Articles tagged security
Elevate Access Token Security by Demonstrating Proof-of-Possession

We use access tokens to request data and perform actions within our software systems. The client application sends a bearer token to the resource server. The resource server checks the validity of the access token before acting upon the HTTP request. What happens if the requesting party is malicious, steals your token, and makes a fraudulent API call? Would the resource server honor the HTTP request? If you use a bearer token, the answer is...
Join Us for Developer Day 2023
We’re thrilled to bring back Developer Day in 2023! Developer Day is an event for developers designed by developers. This year we’re happy to announce this event is a free, two-day virtual event, so you can join us wherever you are! The event focuses on using identity to power secure applications, so join us to create a safer world for your application users. Check out more in this teaser video Developer Day 2023 event Authentication...
A Secure and Themed Sign-in Page

Creating secure applications requires authentication. Delegating all the tedious details of the sign-in process to Okta is the most secure method to authenticate, not to mention speedier for development. So you’ll see us advocating for and using the Okta-hosted sign-in page in our blog posts. But the default sign-in page can look too different from the personality you have in your application. And the login URL redirects to a domain outside your application, which is...
Protect Your Angular App From Cross-Site Scripting

In the last post of this SPA security series, we covered Cross-Site Request Forgery (CSRF) and how Angular helps you with a mitigation technique. Posts in the SPA web security series 1. Defend Your SPA From Security Woes 2. Defend Your SPA From Common Web Attacks 3. Protect Your Angular App From Cross-Site Request Forgery 4. Protect Your Angular App From Cross-Site Scripting Next, we’ll dive into Cross-Site Scripting (XSS) and look at the built-in...
Protect Your Angular App From Cross-Site Request Forgery

Previously, I wrote about web security at a high level and the framework-agnostic ways to increase safety and mitigate vulnerabilities. Posts in the SPA web security series 1. Defend Your SPA from Security Woes 2. Defend Your SPA from Common Web Attacks 3. Protect Your Angular App From Cross-Site Request Forgery 4. Protect Your Angular App From Cross-Site Scripting Now, I want to dive a little deeper into the vulnerabilities. In this short post, we’ll...
Defend Your SPA from Common Web Attacks

This is the second post in a series about web security for SPAs. In the last post, we laid the groundwork for thinking about web security and applying security mechanisms to our application stack. We covered the OWASP Top Ten, using secure data communication with SSL/TLS, using security headers to help enhance built-in browser mechanisms, keeping dependencies updated, and safeguarding cookies. Posts in the SPA web security series 1. Defend Your SPA from Security Woes...
Defend Your SPA from Security Woes

There’s a lot of information floating out there about web security. But when I read through the material, I noticed some information wasn’t up to date, or it was written specifically for traditional server-rendered web applications, or the author recommended anti-patterns. In a series of posts, I will cover web security concerns that all web devs should be aware of, emphasizing client-side applications, namely Single Page Applications (SPAs). Furthermore, I’m not going to get into...
OAuth for Java Developers

You can use OAuth to secure apps, APIs, and devices. OAuth has become increasingly popular, especially as developers are asked to knit together hundreds of apps and thousands of users in enterprise environments. The Java ecosystem is vast, with over 10 million developers worldwide and an abundance of IDEs, build tools, libraries, and frameworks to make them more productive. The infographic below is recommended as a starting point for Java developers. It’s designed to help...
The Identity of OAuth Public Clients

I recently got back from a series of events filled with lots of interesting discussions around various OAuth-related topics. At the official IETF meeting in Vienna back in March, I presented the latest work on OAuth 2.1 and we discussed and made progress on some of the current open issues. At the OAuth Security Workshop a few weeks later, I presented a session on client authentication for mobile apps, and there were many more presentations...
The Benefits of GDPR for Application Security

As the internet has grown, so has the need to protect users from privacy invasions, fraud, or other types of abuse by attackers. The European Union’s solution is the General Data Protection Regulation, or GDPR. First put into effect in 2018, the policy applies not only to the organizations in the EU but to any organization that uses or collects data from people in the EU. If your organization is subject to GDPR, you’ll need...
Does Java 18 finally have a better alternative to JNI?
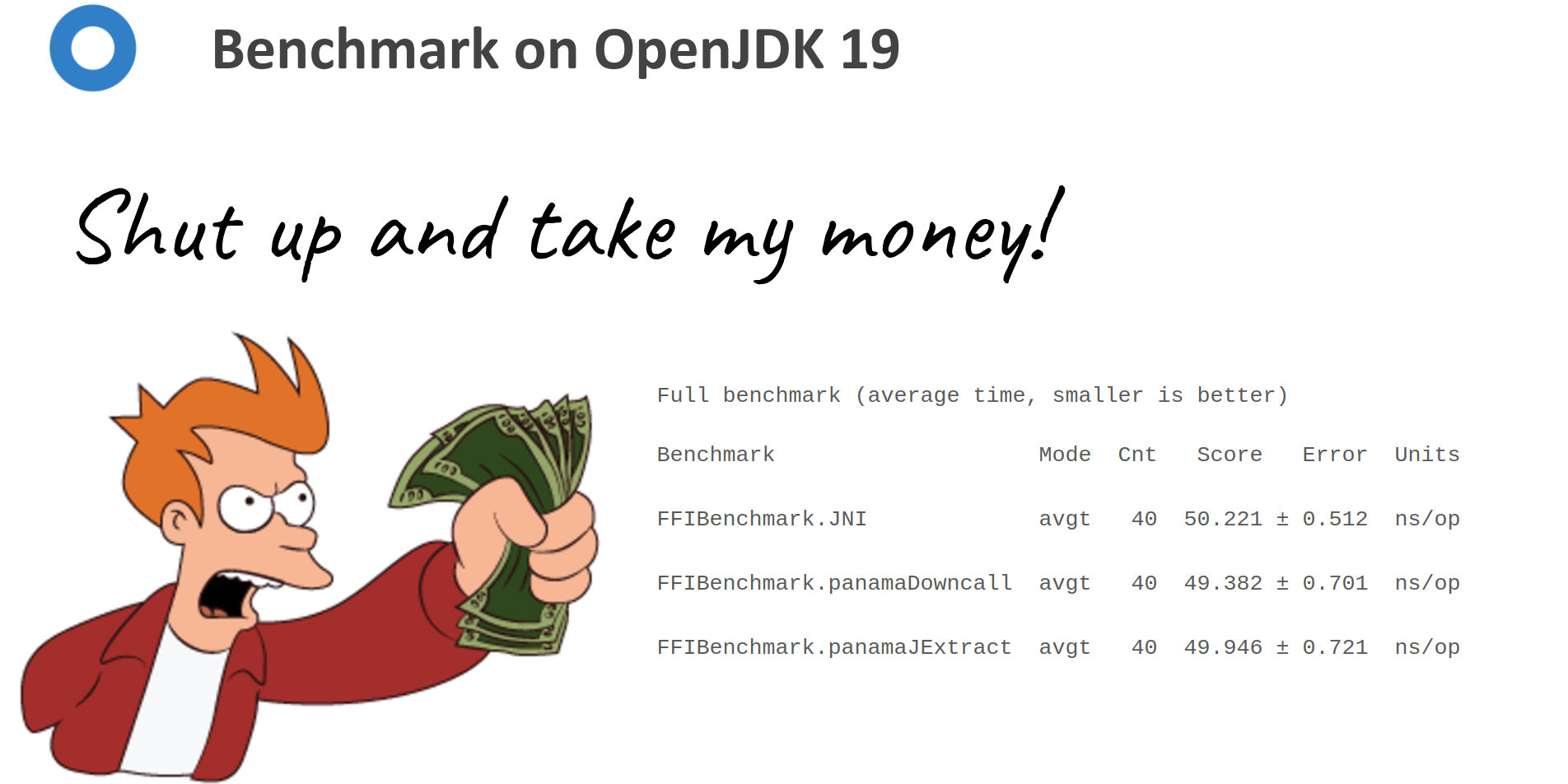
Java 18 was released last month (March 2022), and with it comes the second incubator of the Foreign Function & Memory API, so let us look at the state of Foreign Function Interface (FFI) in Java. Table of Contents What is a Foreign Function Interface? Why is Foreign Function Interface needed? A brief history of FFI in Java Java Native Interface (JNI) Java Native Access (JNA) Java Native Runtime (JNR) Enter Project Panama Foreign-Memory Access...
Why Safe Programming Matters and Why a Language Like Rust Matters

