementation of JAX-RS was created. Building JAX-RS endpoints only requires adding annotations to your code. Keep reading to see how easy it is! In this tutorial you’ll create a TODO list service that will...
Add Docker to Your Spring Boot Application

Docker enables you to deploy a server environment in containers. A container is a standardized unit of software that assembles code, runtime, dependencies, settings, and initialization in a single package that you can run reliably from one computing environment to another. Deploying your app as a Docker container is not hard, and can alleviate a lot of problems that you may encounter when moving your app around the multiple environments it has to go, like...
Use Okta Token Hooks to Supercharge OpenID Connect

OpenID Connect (OIDC) and OAuth 2.0 are already recognized as powerful tools for incorporating authentication and authorization into modern web applications. Okta has enhanced the capabilities of these standards by introducing our Inline Hooks feature. There are a number of different types of inline hooks that Okta supports. In this post, I focus on hooks that allow you to patch information into the tokens you get back from Okta via OIDC and OAuth. You’ll first...
OAuth 2.1: How Many RFCs Does it Take to Change a Lightbulb?
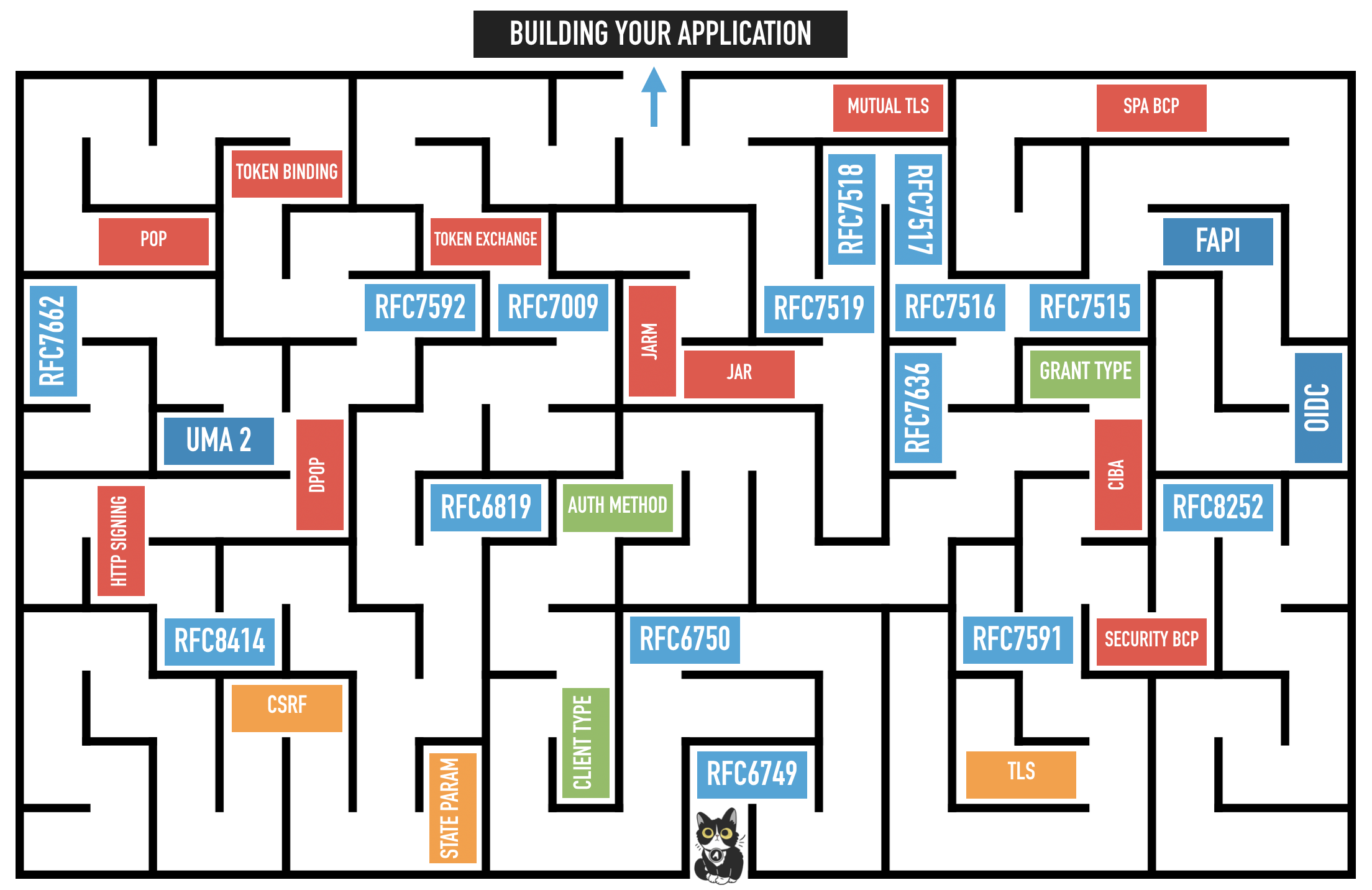
The OAuth working group agreed last month in Singapore (IETF 106) that work will begin to update the current OAuth 2.0 Framework to a potential version 2.1 encompassing all the latest recommendations and best practices around the specification. This is in part due to the maze of documentation that developers need to understand when getting started on the topic to choose the correct flow and implement the best security posture for their application landscape. By...
Deploy Your Spring Boot App the Right Way

Spring Boot is an awesome solution to speed up the development cycle of your app. Have an idea and want to transform it into a Spring Boot app, but don’t know the best way to deploy it? Look no further, we will help you out! There are plenty of options to deploy Spring Boot applications. In this article. we will cover three of them: Azure Amazon Web Services Self-hosted We will use a simple application...
A Quick Guide to Java on Netty

Netty is a non-blocking input/output (NIO) framework that makes it relatively simple to develop low-level network servers and clients. Netty provides an incredible amount of power for developers who need to work down on the socket level, for example when developing custom communication protocols between clients and servers. It supports SSL/TLS, has both blocking and non-blocking unified APIs, and a flexible threading model. It’s also fast and performant. Netty’s asynchronous, non-blocking I/O model is designed...
ASP.NET Core 3.0 MVC Secure Authentication

On September 23rd, Microsoft announced the third major release of its .NET Core framework. This new release boasts better performance, support for Windows Desktop apps, improved support for Docker containers, and more. Naturally, I was excited to see this new release and get authentication hooked into it with Okta! I put together this tutorial to demonstrate how to quickly and securely set up user management with Okta and OIDC (OpenID Connect) in an ASP.NET Core...
Simple, Secure Authentication with CodeIgniter

