Articles tagged oauth2
Elevate Access Token Security by Demonstrating Proof-of-Possession

We use access tokens to request data and perform actions within our software systems. The client application sends a bearer token to the resource server. The resource server checks the validity of the access token before acting upon the HTTP request. What happens if the requesting party is malicious, steals your token, and makes a fraudulent API call? Would the resource server honor the HTTP request? If you use a bearer token, the answer is...
Get Started with Jetty, Java, and OAuth

Jetty is a small, highly-scalable Java-based web server and servlet engine. It supports HTTP/2, WebSockets, and many other protocols. It powers websites and frameworks, both large and small, such as Google AppEngine. Because it is an Eclipse project, its open source project is called Eclipse Jetty. It is standards-compliant and open source, as well as commercially usable. It is the main alternative to Tomcat when hosting Java applications. Like Tomcat, you can use Jetty both...
Add Auth to Any App with OAuth2 Proxy
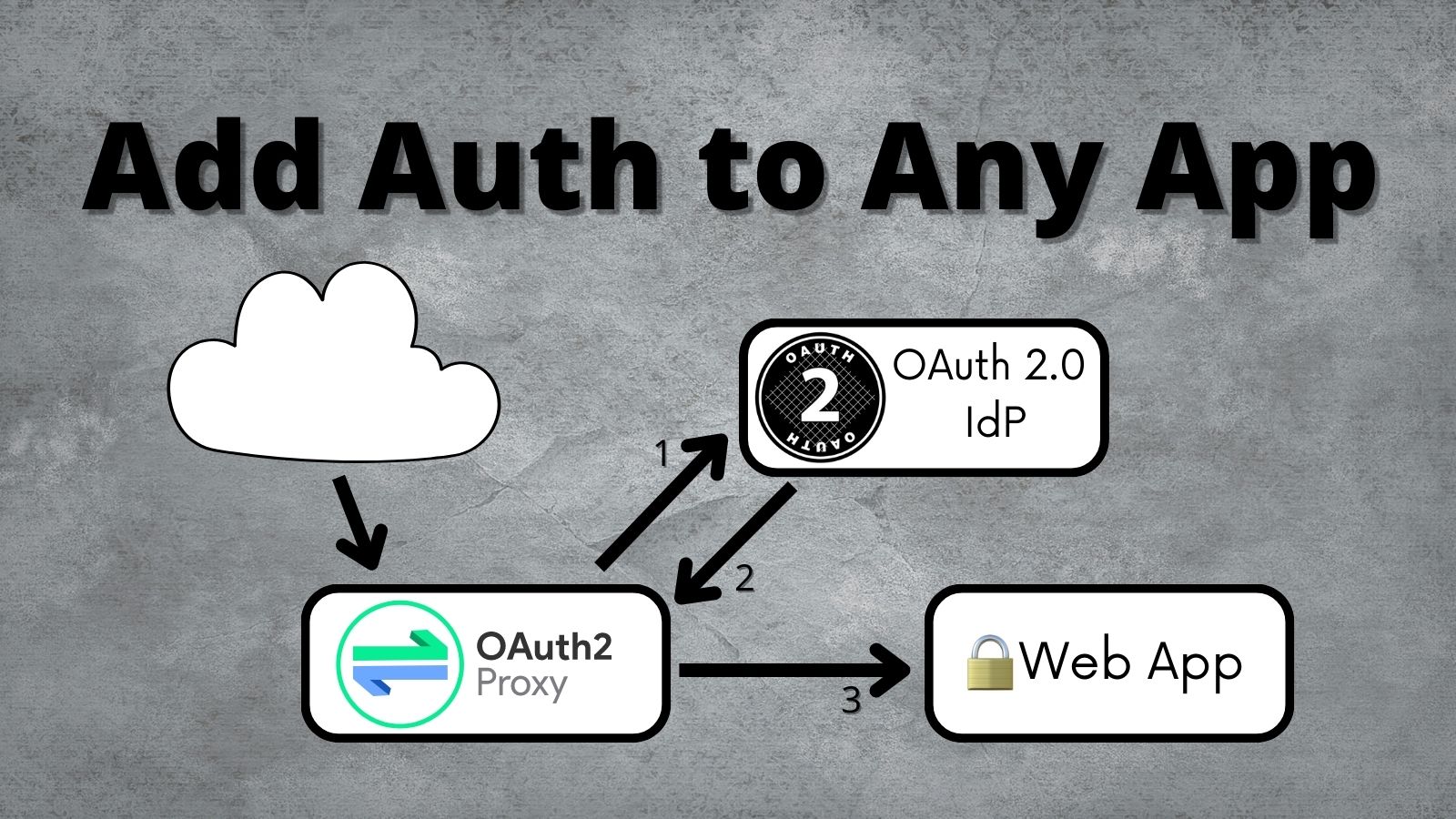
Updating an application to use OAuth 2.0 doesn’t need to be complicated. Most of the time, your language or framework will already have an OAuth library. Sometimes, this isn’t the case, and you need to find an alternative. In this post, I’ll walk through setting up and using OAuth2 Proxy to secure your application without any code changes! OAuth2 Proxy is a reverse proxy that sits in front of your application and handles the complexities...
OAuth for Java Developers