As programmers, how many of you have a good understanding of programming safety or secure programming? It’s not the same as application security or cyber security. I have to confess; I didn’t know a lot about these in the early years of my career, especially since I didn’t come from a computer science background. But looking back, I think programming security is something every programmer should be aware of and should be taught at a...
A Comparison of Cookies and Tokens for Secure Authentication

Access control in websites and web applications is a top priority for security, but how you set up access depends on how you store the data to be authenticated. This, in turn, enables user authorization. Cookies and tokens are two common ways of setting up authentication. Cookies are chunks of data created by the server and sent to the client for communication purposes. Tokens, usually referring to JSON Web Tokens (JWTs), are signed credentials encoded...
Three Ways to Run Your Java Locally with HTTPS

If you’re developing a web application, chances are you want your dev environment as close to production as possible. One of the often-overlooked differences between local development and production servers is the use of Transport Layer Security (TLS), or Hypertext Transfer Protocol Secure (HTTPS). In this post, I’ll cover three different options to get your local Java app running with TLS in no time! Table of Contents Start with a simple Java application HTTPS using...
Containerless! How to Run WebAssembly Workloads on Kubernetes with Rust

WebAssembly (Wasm) is one of the most exciting and underestimated software technologies invented in recent times. It’s a binary instruction format for a stack-based virtual machine that aims to execute at native speeds with a memory-safe and secure sandbox. Wasm is portable, cross-platform, and language-agnostic—designed as a compilation target for languages. Though originally part of the open web platform, it has found use cases beyond the web. WebAssembly is now used in browsers, Node.js, Deno,...
Boost Your Productivity Using Okta CLI with Fig

CLIs are great. I love the speed and productivity increases I get when using a CLI, but memorizing commands – especially when commands need arguments, options, flags, and so on – can be daunting. Luckily, there are tools available for CLI fans out there, and one tool I’ve been enjoying is Fig. Fig powers up your CLI productivity Fig adds autocompletion to supported terminals, which makes using CLIs so much easier. Using Git? You’ll see...
What We Learned About Game Security at PAX West 2021
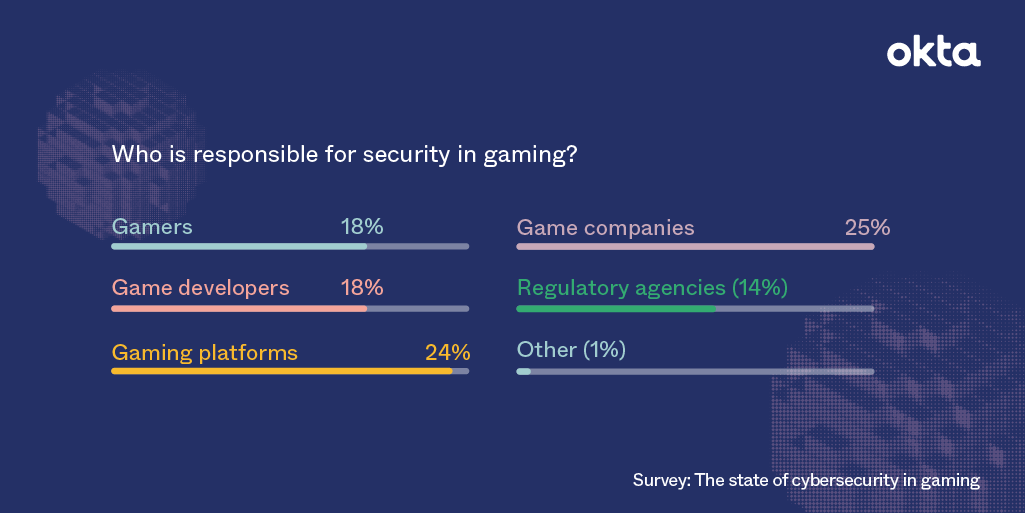
When it comes to security, there seems to be a disconnect in gaming. Where other industries have embraced an all-for-one and one-for-all approach to combating security threats, most gaming and entertainment companies seem largely happy to go it alone. This isn’t just conjecture. At Okta, we were curious about how developers and gaming companies approached security, so this past autumn we decided to take advantage of the return of PAX West, Penny Arcade’s iconic gaming...
Five Anti-Patterns with Secrets in Java

Most applications require some sort of secret or password to enable access: database connection info, API keys, OAuth client secrets, and JWT keys, to list some examples. Dealing with secrets in your projects is always a chore, and it’s often done wrong. In this post, I’ll describe five common problems, which you can think of as anti-patterns (the opposite of a best practice) and I’ll offer suggestions to help you avoid these issues. Table of...
Native SSO: Desktop and Mobile Apps Single Sign-On