CodeIgniter is a simple, lightweight PHP framework that remains a popular option for many developers. It might lack the sophisticated architecture and advanced features of Symfony or Laravel, but it compensates with a small footprint and a shallow learning curve. In this tutorial, I will show you how to build a simple application for creating/viewing news items. We will extend the standard CodeIgniter tutorial to add user authentication to the application, require a logged-in user...
An Illustrated Guide to OAuth and OpenID Connect
In the “stone age” days of the Internet, sharing information between services was easy. You simply gave your username and password for one service to another so they could login to your account and grab whatever information they wanted! Yikes! You should never be required to share your username and password, your credentials, to another service. There’s no guarantee that an organization will keep your credentials safe, or guarantee their service won’t access more of...
Build a Simple CRUD App with Java and JSF

JavaServer Faces (JSF) is a Java framework for building Web applications, centered on components as the building blocks for the user interface. JSF benefits from a rich ecosystem of tools and vendors, as well as out of the box components and libraries that add even more power. Why use JSF instead of JavaServer Pages (JSP)? There are two primary reasons: First, JSF has more templating capabilities, since it doesn’t write your view directly as it...
Build a NodeJS App with TypeScript
As dynamically typed languages became prominent during the last decade, typeless (or should I say lawless?) programming became the norm for the backend as well as the frontend. Many people believe the simplicity of “just writing” code is efficient for providing a proof of concept or prototyping applications. However, as those applications grow, the typeless code used to build them often becomes incredibly convoluted and more difficult (some would say impossible) to manage. In the...
Build an Application with Spring Boot and Kotlin

In 2011, JetBrains, the company behind IntelliJ, decided to create a modern language that would run inside the Java Virtual Machine and address common concerns with Java at the time like its verbosity. This project became Kotlin, a quickly growing and popular language. Google then announced official support for Kotlin on Android, further accelerating its adoption. Many companies started to replace Java with Kotlin as their main language to take advantage of the new features...
Make Java Tests Groovy With Hamcrest

My favorite way to test Java code is with Groovy. Specifically, writing tests in Groovy with Hamcrest. In this post, I’ll walk through how to test a simple Spring Boot application with these tools. Groovy is an optionally typed dynamic language for the JVM, and can be compiled statically. That is a mouthful and I’ll explain this as we go, but for now think of Groovy as Java with lots of sugar. Groovy is a...
Easy Spring Boot Deployment with AWS Elastic Beanstalk

Nearly all applications rely on authentication. Developers, and the companies that employ them, want to confirm who is making the request and are they who they say they are. And, this needs to happen fast enough for a good user experience. Fortunately, there are great tools to help. Spring Boot with Spring Security is a fantastic solution for Java-based web development. With relatively little code, developers can implement, test, update, and expand authentication schemes easily...
Secure Your ASP.NET Core App with OAuth 2.0

Do you ever wish you had a virtual scrap of paper you could use to write notes in the cloud? I’ll show you how to build a simple ASP.NET Core app to keep track of your notes, plus how to use .NET Core’s OAuth 2 authentication middleware to secure access to your app so your personal notes are kept private. Note: In May 2025, the Okta Integrator Free Plan replaced Okta Developer Edition Accounts, and...
Build Mobile Apps with Angular, Ionic 4, and Spring Boot
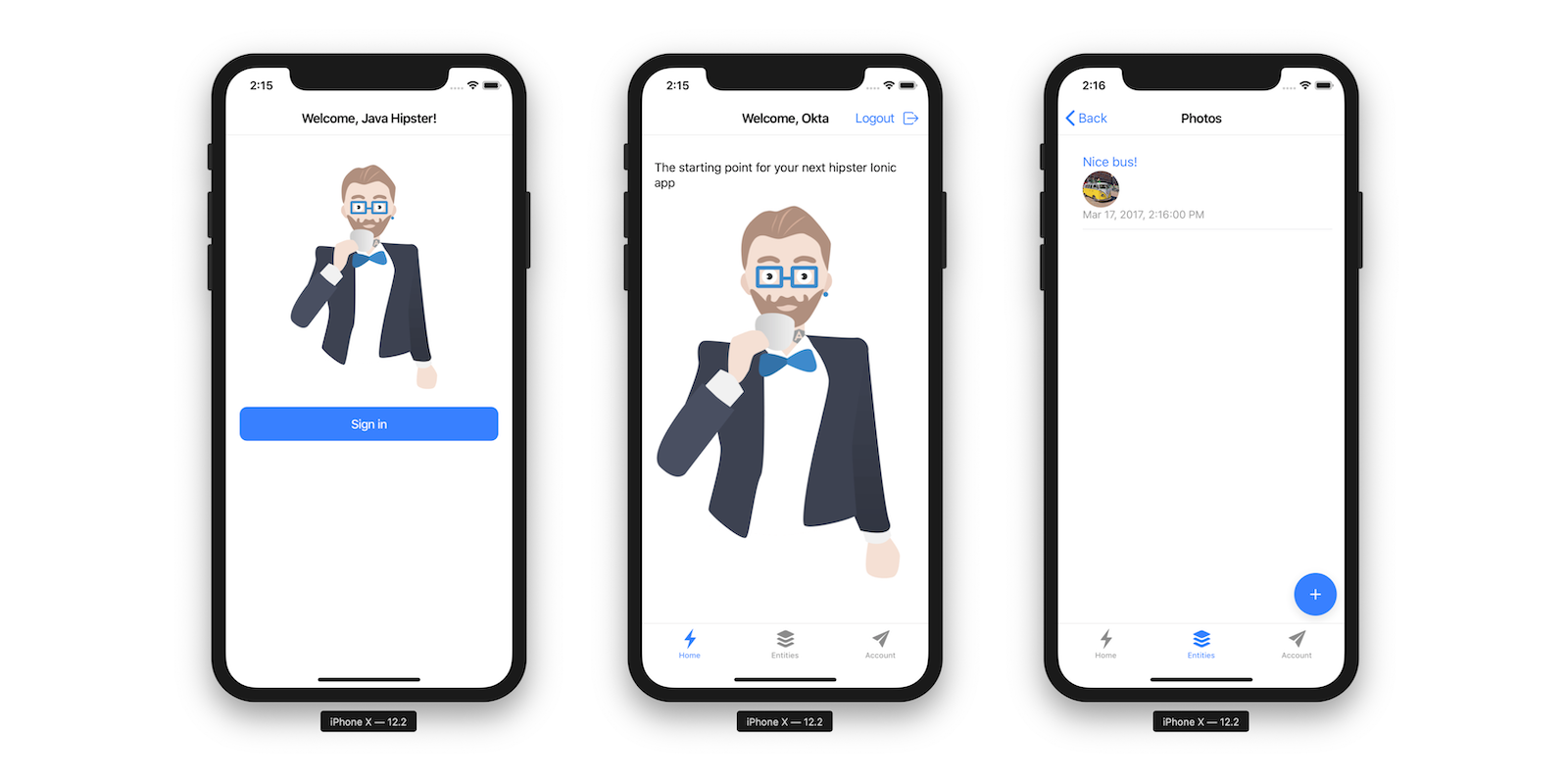
I’m a big fan of Ionic. I started using it several years ago when it was based on AngularJS. As a developer, I really liked it because I knew Angular. I found didn’t have to learn much more to be a productive developer with Ionic. What is Ionic? I’m glad you asked! Ionic is an open source project that allows you to build mobile apps using web tech. Technically, this is called a "hybrid" app...
7 Ways an OAuth Access Token is like a Hotel Key Card