You can use OAuth to secure apps, APIs, and devices. OAuth has become increasingly popular, especially as developers are asked to knit together hundreds of apps and thousands of users in enterprise environments. The Java ecosystem is vast, with over 10 million developers worldwide and an abundance of IDEs, build tools, libraries, and frameworks to make them more productive. The infographic below is recommended as a starting point for Java developers. It’s designed to help...
Authenticate from the Command Line with Java
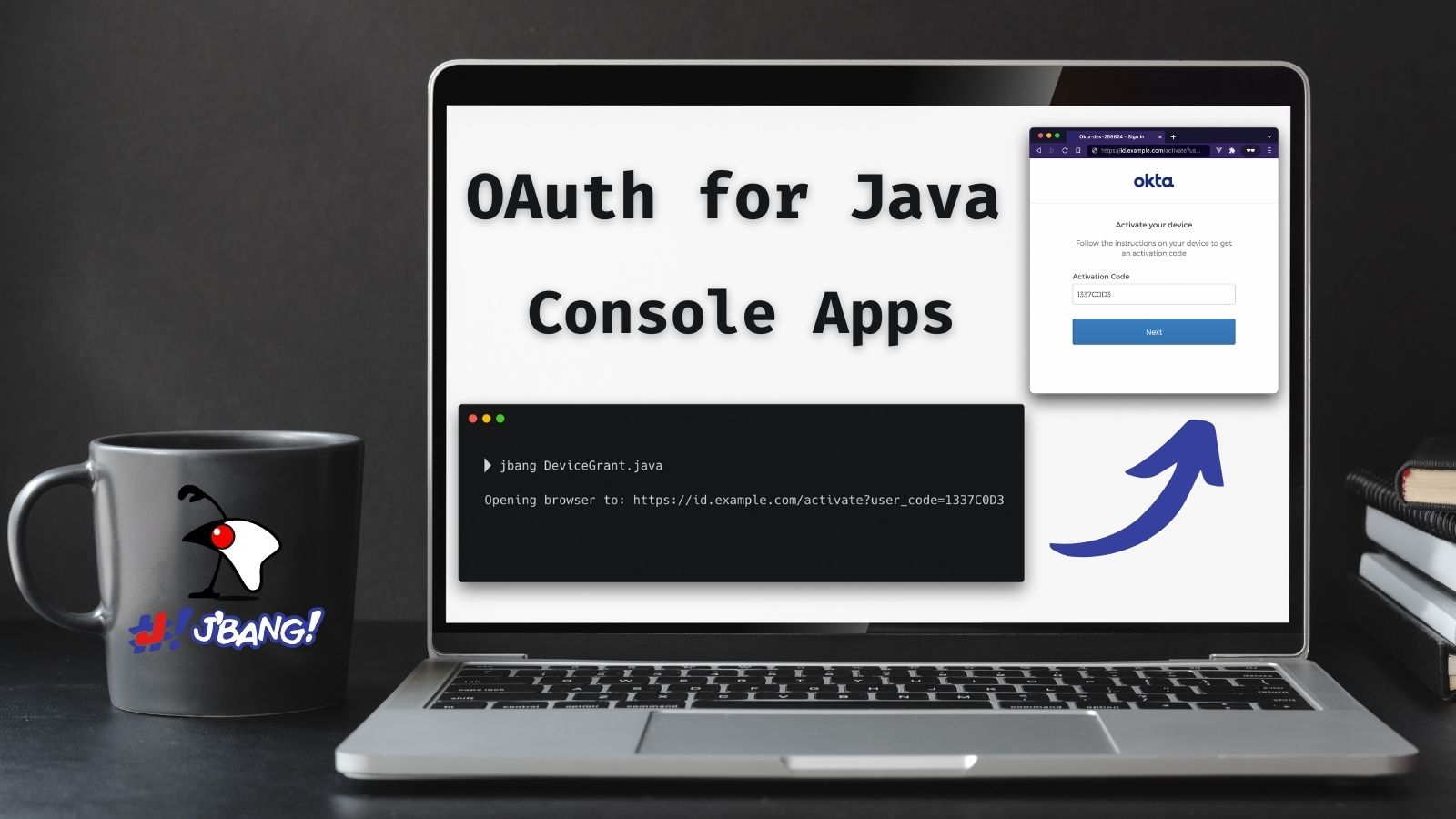
Anyone who has tried to type a password using a television remote can tell you what a pain it is. Not only will you be frustrated with the keyboard, but it’s not secure; everyone else in the room can see what you are typing. Fortunately, the OAuth 2.0 Device Authorization Grant gives you an easier way to sign in. The name is a mouthful, but if you have ever logged in to a TV by...
Better Integration Testing With Spring Cloud Contract