When you hear SSO (Single Sign-On), you probably immediately think of web apps, and how you only need to sign into one web app first, then all other web apps give you seamless access. Unfortunately, for desktop and mobile applications (often referred to as “native apps”), the seamless web SSO experience (also referred to as native SSO) has not caught on. This is partly due to the lack of an industry standard or best practice...
The Things to Keep in Mind about Auth
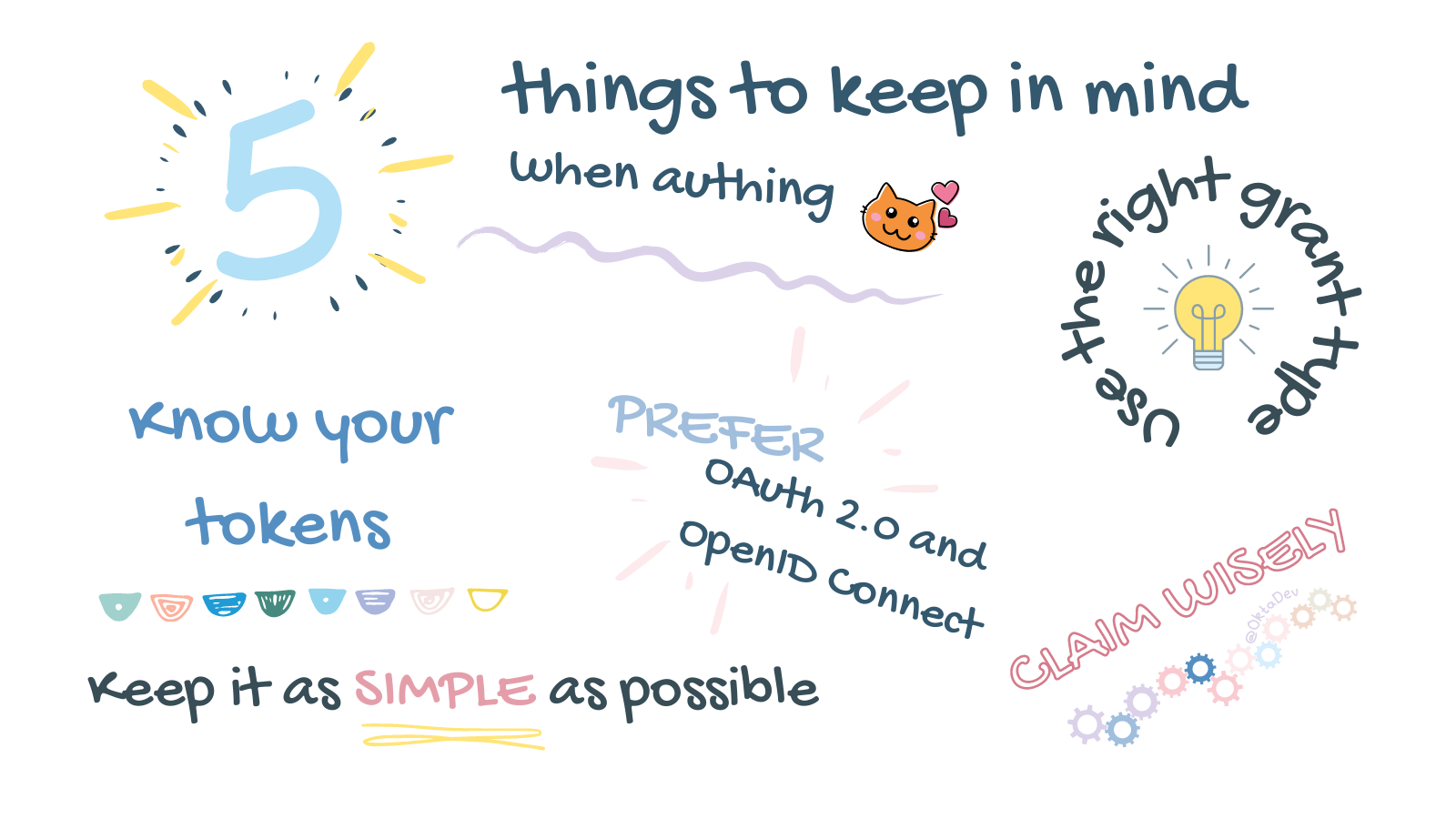
There’s a lot of information out there about adding authentication to your app, which is helpful! But also overwhelming. It can be hard to find relevant and up-to-date information. Security best practices and technologies change, so refreshing your understanding and keeping up with current best practices is a good thing. Here are some notes I took while I reviewed my knowledge and applied my experience implementing auth. Prefer OAuth 2.0 and OpenID Connect If you’re...
Security.txt: Make Vulnerabilities Easier to Report
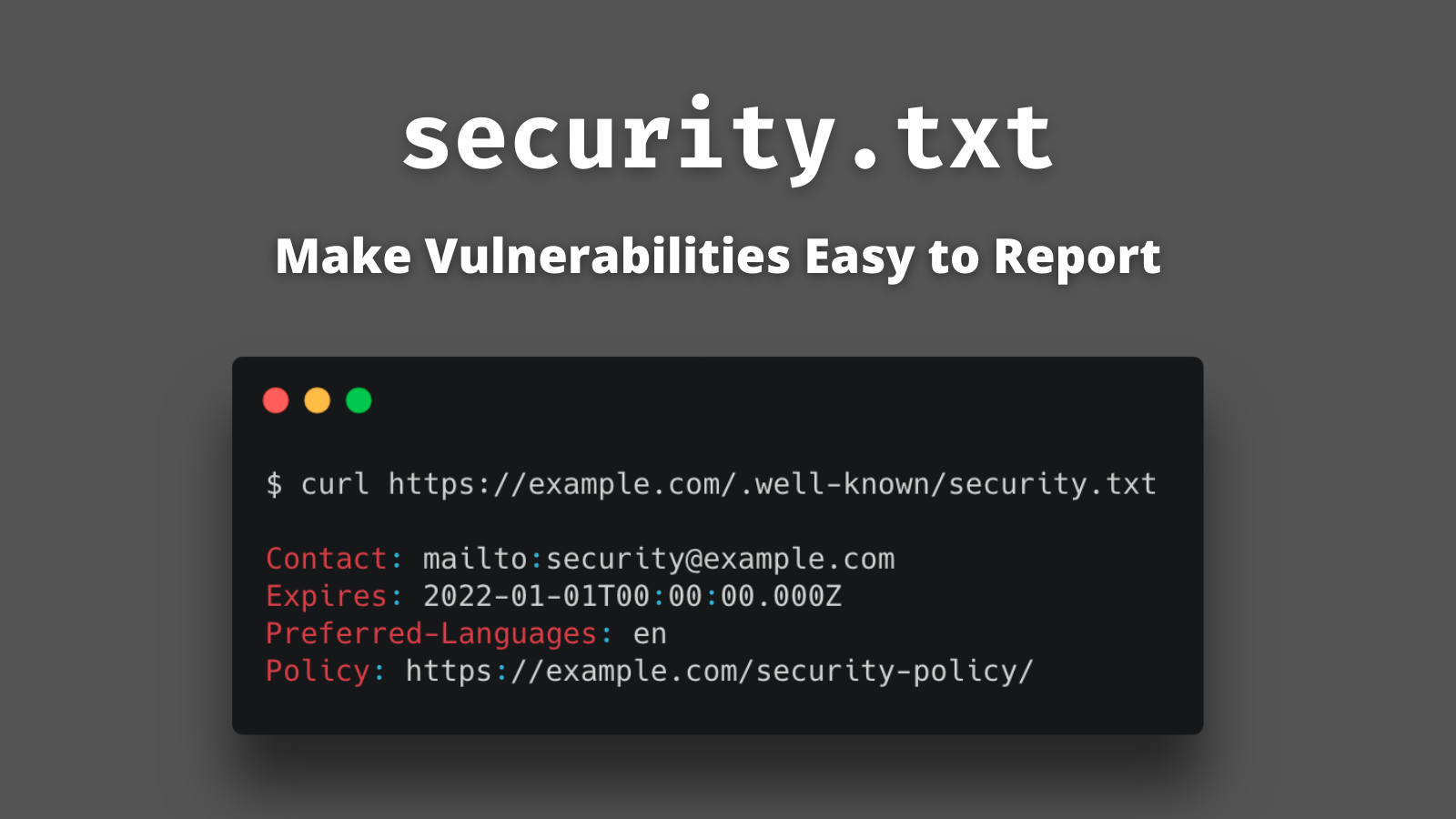
We all know that all software has bugs and that security is hard, but somehow we are still surprised when we see new vulnerabilities. Vulnerability A bug, flaw, weakness, or exposure of an application, system, device, or service that could lead to a failure of confidentiality, integrity, or availability. In 2020, there were 18,395 vulnerabilities reported, which means about 50 new vulnerabilities are reported every day. These numbers only include what has been reported to...
An Overview of Best Practices for Security Headers