What do OAuth 2.0 access tokens and hotel key cards have in common? It turns out quite a lot! A hotel key card is essentially a physical counterpart to an OAuth access token. You get a hotel key card by authenticating at the front desk At a hotel, you check in at the front desk, show your ID card, and then you get a key card that you can use to get into your hotel...
What the Heck is Sign In with Apple?

This week at Apple’s developer conference WWDC, Apple announced a new feature, “Sign In with Apple” enabling users to sign in to apps using their Apple ID. This new feature is positioned as a secure and privacy-friendly way for users to create an account in apps. Most iOS and Mac users already have an Apple ID, and this new feature lets them use that Apple ID to sign in to other apps and websites. If...
Token Authentication in PHP

JSON Web Tokens (JWTs) have turned into the de-facto standard for stateless authentication of mobile apps, single-page web applications, and machine-to-machine communication. They have mostly superseded the traditional authentication method (server-side sessions) because of some key benefits: They are decentralized and portable (you can request a token from a dedicated service, and then use it with multiple backends) There is no need for server-side sessions - a JWT can contain all the required information about...
Easy Single Sign-On with Spring Boot and OAuth 2.0

Single sign-on used to be the “Holy Grail” of enterprise size companies and was usually only available companies that could afford it. Nowadays, we take SSO as a matter of course. For instance, you would think it was completely weird (and unpleasant) if you logged into GMail and then had to log in again when you went to Google Docs. But, what about building custom applications for developers? SSO was still in the domain of...
Is the OAuth 2.0 Implicit Flow Dead?

You may have heard some buzz recently about the OAuth 2.0 Implicit flow. The OAuth Working Group has published some new guidance around the Implicit flow and JavaScript-based apps, specifically that the Implicit flow should no longer be used. In this post we’ll look at what’s changing with the Implicit flow and why. Note: In May 2025, the Okta Integrator Free Plan replaced Okta Developer Edition Accounts, and the Okta CLI was deprecated. We preserved...
Build a Simple REST API in PHP

REST APIs are the backbone of modern web development. Most web applications these days are developed as single-page applications on the frontend, connected to backend APIs written in various languages. There are many great frameworks that can help you build REST APIs quickly. Laravel/Lumen and Symfony’s API platform are the most often used examples in the PHP ecosystem. They provide great tools to process requests and generate JSON responses with the correct HTTP status codes....
Simple User Authentication in React

In 2019, it’s quite easy to find React components for pretty much everything. For example, if you want to add user authentication to your app, you can do so easily with Okta’s React component. Here I’ll walk you through creating a simple, fun React app that fetches random Chuck Norris jokes. I’ll then show you how you can add user authentication and customize your user experience, so the jokes will replace Chuck Norris’ name with...
Migrate Your Spring Boot App to the Latest and Greatest Spring Security and OAuth 2.0