Spring Cloud Contract was created as a way to help test interconnected microservices. Generally speaking, there are two options when testing microservices: 1) you can deploy the entire mesh of services in your integration tests and test against that, or 2) you can mock each service in your integration tests. Both of these options have serious drawbacks. The first, deploying the entire mesh of microservices for testing, has the obvious drawback of being difficult, if...
Learn How to Build a Single-Page App with Vue and Spring Boot

In this tutorial, you are going to create a single-page application (SPA) that uses a Spring Boot resource server and a Vue front-end client. You’ll see how to configure Spring Boot to use JSON Web Tokens (JWT) for authentication and authorization, with Okta as an OAuth 2.0 and OpenID Connect (OIDC) provider. You’ll also see how to bootstrap a Vue client app with the Vue CLI and how to secure it using the Okta Sign-In...
Session Clustering for OAuth 2.0 Applications

A common OAuth 2.0 question we get: "How do I deal with OAuth in a load-balanced application?" The short answer: There’s nothing specific about session clustering for OAuth. The longer answer is—you likely still need to worry about cluster session management. This post will discuss how an OAuth login relates to your application’s session. And we’ll build a simple, secure, load-balanced application to demonstrate. Note: In May 2025, the Okta Integrator Free Plan replaced Okta...
Command Line Login with the OAuth Device Grant

Even if you’ve never heard of the OAuth 2.0 Device Authorization Grant, formerly known as the Device Flow, you’ve probably seen it in action on a smart TV or other streaming device. The Device Authorization Grant is commonly used on devices with limited keyboard input ability. The process allows you to log in to an account more easily via a separate browser on your laptop, mobile phone, or other companion rich-input device. For instance, if...
Centralize Authentication at the Gateway with Apache APISIX and OpenID Connect

Apache APISIX is a dynamic, real-time, high-performance API gateway, providing rich traffic management. The project offers load balancing, dynamic upstream, canary release, circuit breaking, authentication, observability, and many useful plugins. In addition, the gateway supports dynamic plugin changes along with hot-plugging. The OpenID Connect plugin for Apache APISIX allows users to replace traditional authentication mode with centralized identity authentication mode via OpenID Connect. NOTE: This post originally appeared on the Apache APISIX blog. Table of...
How to Prevent Reactive Java Applications from Stalling

Modern applications must work smoothly on high loads and with a high number of concurrent users. Traditional Java applications run blocking code and a common approach for scaling is to increase the number of available threads. When latency comes into the picture, many of these additional threads sit idle, wasting resources. A different approach increases efficiency by writing asynchronous non-blocking code that lets the execution switch to another task while the asynchronous process completes. Project...
Spring WebClient for Easy Access to OAuth 2.0 Protected Resources