Many decisions go into the process of creating a secure website. One of these decisions is selecting which HTTP security headers to implement. Today, we’ll dive into the most important HTTP security headers and the best practices that will strengthen your website’s security. Table of Contents The Security Headers HTTP Strict Transport Security (HSTS) Content-Security-Policy (CSP) X-XSS-Protection X-Frame-Options Referrer-Policy X-Content-Type-Options Permissions-Policy Configuring a Security Header Nginx Apache IIS Firebase Learn More About Security Headers The...
Announcing the Okta Identity Early Access Hackathon Winners

Back in early August, in partnership with DevPost, we announced the Okta Identity Early Access Hackathon, and invited developers everywhere to "build something awesome with the Okta Identity Engine (OIE) Limited GA release." Our aim was to give participants the chance to explore the new platform with its new capabilities for customer identity and access management. In exchange, we hoped to gain early stage feedback and a feel for what engaged the dev community worldwide....
Command Line Login with the OAuth Device Grant

Even if you’ve never heard of the OAuth 2.0 Device Authorization Grant, formerly known as the Device Flow, you’ve probably seen it in action on a smart TV or other streaming device. The Device Authorization Grant is commonly used on devices with limited keyboard input ability. The process allows you to log in to an account more easily via a separate browser on your laptop, mobile phone, or other companion rich-input device. For instance, if...
Centralize Authentication at the Gateway with Apache APISIX and OpenID Connect

Apache APISIX is a dynamic, real-time, high-performance API gateway, providing rich traffic management. The project offers load balancing, dynamic upstream, canary release, circuit breaking, authentication, observability, and many useful plugins. In addition, the gateway supports dynamic plugin changes along with hot-plugging. The OpenID Connect plugin for Apache APISIX allows users to replace traditional authentication mode with centralized identity authentication mode via OpenID Connect. NOTE: This post originally appeared on the Apache APISIX blog. Table of...
Fixing Common Problems with CORS and JavaScript
Many websites have JavaScript functions that make network requests to a server, such as a REST API. The web pages and APIs are often in different domains. This introduces security issues in that any website can request data from an API. Cross-Origin Resource Sharing (CORS) provides a solution to these issues. It became a W3C recommendation in 2014. It makes it the responsibility of the web browser to prevent unauthorized access to APIs. All modern...
The Rails Guide to Securing an API

In this tutorial we are going down a different track then our last Ruby Post (bad pun intended). Instead diving into building a very simple API that, of course, we will secure with access tokens minted by our very own Okta OAuth server. We’ll make requests to this API via Postman to keep things nice and simple. Now let’s get chugging along. (OK, that’s the last pun for a bit.) Prerequisites for this blog post...
OAuth Patterns and Anti-Patterns - a DZone Refcard

I’m happy to announce the release of a brand new OAuth cheat sheet published through DZone’s Refcardz, “OAuth Patterns and Anti-Patterns”. This five-page reference guide covers the latest in OAuth and clarifies some common misunderstandings of applying it to real world use cases. With a focus on OAuth 2.0, OpenID Connect, and best practices, you’ll quickly learn how to avoid some common mistakes and how to make your applications and APIs more secure. The “OAuth...
A Beginner's Guide to JWTs

JSON Web Tokens (JWT) are used everywhere (even places they shouldn’t be). This post will cover the basics of what you need to know about JWT and the related specifications in the Javascript Object Signing and Encryption (JOSE) family. JWT is pronounced "jot". Table of Contents What is a JWT? How JWTs Are Used JWT Structure JWT Claims JWT Header JWT Signature Problems with JWTs Learn More About JWT What is a JWT? A JWT...
Introducing the Okta CLI

Okta is an Identity Management Platform that takes all the hassle out of authentication and authorization. It’s feature-packed with everything from workforce integrations for G-Suite to the latest version of OAuth 2.0 as-a-service for developers writing their own APIs. It can sometimes be a daunting task for developers to get started with Okta because of how feature-rich it is. Introducing the Okta CLI - made by developers for developers. Using the CLI tool, you can...
OAuth Sketch Notes - Live Q&A
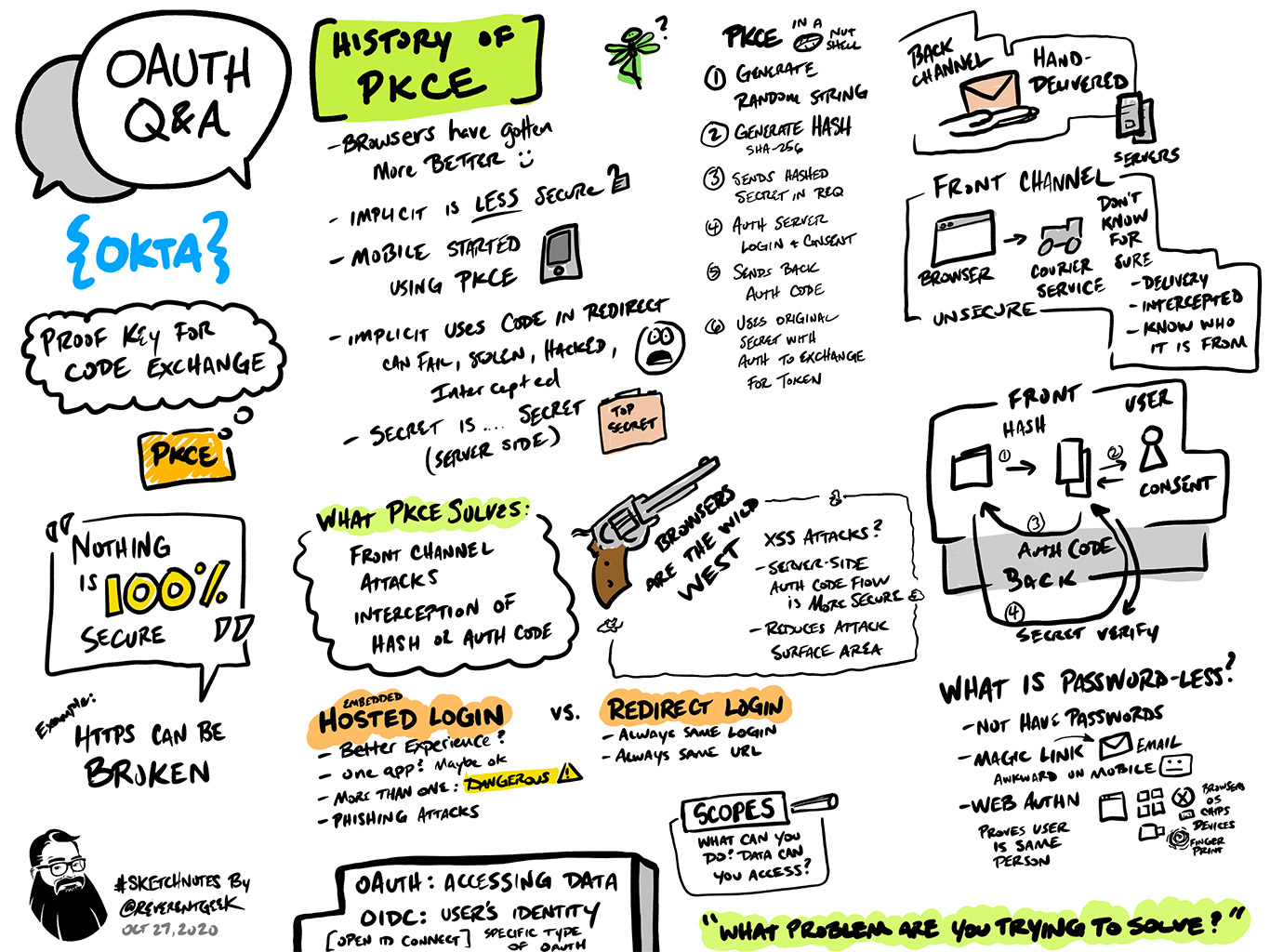
Why do we need PKCE in OAuth? How does PKCE work? What’s the difference between the front channel and back channel? Can SPAs even use a back channel? These are just a few of the things we talked about during this sketch notes livestream! Developer advocates Lee Brandt and Aaron Parecki discuss PKCE, cross-site scripting, OAuth vs OpenID Connect and more, all while David Neal sketched notes live! Some of the other topics covered include...
Easy Authentication for Ruby On Rails Login