Spring Boot 1.5.x made it easier than ever before to integrate Spring Security with OAuth 2.0 into your application. Spring Boot 2.1.x dials it up to 11 by making OpenID Connect a first class citizen in the stack. In this post, you start with Spring Boot 1.5.19 and Spring Security 4.2.x. You integrate it with Okta’s OAuth service. From there, you move onto Spring Boot 2.1.3 and Spring Security 5.1. You’ll see how integrating with...
Add the OAuth 2.0 Device Flow to any OAuth Server
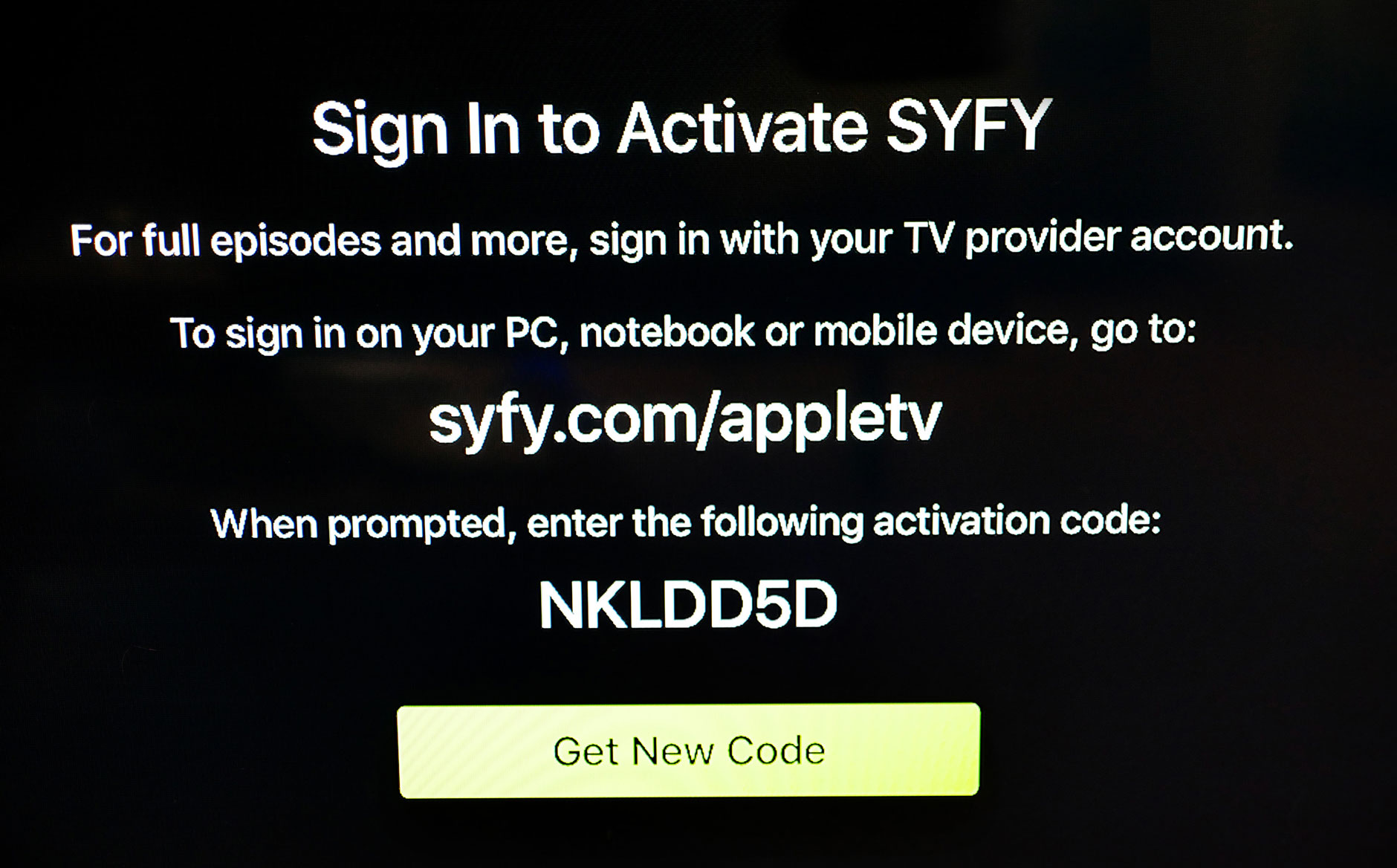
You may not have heard of the Device Flow before, but you’ve probably used it if you have an Apple TV, Roku or Amazon FireTV! The OAuth 2.0 Device Flow is used to log in to a device using OAuth when the device doesn’t have a browser, or also when the device has limited keyboard input ability. The Apple TV is a great device, but it’s missing a browser, which means it can’t do a...
Create and Verify JWTs in PHP with OAuth 2.0

JSON Web Tokens (JWTs) allow you to implement stateless authentication (without the use of server-side sessions). JWTs are digitally signed with a secret key and can contain various information about the user: identity, role, permissions, etc in JSON format. This information is simply encoded and not encrypted. However, because of the digital signature, the payload cannot be modified without access to the secret key. JWTs are a relatively hot topic as they are widely used...
Nobody Cares About OAuth or OpenID Connect

If you’re reading this post, there’s a good chance that you’re a web developer who’s very interested in web security. You’ve probably heard about OAuth or OpenID Connect (OIDC) before. You may have even used them at some point in your career. But here’s the thing: almost nobody actually cares about OAuth or OIDC. Not you, not me, and not even other developers in the security industry. To understand why nobody cares about these two...
Why OAuth API Keys and Secrets Aren't Safe in Mobile Apps

It’s pretty common for mobile apps to access backend API services to fetch data. It’s also pretty common for APIs to require secret keys in order to access them. So how do you securely include API keys in a mobile app? Well, the short answer is you don’t. The long answer is the rest of this blog post. Let’s take a look at two ways it’s possible to hack secret API keys out of mobile...
OAuth 2.0 for Native and Mobile Apps

These days, when you hear someone talking about OAuth, it is likely they mean OAuth 2.0. Previous versions of the standard are deprecated. OAuth is an authorization framework that enables you to work with external systems in a secure way using digital identifiers called tokens. One type of token is called an access token. Its function is to allow you to exercise APIs securely. The API service can use the access token to determine if...
Build and Test a React Native App with TypeScript and OAuth 2.0

React Native is one of the most popular ways of creating mobile apps. Building on the success of React, it ties together native components for both Android and iOS using a shared JavaScript code-base. However, JavaScript has come under fire recently for not being type safe which can lead to a loss of developer trust. Enter TypeScript, which allows type annotations to be added to existing JavaScript code. One requirement of many mobile apps is...
Build a Single-Page App with Go and Vue
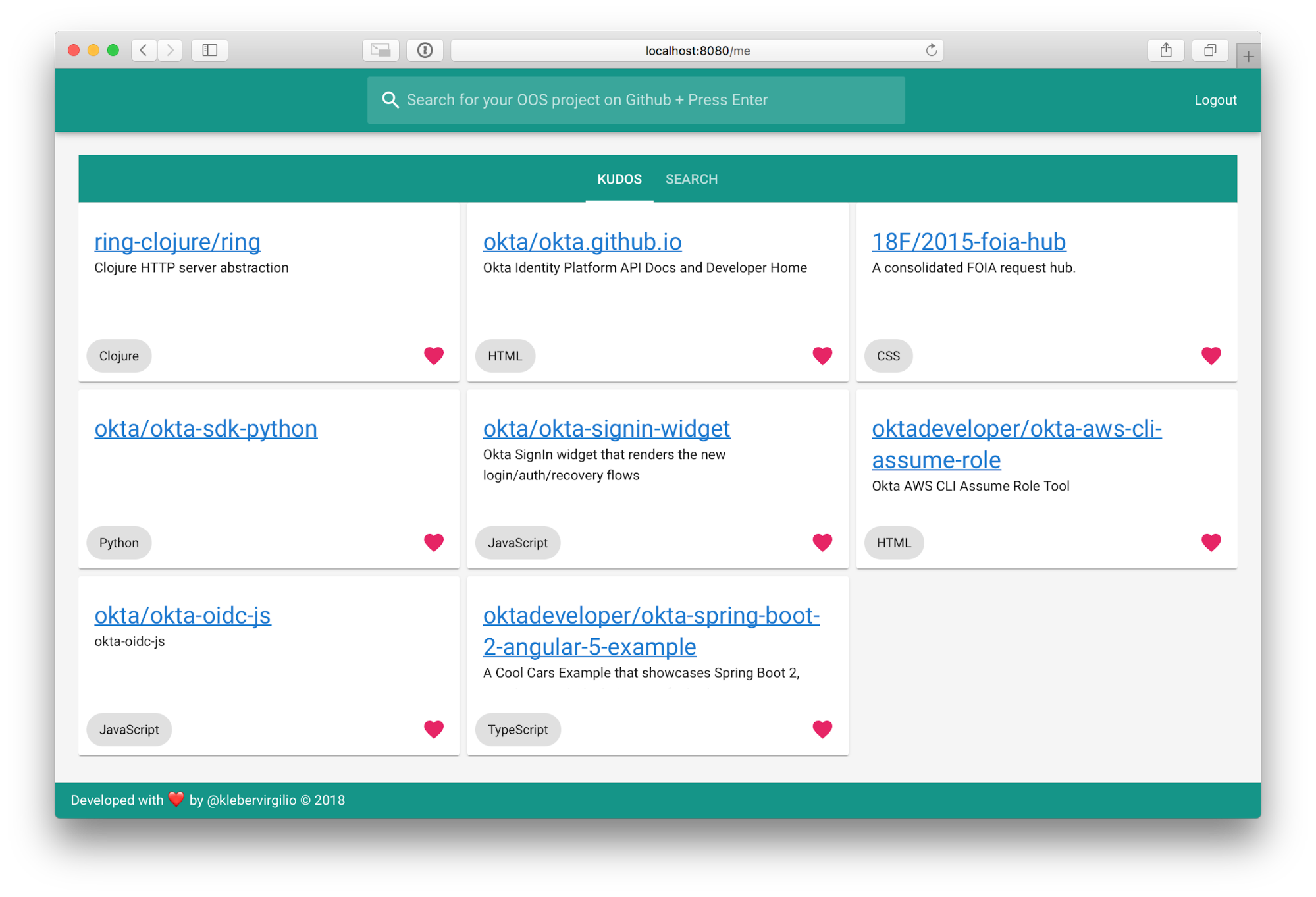
Single-Page Applications (SPAs) improve user experience by offering rich UI interactions, fast feedback, and the relief of knowing you don’t need to download and install a traditional application. Browsers are now operating systems and websites are apps. While a SPA isn’t always the answer, for apps that rely on snappy user interaction they are increasingly common. To the end user, a well-designed SPA feels like rainbows and unicorns. From the developer perspective, reality can often...
Stolen Access Tokens and You