Spring ẀebClient was added as part of the reactive web stack WebFlux in Spring Framework 5.0. WebClient allows performing HTTP requests in reactive applications, providing a functional and fluent API based on Reactor, and enabling a declarative composition of asynchronous non-blocking requests without the need to deal with concurrency. One of its features is support for filter registration, allowing to intercept and modify requests, which can be used for cross-cutting concerns such as authentication, as...
How to Use Client Credentials Flow with Spring Security

The client credentials grant is used when two servers need to communicate with each other outside the context of a user. This is a very common scenario—and yet, it’s often overlooked by tutorials and documentation online. In contrast, the authorization code grant type is more common, for when an application needs to authenticate a user and retrieve an authorization token, typically a JWT, that represents the user’s identity within the application and defines the resources...
Introducing the Okta CLI

Okta is an Identity Management Platform that takes all the hassle out of authentication and authorization. It’s feature-packed with everything from workforce integrations for G-Suite to the latest version of OAuth 2.0 as-a-service for developers writing their own APIs. It can sometimes be a daunting task for developers to get started with Okta because of how feature-rich it is. Introducing the Okta CLI - made by developers for developers. Using the CLI tool, you can...
Spring Cloud Config for Shared Microservice Configuration

The microservice architecture pattern, in which business functionality is distributed among many small atomic applications as opposed to one or two monolithic chunks, is very powerful and in wide use across large and small tech companies. Each piece has a narrow, well-defined task and communicates with other services via a shared channel (usually REST APIs). The benefits of adopting a microservice architecture include: Easier maintenance and development of applications: developers and teams can focus on...
Create a Secure Ktor Application with Kotlin

In this tutorial, you will build your very own Nano Blogging Service (nabl for short) using a modern JVM stack. This includes using the Kotlin programming language, the Ktor web framework, and securing it with Okta. Users can log in or sign up, post updates, and browse specific or global chronological feed without advertisements. The blogging service displays posts from the selected user or everyone in the chronological feed. Kotlin is often considered a “better...
Build a Secure Micronaut and Angular App with JHipster

Micronaut is a new framework for developing JVM applications, including APIs and microservices. It uses ahead-of-time (AOT) compilation to compute the information that your application needs before runtime, removing the need for reflection. The result is a significant decrease in runtime overhead and startup time, and a substantial increase in application throughput. Micronaut is a direct competitor to Spring Boot from the folks that invented Grails. Its design and runtime efficiency make it ideal for...
Serverless Java with Amazon Web Services

Serverless is the next iteration in cloud management. First, we let go of having physical hardware servers and moved all of our servers into the cloud because, hey, why bother managing all that hardware? This created cloud infrastructure providers that resulted in behemoths like Amazon and Google. Now, they’re saying, why bother managing a server at all? What you really want to do is run code, right? Serverless is an architecture where code is run...
Continuous Integration with Jenkins and Java

Continuous Integration (CI) is a popular development practice that helps to ensure software is high-quality and deployable, as you validate (compile and test) the software as soon as you check in changes to the Source Control Management System (SCM). You must have some key elements in place to adopt CI: A SCM system like Git, and a shared repository A CI server like Jenkins Automated tests Teamwork CI practices that allow you to keep build...
Use PKCE with OAuth 2.0 and Spring Boot for Better Security

Browser and mobile feature enhancements move fast. Often times, these technologies move faster than security standards designed to protect them can keep up. OAuth 2.0 offers the best and most mature standard for modern applications. However, there hasn’t been an official release of this standard since 2012. Eight years is a very long time in Internet technology years! That doesn’t mean that its contributors have been sitting idly by. There is active work on the...
Build a CRUD Application with Kotlin and React

In this tutorial, you’re going to build a client and server application using React for the frontend and Kotlin with Spring Boot for the backend. You’ll first build the app unsecured before securing it using Okta. To secure the React frontend, you’ll use OAuth 2.0 login, and for the backend, you’ll use a JSON Web Token and Spring Boot’s resource server OAuth implementation. This tutorial covers a lot of ground. It also uses a lot...
Build a CRUD API with Java and MongoDB