A couple of things have changed in the Rails world since we published our last blog post on Rails. For one, Rails 6.0 was released on August 16, 2019 (Yay progress!), and, for another, Omniauth had a CRSF vulnerability reported (not so great). Does this make you a bit anxious? Don’t worry! Today we will be going over how to create a Rails app from scratch with the new Rails release and go over how...
Welcome Nick Gamb
My name is Nick Gamb and I am excited to be joining the Okta Developer Advocacy team for the .NET community. Who Am I At heart, I am just an inquisitive nerd who has had a very fortunate career getting to do many different things. I love video games, computers, programming, hacking, security, DevOps, data, film, photography, sound design, editing -it’s a long list. For the brave and interested, the longer, but still condensed, version...
JWT vs Opaque Access Tokens: Use Both With Spring Boot

The topic of validating an OAuth 2.0 access tokens comes up frequently on this blog. Often we talk about how to validate JSON Web Token (JWT) based access tokens; however, this is NOT part of the OAuth 2.0 specification. JWTs are so commonly used that Spring Security supported them before adding support for remotely validating tokens (which is part of the OAuth 2.0 specification.) In this post, you will build a simple application that takes...
Introducing JPaseto: Security Tokens For Java

PASETO is a new security token format designed to be easy to use and free from the issues inherent with JSON Web Token (JWT) related specifications. Platform Agnostic SEcurity TOkens (PASETO) is a draft RFC spec created by Scott Arciszewski. PASETO reduces the scope of the JavaScript Object Signing and Encryption (JOSE) family of specs (which JWT is a part of), while still providing the functions that secure applications need. PASETO is everything you love...
SQL Injection in PHP: Practices to Avoid

SQL injections are one of the most common vulnerabilities found in web applications. Today, I’m going to explain what a SQL injection attack is and take a look at an example of a simple vulnerable PHP application accessing a SQLite or MySQL database. After that, we’ll look at several methods to prevent this attack, fixing the problem. Prerequisites Make sure you have the following software installed and enabled on your system: PHP 7 Composer PHP...
Serverless Java with Amazon Web Services

Serverless is the next iteration in cloud management. First, we let go of having physical hardware servers and moved all of our servers into the cloud because, hey, why bother managing all that hardware? This created cloud infrastructure providers that resulted in behemoths like Amazon and Google. Now, they’re saying, why bother managing a server at all? What you really want to do is run code, right? Serverless is an architecture where code is run...
What's New with OAuth and OpenID Connect?

In this video you'll learn about the latest developments in the OAuth and OpenID Connect specs from Aaron Parecki, a regular contributor to the OAuth working group. The latest additions to the specs enable richer experiences and better security for applications using OAuth.
Security Patterns for Microservice Architectures

If you attend a lot of Java ecosystem conferences, you’ll think that everyone uses microservices. It’s a trendy topic, and developers everywhere are interested in learning about them. For a good reason too! Microservice architectures are a technique for delivering code faster. Chris Richardson is a friend and expert on microservices. He suggests a helpful guideline in a recent blog post: Why microservices? IF you are developing a large/complex application AND you need to deliver...
A Developer Guide to Reporting Vulnerabilities

Many of us are not familiar with vulnerability reporting and how it is different from reporting a regular bug. Frequently, I’ve seen people report vulnerabilities or potential security issues incorrectly. A public bug tracker or Stack Overflow is NOT the right tool; developers need to handle vulnerabilities differently and should not disclose them until the project/vendor fixes them. In this post, you will learn basics about vulnerabilities, how they relate to Common Vulnerabilities and Exposures...
Create and Verify PASETO Tokens in Java

PASETO is the latest trend in security token formats. Its primary goal is to reduce the problems the JSON Web Token (JWT) related specifications introduce. In this post, I’ll give you a brief introduction to PASETO tokens and then jump into an example that creates and parses tokens using in Java using JPaseto. If you’d rather watch a video, I created a screencast too! What is PASETO? PASETO stands for Platform-Agnostic SEcurity TOkens. The PASETO...
AWS Athena as a Data Analysis Supplement

As part of a security investigation, you may be tasked with determining whether a specific API action occurred throughout your cloud deployment within some distant date range. This would normally be straightforward to determine, by using either the provided CloudTrail querying console or a Security Information and Event Management platform (SIEM) which is set to consume these logs such as Splunk or Elasticsearch. For most data analysis solutions, the amount of data ingested or stored...
Use Okta Token Hooks to Supercharge OpenID Connect