What never dies, spreads rampantly, and is guaranteed to bite you? You guessed it: Stolen access tokens! In recent weeks, we’ve seen a number of hacks around OAuth access tokens. As much as we’d like to blame the underlying technology, it’s more out of misuse and misunderstanding than anything else. No matter who it is, the outbreak is the same: A website uses OAuth with little to no granularity in scopes The website issues an...
Build a Desktop App with Electron and Authentication

Electron is a framework for building cross-platform desktop applications with web technologies like JavaScript, HTML, and CSS. It was created for GitHub’s Atom editor and has achieved widespread adoption since. Electron powers several apps that I use on a daily basis: Slack, Kitematic, and Visual Studio Code to name a few. Electron 2.0 was released in early May 2018, along with changes to the project to adhere to strict semantic versioning. This is good news...
Build a Basic CRUD App in Android with Kotlin
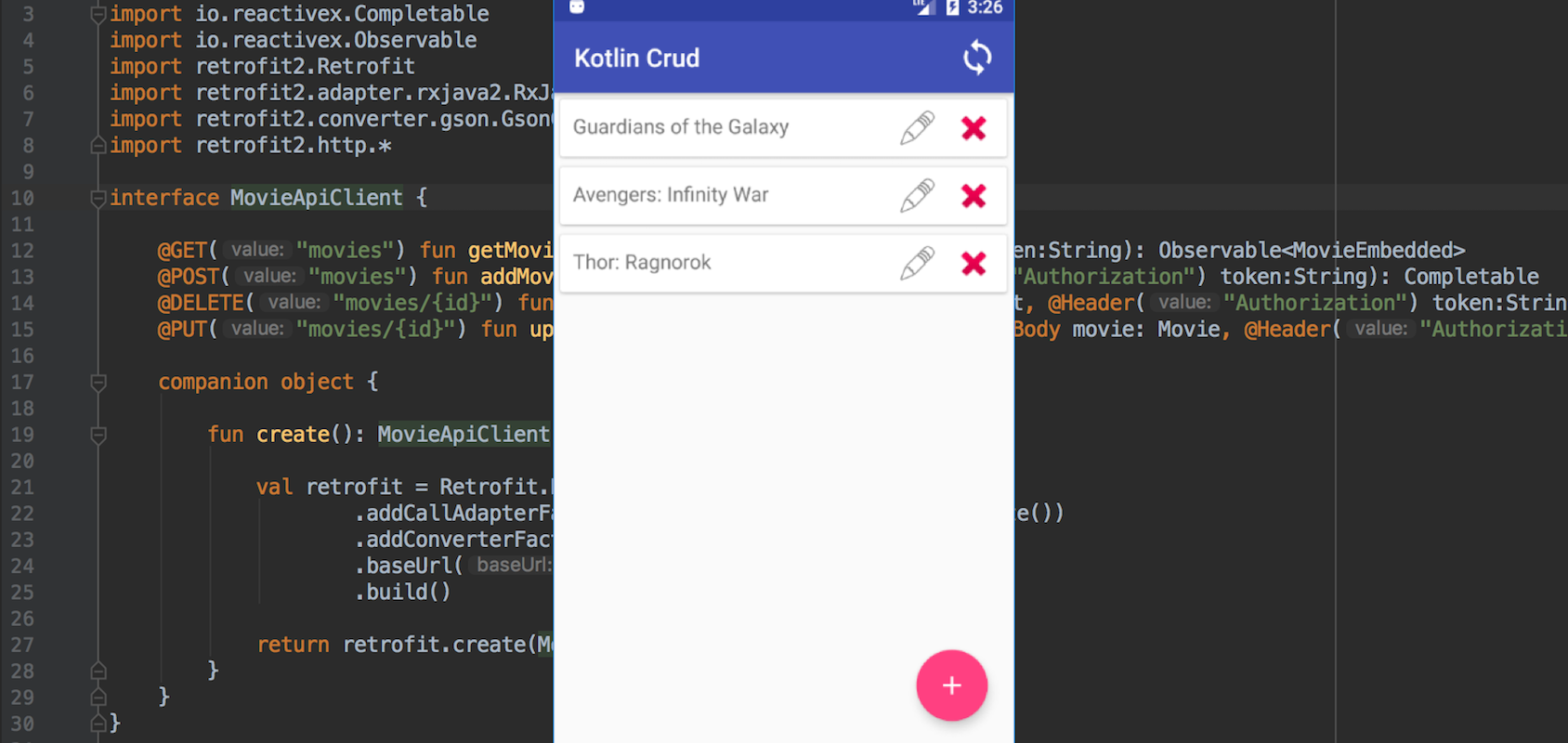
Kotlin was recently given official Android support status by Google, but it remains difficult to understand for many developers. The best way to start is by creating a complete app yourself, which you’ll do in this tutorial. In this tutorial, you’ll use Spring Boot for the API that powers your Android (+ Kotlin) mobile app. Spring Boot is a great way to create a robust REST API with a minimal amount of code. I’m going...
Use nginx to Add Authentication to Any Application