This tutorial leverages two technologies that are commonly used to build web services: MongoDB and Java (we’ll actually use Spring Boot). MongoDB is a NoSQL database, which is a generic term for any non-relational databases and differentiates them from relational databases. Relational databases, such as SQL, MySQL, Postgres, etc…, store data in large tables with well-defined structures. These structures are strong and tight and not easily changed or customized on a per-record basis (this structure...
OAuth 2.1: How Many RFCs Does it Take to Change a Lightbulb?
The OAuth working group agreed last month in Singapore (IETF 106) that work will begin to update the current OAuth 2.0 Framework to a potential version 2.1 encompassing all the latest recommendations and best practices around the specification. This is in part due to the maze of documentation that developers need to understand when getting started on the topic to choose the correct flow and implement the best security posture for their application landscape. By...
Kotlin: A Beginner's Guide and Tutorial

Kotlin is a modern, statically typed language within the JVM. Kotlin is a cross-platform, multi-purpose, free and open-source language developed by JetBrains under the Apache 2.0 license and has constructs for both Object Oriented and Functional programming styles, which can be mixed. It can be used for web development, server and client, and mobile development, using most Java IDEs. Kotlin is an awesome option for Java developers because it is concise, expressive, and safe. According...
ASP.NET Core 3.0 MVC Secure Authentication

On September 23rd, Microsoft announced the third major release of its .NET Core framework. This new release boasts better performance, support for Windows Desktop apps, improved support for Docker containers, and more. Naturally, I was excited to see this new release and get authentication hooked into it with Okta! I put together this tutorial to demonstrate how to quickly and securely set up user management with Okta and OIDC (OpenID Connect) in an ASP.NET Core...
Get Started with Jetty, Java, and OAuth
OAuth 2.0 Java Guide: Secure Your App in 5 Minutes
Modern applications rely on user authentication, but it can present Java developers with a difficult challenge, as well as a range of framework-specific options to choose from. We have seen many Spring developers start with a simple, home-grown authentication service they plan to replace “later” with a more robust option… only for that homegrown service to bikeshed its way to a permanent place in the stack. To end this cycle of heartbreak, this post will...
How to Develop a Quarkus App with Java and OIDC Authentication

Quarkus is a container-first Kubernetes Java framework designed to have a super-fast start-up time and low memory usage. The container-first strategy emphasizes packaging the runtime environment along with the application code, allowing both to be tightly optimized and avoiding the endless updates and configuration problems that can come along with monolithic server systems. Quarkus was built from the beginning to support compilation to native code for use with Graal/SubstrateVM but also supports the good old...
Build a Simple CRUD App with Java and JSF

JavaServer Faces (JSF) is a Java framework for building Web applications, centered on components as the building blocks for the user interface. JSF benefits from a rich ecosystem of tools and vendors, as well as out of the box components and libraries that add even more power. Why use JSF instead of JavaServer Pages (JSP)? There are two primary reasons: First, JSF has more templating capabilities, since it doesn’t write your view directly as it...
Get Started with the ELK Stack

Good design principles require that microservices architectures are observable, and provide a centralized monitoring tool. This tool allows development teams to verify the overall system health, inspect logs and errors, and get feedback after deployments. So what is the Elastic (or ELK) Stack and why it is an excellent option to meet this need? In this tutorial post, you will learn how to … Set up and run the ELK stack in Docker containers Set...
Build an Application with Spring Boot and Kotlin

In 2011, JetBrains, the company behind IntelliJ, decided to create a modern language that would run inside the Java Virtual Machine and address common concerns with Java at the time like its verbosity. This project became Kotlin, a quickly growing and popular language. Google then announced official support for Kotlin on Android, further accelerating its adoption. Many companies started to replace Java with Kotlin as their main language to take advantage of the new features...
5 Minute Serverless Functions in Azure without an IDE

Microsoft Azure makes it incredibly easy to get a basic API/microservice up and running quickly! If you are unfamiliar with building serverless architecture in the Microsoft ecosystem, using Azure Functions has become a quick way to get back-end code up and running that is easy to understand and usable for anyone. In this tutorial, we will set-up an API endpoint using the HTTP Trigger invocation that you can use with any front-end site. I use...
Implement the OAuth 2.0 Authorization Code with PKCE Flow