OpenID Connect (OIDC) and OAuth 2.0 are already recognized as powerful tools for incorporating authentication and authorization into modern web applications. Okta has enhanced the capabilities of these standards by introducing our Inline Hooks feature. There are a number of different types of inline hooks that Okta supports. In this post, I focus on hooks that allow you to patch information into the tokens you get back from Okta via OIDC and OAuth. You’ll first...
Multi-Factor Authentication Sucks
For the last seven years or so I’ve been building developer tools to help make user authentication and authorization simpler and more secure. When I’m not building tools to help secure web applications, I’m often writing articles, creating videos, and educating developers on web security best practices. I care a lot about web security. With that said (and I almost feel guilty admitting this), I think multi-factor authentication (MFA) sucks. It’s slow, annoying, frustrating, and...
Why Every Developer Needs to be a Generalist
Context, as they say, is king. The age-old question of exactly what a software developer should focus on learning has been crossing my mind a lot lately. More than ever, our technology is evolving at a furious pace - and the coding world is definitely feeling the pressure. It can be overwhelming to choose where to pay attention and what to dismiss as a passing fad. So what are you to do? Let’s look at...
OAuth 2.0 Java Guide: Secure Your App in 5 Minutes
Modern applications rely on user authentication, but it can present Java developers with a difficult challenge, as well as a range of framework-specific options to choose from. We have seen many Spring developers start with a simple, home-grown authentication service they plan to replace “later” with a more robust option… only for that homegrown service to bikeshed its way to a permanent place in the stack. To end this cycle of heartbreak, this post will...
The Dangers of Self-Signed Certificates
How many times have you started a new job, and the first thing you see on the company intranet is a “Your connection is not private” error message? Maybe you asked around and were directed to a wiki page. Of course, you probably had to click through the security warnings before actually viewing that page. If you are security-minded, this probably bothers you, but because you have a new job to do, you accept the...
An Illustrated Guide to OAuth and OpenID Connect
In the “stone age” days of the Internet, sharing information between services was easy. You simply gave your username and password for one service to another so they could login to your account and grab whatever information they wanted! Yikes! You should never be required to share your username and password, your credentials, to another service. There’s no guarantee that an organization will keep your credentials safe, or guarantee their service won’t access more of...
A Thorough Introduction to PASETO
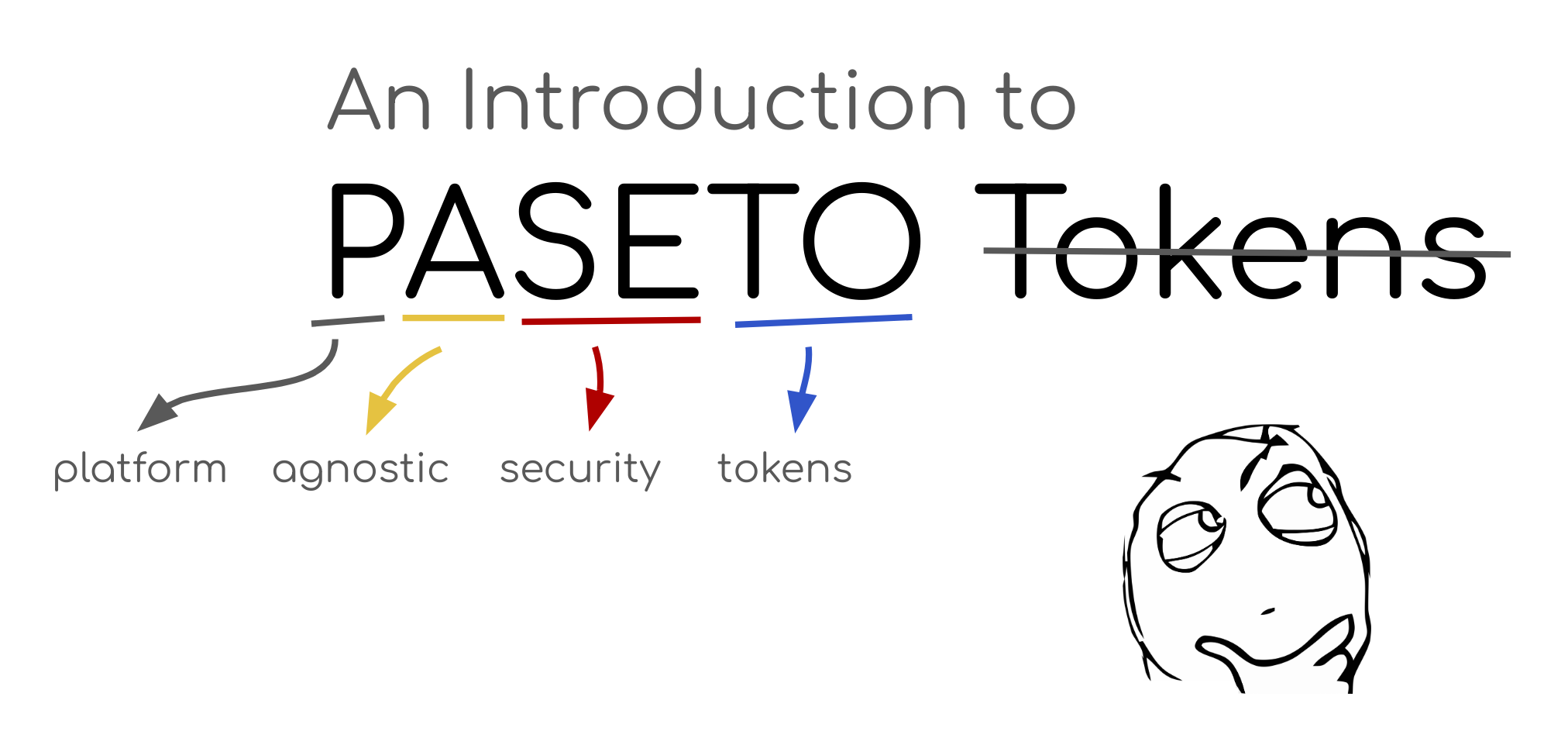
Today I’m going to introduce you to one of my favorite pieces of security technology released in the last several years: PASETO (platform-agnostic security tokens). PASETO is a relatively new protocol, designed by Scott Arciszewski in early 2018 that is quickly gaining adoption in the security community. While PASETO is still a young technology, I thought it’d be interesting to take an in-depth look at it, since it’s both incredibly useful and solves a lot...
Get Started with the ELK Stack

Good design principles require that microservices architectures are observable, and provide a centralized monitoring tool. This tool allows development teams to verify the overall system health, inspect logs and errors, and get feedback after deployments. So what is the Elastic (or ELK) Stack and why it is an excellent option to meet this need? In this tutorial post, you will learn how to … Set up and run the ELK stack in Docker containers Set...
Why Public Key Cryptography Matters

40 years old and as relevant today as when it was first invented, public key cryptography is the unsung hero of modern cybersecurity. Most people take unknowing advantage of it many times a day. So what is it, and how does it work? Let’s start by reviewing the concept of symmetric encryption, which allows you to encrypt information using a shared secret key. It’s not a modern idea—even Julius Caesar used it to code his...
Securing REST APIs

When machines ask each other for information online, they don’t need elaborate browser interfaces or clickable buttons. They just need raw data in a machine-readable format. Today, many applications get the data they need via a REST API–a powerful way of serving up information online that underpins many modern online services. Like any technology, REST APIs bring their own unique security challenges. The question that remains is how to reduce those vulnerabilities. What is a...
Combat Side-Channel Attacks with Cross-Origin Read Blocking

As if developers didn’t have a big enough task securing web applications from software-layer attacks, they now have to contend with another threat: hardware-layer vulnerabilities. These complex cybersecurity flaws were introduced long before many modern developers began coding and extend from the inner workings of a computer’s silicon to a web application’s code. If exploited, hardware-layer vulnerabilities can result in leaked information from the web browser to an attacker. Luckily, Cross-Origin Read Blocking (CORB) is...
Implement the OAuth 2.0 Authorization Code with PKCE Flow

Imagine two levers that are inversely connected. That is, as one goes up, the other goes down. One lever is User Experience and the other is Security. It’s not a perfect analogy, but most developers can attest that as user experience goes up, security goes down. Take browser history syncing for example. I can start a session with my bank on Firefox mobile and pick up right where I left off on Firefox desktop. From...
Easy Spring Boot Deployment with AWS Elastic Beanstalk

Nearly all applications rely on authentication. Developers, and the companies that employ them, want to confirm who is making the request and are they who they say they are. And, this needs to happen fast enough for a good user experience. Fortunately, there are great tools to help. Spring Boot with Spring Security is a fantastic solution for Java-based web development. With relatively little code, developers can implement, test, update, and expand authentication schemes easily...
SAML: What's Behind SSO
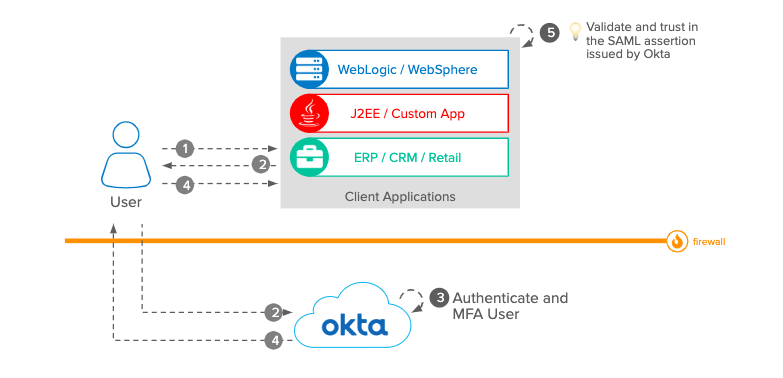
Apple’s recent announcement of a single sign-on (SSO) solution, Sign in with Apple, has developers everywhere thinking about how to incorporate it into their application’s infrastructure. Apple is hardly the first organization to introduce SSO—it’s a security-focused methodology that has been available for years—and one of the protocols behind it is SAML. The SAML protocol lets users prove their identities across multiple applications with just one set of login credentials. It was ratified in 2002...
Hashing Techniques for Password Storage