Ever found yourself wanting to put an application behind a login form, but dreading writing all that code to deal with OAuth 2.0 or passwords? In this tutorial, I’ll show you how to use the nginx auth_request module to protect any application running behind your nginx server with OAuth 2.0, without writing any code! Vouch, a microservice written in Go, handles the OAuth dance to any number of different auth providers so you don’t have...
Build a Secure API with Spring Boot and GraphQL

GraphQL is a data query language developed by Facebook in 2012 to solve a shortcoming of REST APIs and traditional database models. All too often, when programmers write REST API data queries, they default to retrieving entire data structures when they need only a part of it. For example, if you want to find out the number of comments on a blog post, a developer might typically retrieve the entire post and all associated fields...
OAuth 2.0 from the Command Line
So you’ve found yourself writing a command line script and needing to talk to an API that uses OAuth 2.0? The typical approaches to getting an OAuth access token from a command line script usually involve copying and pasting the authorization code into the terminal. But we can do better! In this tutorial, I’ll show you how to write a command line script which is able to complete the OAuth exchange all without any copying...
Add Authentication to your PHP App in 5 Minutes
Have you ever found yourself building an app and needing to add authentication, dreading the thought of setting up yet another username and password database? In this post, I’ll show you how easy it is to use Okta to add authentication to a simple PHP app in 5 minutes. By leveraging Okta’s simple OAuth API, we can breeze past most of the challenges involved in authenticating users by letting Okta take care of the hard...
Secure Your API with OAuth, Mulesoft, and Okta in 20 Minutes
If you’re building or managing an API, you’re probably using an API gateway to help you manage it. Hopefully, you’re also using OAuth and an identity provider (IdP) like Okta to secure your API through the gateway. Maybe you’ve also discovered that getting the “OAuth dance” working properly among the gateway, IdP, and application can be tricky. I’ve worked with a lot of different API gateways and want to provide some guidance and tools to...
What is the OAuth 2.0 Password Grant Type?
The OAuth 2.0 Password Grant Type is a way to get an access token given a username and password. It’s typically used only by a service’s own mobile apps and is not usually made available to third party developers. Update: The password grant type is prohibited in the latest OAuth 2.0 Security Best Current Practice. Please see oauth.net for additional information. This post is the third in a series where we explore frequently used OAuth...
How to Securely Manage Users in Your Node App
If you’re building a non-trivial website, chances are you’ll want some way to keep track of users. This can be quite complex and require a good deal of infrastructure, but one of the most secure and scalable ways is also one of the easiest. Using an OAuth 2.0 provider allows you to offload these tasks to an external provider, making your life as a developer so much simpler. When using an OAuth provider, it’s simple...
Build a Photo Gallery PWA with React, Spring Boot, and JHipster

At its core, React is just a UI toolkit, ala GWT, but it has a very healthy ecosystem around it that provides everything you need to build a kick-ass progressive web app (PWA). PWAs are cool because if they’re done right, they can offer a native-like experience for your users, allowing them to install your app, and use it when it’s offline. But, “why React?” is what you’re probably asking yourself right now, right? Well,...
Deploy Your Secure Spring Boot + Angular PWA as a Single Artifact
I’ve written several posts on this blog that show you how to develop an Angular SPA (single-page application) that talks to a Spring Boot API. In almost all of them, I’ve used OAuth 2.0’s implicit flow and built, tested, and deployed them as separate applications. IMHO, this is the way many applications (outside of the Java world) are built and deployed. What if you could combine the two applications for production, and still get all...
What is the OAuth 2.0 Implicit Grant Type?
The Implicit Grant Type is a way for a single-page JavaScript app to get an access token without an intermediate code exchange step. It was originally created for use by JavaScript apps (which don’t have a way to safely store secrets) but is only recommended in specific situations. This post is the second in a series where we explore frequently used OAuth 2.0 grant types. Previously we covered the Authorization Code grant type. If you...
Build and Secure Microservices with Spring Boot 2.0 and OAuth 2.0
Spring Boot has experienced massive adoption over the last several years. For Spring users, it offers a breath of fresh air, where they don’t have to worry about how things are configured if they’re comfortable with defaults. The Spring Boot ecosystem is filled with a wealth of what they call starters. Starters are bundles of dependencies that autoconfigure themselves to work as a developer might expect. Spring Boot allows you to create standalone web apps,...
What is the OAuth 2.0 Authorization Code Grant Type?
The Authorization Code Grant Type is probably the most common of the OAuth 2.0 grant types that you’ll encounter. It is used by both web apps and native apps to get an access token after a user authorizes an app. This post is the first part of a series where we explore frequently used OAuth 2.0 grant types. If you want to back up a bit and learn more about OAuth 2.0 before we dive...
Secure Server-to-Server Communication with Spring Boot and OAuth 2.0
Most OAuth 2.0 guides are focused around the context of a user, i.e., login to an application using Google, GitHub, Okta, etc., then do something on behalf of that user. While useful, these guides ignore server-to-server communication where there is no user and you only have one service connecting to another one. The OAuth 2 client credentials grant type is exclusively used for scenarios in which no user exists (CRON jobs, scheduled tasks, other data...
Hello, Okta!
My name is Aaron Parecki, and last week I joined Okta on the Developer Advocacy team. I’ve been working with Okta since 2016 when we published the online version of my book, OAuth 2.0 Simplified, on oauth.com. In 2017, I worked with the team again on producing the print version, which we released at Okta’s conference in Las Vegas last fall. In 2016, Okta was focused on the enterprise IT market, providing a much-needed single-sign-on...
Token Authentication in ASP.NET Core 2.0 - A Complete Guide

Token authentication has been a popular topic for the past few years, especially as mobile and JavaScript apps have continued to gain mindshare. Widespread adoption of token-based standards like OAuth 2.0 and OpenID Connect have introduced even more developers to tokens, but the best practices aren’t always clear. I spend a lot of time in the ASP.NET Core world and have been working with the framework since the pre-1.0 days. ASP.NET Core 2.0 has great...
Add Single Sign-on to Your Dropwizard Server in 15 Minutes
Dropwizard is recognized as the pioneer in turn-key Java API frameworks, and rivals Spring Boot for ease of adoption. Whether you’re interested in trying it out for the first time, or already have a mature platform built on top of Dropwizard, you can add secure authentication to your site in a matter of minutes. By combining Dropwizard’s production-ready essential libraries and Okta’s identity platform, you can construct a fully secured internet-facing web service with little...
Build a React Native Application and Authenticate with OAuth 2.0

With Okta and OpenID Connect (OIDC) you can easily integrate authentication into a React Native application and never have to build it yourself again. OIDC allows you to authenticate directly against the Okta API, and this article shows you how to do just that in a React Native application. Today you’ll see how to log a user into your React Native application using an OIDC redirect via the AppAuth library. React Native is a pretty...
Develop a Microservices Architecture with OAuth 2.0 and JHipster
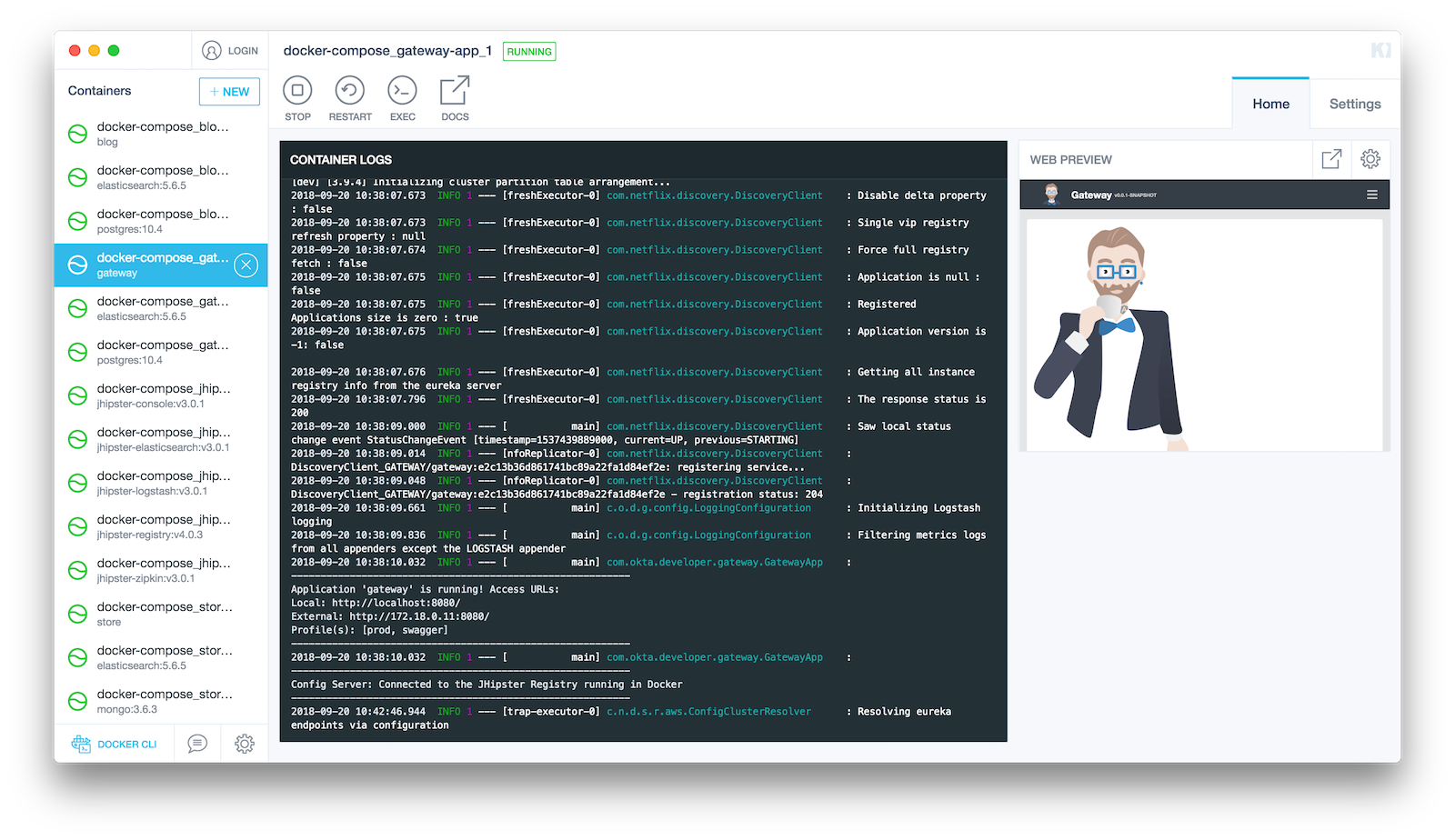
JHipster is a development platform to generate, develop, and deploy Spring Boot + Angular web applications and Spring microservices. It supports using many types of authentication: JWT, session-based, and OAuth 2.0. In its 5.0 release, it added React as a UI option. In addition to having two popular UI frameworks, JHipster also has modules that support generating mobile applications. If you like Ionic, which currently leverages Angular, you can use Ionic for JHipster. If you’re...
Build User Registration with Node, React, and Okta
Today’s internet users expect a personalized experience. Developers must learn to develop websites that provide that personalized experience while keeping their user’s information private. Modern web applications also tend to have a server-side API and a client-side user interface. it can be challenging to get make both ends aware of the currently logged in user. In this tutorial, I will walk you through setting up a Node API that feeds a React UI, and build...
How to Secure Your .NET Web API with Token Authentication