Picture yourself a year from now. Someone just put your entire password database on Pastebin. User accounts are being hacked by the thousands and your local privacy regulator just called to have a chat. Depending on the hashing algorithm you were using to store your user passwords, you could be in a lot of trouble. As they say, an ounce of prevention is worth a pound of cure, so how does hashing work and what...
The Hardest Thing About Data Encryption
Encrypting data is all about making sure that only the right people can view the data you’ve encrypted. There are two primary forms of data encryption: symmetric and asymmetric. While you can easily Google “symmetric encryption best practices” and figure out the best algorithms and developer libraries to use (more on this later) to encrypt and decrypt data, one thing isn’t so easy: figuring out how to properly store and manage your data encryption keys....
Container Security: A Developer Guide

Have you ever spent hours trying to figure out why your newly-installed database, web server, or Python library won’t work? If this sounds familiar, you likely understand the joy of software containers. Forget all those fruitless Stack Exchange searches trying to solve your configuration and dependency problems. Just install a container platform and pull an image. Looking to bootstrap an instant LAMP stack? You can save yourself the time and run sudo docker run -p...
Use Spring Boot and MySQL to go Beyond Authentication

In this post, we will walk through how to build a simple CRUD application using Spring Boot, MySQL, JPA/Hibernate and Okta OpenID Connect (OIDC) Single Sign-On (SSO). The Java Persistence API (JPA) provides a specification for persisting, reading, and managing data from your Java object to relational tables in the database. The default implementation of JPA via Spring Boot is Hibernate. Hibernate saves you a lot of time writing code to persist data to a...
Spring Method Security with PreAuthorize

This tutorial will explore two ways to configure authentication and authorization in Spring Boot using Spring Security. One method is to create a WebSecurityConfigurerAdapter and use the fluent API to override the default settings on the HttpSecurity object. Another is to use the @PreAuthorize annotation on controller methods, known as method-level security or expression-based security. The latter will be the main focus of this tutorial. However, I will present some HttpSecurity code and ideas by...
Build a Phone System for Your Company With Twilio, Okta, and JavaScript

If you’ve ever worked for a company with more than a few employees, you’ve probably seen some interesting phone systems. When I used to work at Cisco, everyone was given a dedicated Cisco desk phone that hooked up to a server somewhere in the company and each employee was assigned a unique phone number and extension. I never really liked that setup. It annoyed me that I had this big, clunky desk phone taking up...
Store ASP.NET Secrets Securely with Azure KeyVault

Nothing ruins your weekend quite as wholly as getting paged at 2 am on Saturday to tell you that there’s been a data breach at your company. In this post, I’m going to talk about how you can reduce the risk of that happening by keeping secrets out of your source code. By following this guide, you’ll create an ASP.NET Core MVC web application that uses Okta for identity management. Rather than working through a...
Simple Authentication with Spring Security

Authentication is vital to all but the most basic web applications. Who is making the request, wanting data, or wanting to update or delete data? Can you be sure that the request is coming from the stated user or agent? Answering this question with certainty is hard in today’s computer security environment. Fortunately, there is absolutely no reason to reinvent the wheel. Spring Boot with Spring Security is a powerful combination for web application development....
Easy Single Sign-On with Spring Boot and OAuth 2.0

Single sign-on used to be the “Holy Grail” of enterprise size companies and was usually only available companies that could afford it. Nowadays, we take SSO as a matter of course. For instance, you would think it was completely weird (and unpleasant) if you logged into GMail and then had to log in again when you went to Google Docs. But, what about building custom applications for developers? SSO was still in the domain of...
Is the OAuth 2.0 Implicit Flow Dead?

You may have heard some buzz recently about the OAuth 2.0 Implicit flow. The OAuth Working Group has published some new guidance around the Implicit flow and JavaScript-based apps, specifically that the Implicit flow should no longer be used. In this post we’ll look at what’s changing with the Implicit flow and why. Note: In May 2025, the Okta Integrator Free Plan replaced Okta Developer Edition Accounts, and the Okta CLI was deprecated. We preserved...
How to Configure Better Web Site Security with Cloudflare and Netlify

Working in the security industry and having an insecure site looks super bad. So imagine how I felt after discovering that the security report for my brand new personal site sucked: To fix this, I decided to improve my security score. I’m sharing my findings and solutions here so you can improve your site security too. This is good not only for improving your site security, but also to improve your SEO performance on Google....
Welcome Micah Silverman

My name is Micah Silverman and I just joined the Developer Advocacy team at Okta. TL;DR - There are some easter eggs in this post. If you want to know what they’re all about - jump to the bottom. Funny thing is, I’ve been working for Okta for 2 years now, just on different teams. It was in the Sales Engineering and Education Services teams that I learned all the ins and outs of the...
Data Persistence with Hibernate and Spring

Note: In May 2025, the Okta Integrator Free Plan replaced Okta Developer Edition Accounts, and the Okta CLI was deprecated. We preserved this post for reference, but the instructions no longer work exactly as written. Replace the Okta CLI commands by manually configuring Okta following the instructions in our Developer Documentation. Java developers typically encounter the need to store data on a regular basis. If you’ve been developing for more than 15 years, you probably...
Nobody Cares About OAuth or OpenID Connect

If you’re reading this post, there’s a good chance that you’re a web developer who’s very interested in web security. You’ve probably heard about OAuth or OpenID Connect (OIDC) before. You may have even used them at some point in your career. But here’s the thing: almost nobody actually cares about OAuth or OIDC. Not you, not me, and not even other developers in the security industry. To understand why nobody cares about these two...
Build a Basic App with Spring Boot and JPA using PostgreSQL

Every non-trivial application needs a way to save and update data: a resource server that is accessible via HTTP. Generally, this data must be secured. Java is a great language with decades of history in professional, enterprise development, and is a great choice for any application’s server stack. Within the Java ecosystem, Spring makes building secure resource servers for your data simple. When coupled with Okta, you get professionally maintained OAuth and JWT technologies easily...
Build a Single-Page App with Go and Vue
Single-Page Applications (SPAs) improve user experience by offering rich UI interactions, fast feedback, and the relief of knowing you don’t need to download and install a traditional application. Browsers are now operating systems and websites are apps. While a SPA isn’t always the answer, for apps that rely on snappy user interaction they are increasingly common. To the end user, a well-designed SPA feels like rainbows and unicorns. From the developer perspective, reality can often...
Stolen Access Tokens and You

What never dies, spreads rampantly, and is guaranteed to bite you? You guessed it: Stolen access tokens! In recent weeks, we’ve seen a number of hacks around OAuth access tokens. As much as we’d like to blame the underlying technology, it’s more out of misuse and misunderstanding than anything else. No matter who it is, the outbreak is the same: A website uses OAuth with little to no granularity in scopes The website issues an...
Simple Authentication with Rails and OmniAuth