API security can be complex. In many cases, just because you’ve built an API that you want to make public, it doesn’t mean that you want just anybody accessing it. In most cases, you want fine-grained control over who can access the API, but setting up that kind of user management can be a daunting task: you’d have to create your own authorization service that can create API credentials for your users and have the...
Use Ionic for JHipster to Create Mobile Apps with OIDC Authentication
We 💙 Ionic, JHipster, and Java here at Okta. Ionic is a framework for building native mobile apps using web technologies. Technically, this is called a “hybrid” app because it’s not using native SDKs. Hybrid mobile apps are distributed just like native apps: they can be installed on mobile devices, and they’re listed in app stores. As an end user, there’s a good chance you can’t tell the difference between a hybrid mobile app and...
Add Single Sign-On to Your Vert.x Server with Okta
Vert.x has continued to gain traction as a contender to the Spring ecosystem, largely due to improved performance and its polyglot accessibility. Fortunately, securing a Vert.x server with industry-leading authentication and authorization is almost as quick and easy as it is in Spring! In just a few minutes, you can have secure single sign-on guarding your server and giving you access to a wealth of information about your users. This tutorial will walk you through...
Build an iOS App with Secure Authentication in 20 Minutes
What does it take to build a successful mobile application in today’s ever-changing market? There are (what seems like an infinite) number of design, build, and test cycles performed, just to release your app into the hands of a user. In essence: while Users.love != true { Product.design() Product.rebuild() } Once completed, the real challenge begins – retaining those users. Mostly that means getting users to log in to your app easily, and then never...
Add Single Sign-On to Your Spring Boot Web App in 15 Minutes
Need a secure web server right now? With Spring Boot and Okta, you can spin up an enterprise-quality REST server with complete user identity and authorization management in less than 20 minutes. Out of the box, Spring Boot and its Starter packages supply a near instant production-ready Tomcat server, and Okta hardens your APIs with a variety of OAuth flows just as fast. This tutorial will walk you through the complete process. The cherry on...
Add Authentication to Play Framework with OIDC and Okta
I’ve fallen in love with Play Framework in the past, but then found a more attractive framework in Spring Boot. I fell in love partly because Play was new and sexy at the time, but also because it’s “live reloading” of Java code was a killer feature I’d been looking for. When it added support for Scala in v2.0, I was very excited to learn Scala and discover the power of functional programming. Part of...
Secure your SPA with Spring Boot and OAuth
If you have a JavaScript single-page application (SPA) that needs to securely access resources from a Spring Boot application, you likely want to use the OAuth 2.0 implicit flow! With this flow your client will send a bearer token with each request and your server side application will verify the token with an Identity Provider (IdP). This allows your resource server to trust that your client is authorized to make the request. In OAuth terms...
Play Zork, Learn OAuth
In the early ’80s, some of the best “video” games were text-based adventures. These games would print out descriptive text of your surroundings and you would interact with the game using simple, but natural language commands like: “go north” or “take sword”. Fast forward some 30 years and a specification for an authorization framework called OAuth 2.0 was published. This framework allows an application to receive a token from an external party (like Okta) that...
Use OpenID Connect Support with JHipster
Single sign-on (SSO) is a feature that most developers don’t care about when building one-off applications for clients or themselves. However, when developing apps for their company, which will be used by employees of their business, they often need to hook into an existing identity provider. It might be Active Directory (AD), LDAP, or a myriad of other systems. Okta provides SSO for many companies around the world and allows them to configure AD and...
Add Role-Based Access Control to Your App with Spring Security and Thymeleaf
User management functions are required by a wide variety of apps and APIs, and it’s a common use-case to partition access to parts of an application according to roles assigned to a user. This is the basis of role-based access control (RBAC). Okta manages these roles with groups. Users can belong to one or more groups. With the Okta Spring Security integration, these groups are automatically mapped to roles that can be called out in...
What's in a Token? – An OpenID Connect Primer, Part 3 of 3
In the previous two installments of this OpenID Connect (OIDC) series, we dug deep into the OIDC flow types and saw OIDC in action using a playground found at: https://okta-oidc-fun.herokuapp.com/. In this third and final installment, we’ll look at what’s encoded into the various types of tokens and how to control what gets put in them. JWTs, have the benefit of being able to carry information in them. With this information available to your app...
OIDC in Action – An OpenID Connect Primer, Part 2 of 3
In the first installment of this OpenID Connect (OIDC) series, we looked at some OIDC basics, its history, and the various flow types, scopes, and tokens involved. In this post, we’ll dive into the mechanics of OIDC and see the various flows in action. The token(s) you get back from an OIDC flow and the contents of the /userinfo endpoint are a function of the flow type and scopes requested. You can see this live...
Identity, Claims, & Tokens – An OpenID Connect Primer, Part 1 of 3
In the beginning, there were proprietary approaches to working with external identity providers for authentication and authorization. Then came SAML (Security Assertion Markup Language) – an open standard using XML as its message exchange type. Then, there was OAuth and OAuth 2.0 – also open as well as being a modern, RESTful approach to authorization using JSON as its medium. And now, the holy grail of “secure delegated access” OpenID Connect (henceforth OIDC), which runs...
What the Heck is OAuth?
There’s a lot of confusion around what OAuth actually is. Some people think OAuth is a login flow (like when you sign into an application with Google Login), and some people think of OAuth as a “security thing”, and don’t really know much more than that. I’m going to show you what OAuth is, explain how it works, and hopefully leave you with a sense of how and where OAuth can benefit your application. What...
Get Started with Spring Boot, OAuth 2.0, and Okta
If you’re building a Spring Boot application, you’ll eventually need to add user authentication. You can do this with OAuth 2.0 (henceforth: OAuth). OAuth is a standard that applications can use to provide client applications with “secure delegated access”. It works over HTTP and authorizes devices, APIs, servers, and applications with access tokens rather than credentials. Very simply, OAuth is a protocol that supports authorization workflows. It gives you a way to ensure that a...
REST Service Authorization with JWTs
Many companies are adopting micro-services based architectures to promote decoupling and separation of concerns in their applications. One inherent challenge with breaking applications up into small services is that now each service needs to deal with authenticating and authorizing requests made to it. Json Web Tokens (JWTs) offer a clean solution to this problem along with TLS client authentication lower down in the stack. Wils Dawson and I presented these topics to the Java User...
Demystifying OAuth
It seems that OAuth 2.0 is everywhere these days. Whether you are building a hot new single page web application (SPA), a native mobile experience, or just trying to integrate with the API economy, you can’t go far without running into the popular authorization framework for REST/APIs and social authentication. During Oktane15, Karl McGuinness, our Senior Director of Identity, demystified the powerful, yet often misunderstood, world of OAuth 2.0 and shared details on Okta’s growing...