Today I’m going to show you how to authenticate users into your Rails applications using the latest best-practices and a hosted authentication/authorization provider which makes managing users simple. Specifically, you’ll learn how to integrate Rails and Okta to create, manage, and secure users with OpenID Connect. To make this all work, you’ll be using one of the most popular gems in the Rails world: OmniAuth. Additionally, you’ll be using the fabulous devise gem to make...
How to Get More Internet Users to Enable 2FA on Their Accounts
If you are reading this article on the Okta Developer blog, chances are high that you are already quite familiar with two-factor authentication (2FA) and how it helps keep hackers out of user accounts even if they’re using compromised passwords. You probably already have 2FA enabled on all of your online accounts. Sadly, you are in the significant minority. Most People are Not Using 2FA Duo Security conducted a survey to research perceptions and adoption...
10 Excellent Ways to Secure Your Spring Boot Application

Spring Boot has dramatically simplified the development of Spring applications. Its autoconfiguration and starter dependencies reduce the amount of code and configuration you need to begin an app. If you were used to Spring and lots of XML back in the day, Spring Boot is a breath of fresh air. Spring Boot was first released in 2014, and a lot has changed since then. Much like code quality and testing, security has become a concern...
What Happens If Your JWT Is Stolen?
All of us know what happens if our user credentials (email and password) are discovered by an attacker: they can log into our account and wreak havoc. But a lot of modern applications are using JSON Web Tokens (JWTs) to manage user sessions—what happens if a JWT is compromised? Because more and more applications are using token-based authentication, this question is increasingly relevant to developers and critical to understand if you’re building any sort of...
How to Prevent Your Users from Using Breached Passwords
Not too long ago, the National Institute of Standards and Technology (NIST) officially recommended that user-provided passwords be checked against existing data breaches. Today I’m going to show you how you can easily add this functionality to any website you run using PassProtect, an open-source developer library we created specifically for this purpose. Why Check User Passwords? The new NIST recommendations mean that every time a user gives you a password, it’s your responsibility as...
Announcing PassProtect - Proactive Web Security
If you’re reading this article you probably care about web security. You probably use a password manager to manage your passwords, you’ve probably got multi-factor authentication setup for all of your services, and you’re probably already subscribed to Have I Been Pwned? so you’re alerted when one of your logins have been involved in a data breach. But you’re not most people. Most web users are completely disconnected from the incredible advancements that have been...
Simple Node Authentication
Authenticating users for Node.js/Express.js web apps can be difficult. You have to set up a database, define a user schema (or use something more flexible like NoSQL), write code to handle password hashing, etc. It’s annoying. Using Okta’s API service, however, you can easily register and log in users to your Node website using our OpenID Connect integration. Note: In May 2025, the Okta Integrator Free Plan replaced Okta Developer Edition Accounts, and the Okta...
WebAuthn: A Developer's Guide to What's on the Horizon
There’s been a lot of news lately about the new W3C Web Authentication API, also known as WebAuthn. Want to know what it’s all about? Let’s take a closer look. The Web Authentication API allows browsers to make use of hardware authenticators such as the Yubikey or a mobile phone’s biometrics, like a thumbprint reader or facial recognition. WebAuthn can be used with these technologies to enable two-factor authentication to websites, or even as the...
Token Authentication in ASP.NET Core 2.0 - A Complete Guide

Token authentication has been a popular topic for the past few years, especially as mobile and JavaScript apps have continued to gain mindshare. Widespread adoption of token-based standards like OAuth 2.0 and OpenID Connect have introduced even more developers to tokens, but the best practices aren’t always clear. I spend a lot of time in the ASP.NET Core world and have been working with the framework since the pre-1.0 days. ASP.NET Core 2.0 has great...
A Breakdown of the New SAML Authentication Bypass Vulnerability
Several weeks ago a new critical vulnerability was discovered that affects many SAML implementations. This vulnerability was first reported by Kelby Ludwig of Duo Security and is particularly interesting to us (as a user management company) as it can be used to bypass authentication in a sinisterly simplistic way. In this post, we’ll take an in-depth look at this new SAML vulnerability, what it is, how it works, and what you need to know to...
Set Up and Enforce Multi-Factor Authentication with the Okta API
So, you’re building a custom app and you need to include support for multi-factor authentication (MFA). Did you know that Okta’s API can support multi-step MFA workflows? The diagram below shows the primary authentication flows with MFA enrollment and enforcement enabled. Okta has a push-based verification app called Okta Verify. It’s available on the Google Play and Apple App stores. Okta Verify is similar to Google Authenticator, except it adds the additional feature of supporting...
Build User Registration with Node, React, and Okta
Today’s internet users expect a personalized experience. Developers must learn to develop websites that provide that personalized experience while keeping their user’s information private. Modern web applications also tend to have a server-side API and a client-side user interface. it can be challenging to get make both ends aware of the currently logged in user. In this tutorial, I will walk you through setting up a Node API that feeds a React UI, and build...
How to Secure Your .NET Web API with Token Authentication

API security can be complex. In many cases, just because you’ve built an API that you want to make public, it doesn’t mean that you want just anybody accessing it. In most cases, you want fine-grained control over who can access the API, but setting up that kind of user management can be a daunting task: you’d have to create your own authorization service that can create API credentials for your users and have the...
Build a Preact App with Authentication
React is a fast, and lightweight library, which has led to fast adoption across the SPA (single-page app) ecosystem. Preact is an even lighter-and-faster alternative to React, weighing in at a measly 3kb! For less complex applications, it can be a great choice. In this tutorial, you’ll build a basic Preact application with a couple of pages and user authentication using the Okta Sign-In Widget. Bootstrap Your App With PreactCLI To get your project started,...
Why JWTs Suck as Session Tokens
JSON Web Tokens (JWTs) are so hot right now. They’re all the rage in web development: Trendy? ✓ Secure? ✓ Scalable? ✓ Compact? ✓ JSON? ✓ With all these amazing things going for JWTs, they seem like an unstoppable hype train headed straight for Stack Overflow fame and fortune! But… today I’m here to talk with you about the downsides of using JWTs. Specifically, why it’s a bad idea to use JWTs as session tokens...
What the Heck is OAuth?
There’s a lot of confusion around what OAuth actually is. Some people think OAuth is a login flow (like when you sign into an application with Google Login), and some people think of OAuth as a “security thing”, and don’t really know much more than that. I’m going to show you what OAuth is, explain how it works, and hopefully leave you with a sense of how and where OAuth can benefit your application. What...
REST Service Authorization with JWTs
Many companies are adopting micro-services based architectures to promote decoupling and separation of concerns in their applications. One inherent challenge with breaking applications up into small services is that now each service needs to deal with authenticating and authorizing requests made to it. Json Web Tokens (JWTs) offer a clean solution to this problem along with TLS client authentication lower down in the stack. Wils Dawson and I presented these topics to the Java User...
Demystifying OAuth
It seems that OAuth 2.0 is everywhere these days. Whether you are building a hot new single page web application (SPA), a native mobile experience, or just trying to integrate with the API economy, you can’t go far without running into the popular authorization framework for REST/APIs and social authentication. During Oktane15, Karl McGuinness, our Senior Director of Identity, demystified the powerful, yet often misunderstood, world of OAuth 2.0 and shared details on Okta’s growing...
TLS Client Authentication for Internal Services
If you’re like me, the most aggravating thing is finding a Stack Overflow question that exactly describes the issue you are facing, only to scroll down and see that it has remained unanswered since 2011. I was recently trying to configure Transport Layer Security (TLS) client authentication (also referred to as mutual SSL) between two internal services at Okta and found the lack of complete examples astonishing. I hope that this blog post provides a...