Imagine two levers that are inversely connected. That is, as one goes up, the other goes down. One lever is User Experience and the other is Security. It’s not a perfect analogy, but most developers can attest that as user experience goes up, security goes down. Take browser history syncing for example. I can start a session with my bank on Firefox mobile and pick up right where I left off on Firefox desktop. From...
Make Java Tests Groovy With Hamcrest

My favorite way to test Java code is with Groovy. Specifically, writing tests in Groovy with Hamcrest. In this post, I’ll walk through how to test a simple Spring Boot application with these tools. Groovy is an optionally typed dynamic language for the JVM, and can be compiled statically. That is a mouthful and I’ll explain this as we go, but for now think of Groovy as Java with lots of sugar. Groovy is a...
Tutorial: How to Build a JavaFX Desktop App with OIDC Authentication

JavaFX, a library of user interaction controls, allows Java developers to build cross-platform desktop applications and internet application. It was intended as a replacement for Swing (if you’re old like me and remember that). Implementing an authorization flow with OAuth 2.0 can be tricky with a desktop framework like JavaFX. Typically, OAuth flows require a browser and redirecting to specific URLs. Detecting a redirect in JavaFX’s default browser is impossible. The default Java browser (java.awt.Desktop.browse(URI))...
Easy Spring Boot Deployment with AWS Elastic Beanstalk

Nearly all applications rely on authentication. Developers, and the companies that employ them, want to confirm who is making the request and are they who they say they are. And, this needs to happen fast enough for a good user experience. Fortunately, there are great tools to help. Spring Boot with Spring Security is a fantastic solution for Java-based web development. With relatively little code, developers can implement, test, update, and expand authentication schemes easily...
Secure Your ASP.NET Core App with OAuth 2.0

Do you ever wish you had a virtual scrap of paper you could use to write notes in the cloud? I’ll show you how to build a simple ASP.NET Core app to keep track of your notes, plus how to use .NET Core’s OAuth 2 authentication middleware to secure access to your app so your personal notes are kept private. Note: In May 2025, the Okta Integrator Free Plan replaced Okta Developer Edition Accounts, and...
A Quick Guide to Spring Boot Login Options

In this post, you’re going to work through various options for implementing a login feature using Spring Boot 2.1. You’ll start with the most simple, basic auth, which you’d likely never want to use except for perhaps an internal backend tool, and move on to a simple form-based authentication page. Next, you’ll customize the default, auto-generated form by overriding some default templates and controllers. Finally, you’ll move on to adding Single Sign-on using OAuth 2.0....
A Quick Guide to OAuth 2.0 with Spring Security

When building a web application, authentication and authorization is a must. Doing it right, however, is not simple. Computer security is a true specialty. Legions of developers work day and night against equally numerous international hackers creating a continual development cycle of finding vulnerabilities, attacking them, and fixing them. Keeping up with all this solo would be painful (if not impossible). Fortunately, there’s no need. Spring Security and Spring Boot have made implementing a web...
Migrate Your Spring Boot App to the Latest and Greatest Spring Security and OAuth 2.0

Spring Boot 1.5.x made it easier than ever before to integrate Spring Security with OAuth 2.0 into your application. Spring Boot 2.1.x dials it up to 11 by making OpenID Connect a first class citizen in the stack. In this post, you start with Spring Boot 1.5.19 and Spring Security 4.2.x. You integrate it with Okta’s OAuth service. From there, you move onto Spring Boot 2.1.3 and Spring Security 5.1. You’ll see how integrating with...
Devnexus 2019: Join the <dev/>olution

Hello, Developers! Have you ever been to the wonderful conference known as Devnexus? I attended for the first time two years ago and had a blast! It’s well organized, affordable, and has a diverse and fun crowd. This year, Okta is sponsoring Devnexus and we have a number of speakers sharing their wisdom. I thought it’d be fun to write a blog post that highlights my team members and what they’ll be talking about. If...
Add the OAuth 2.0 Device Flow to any OAuth Server
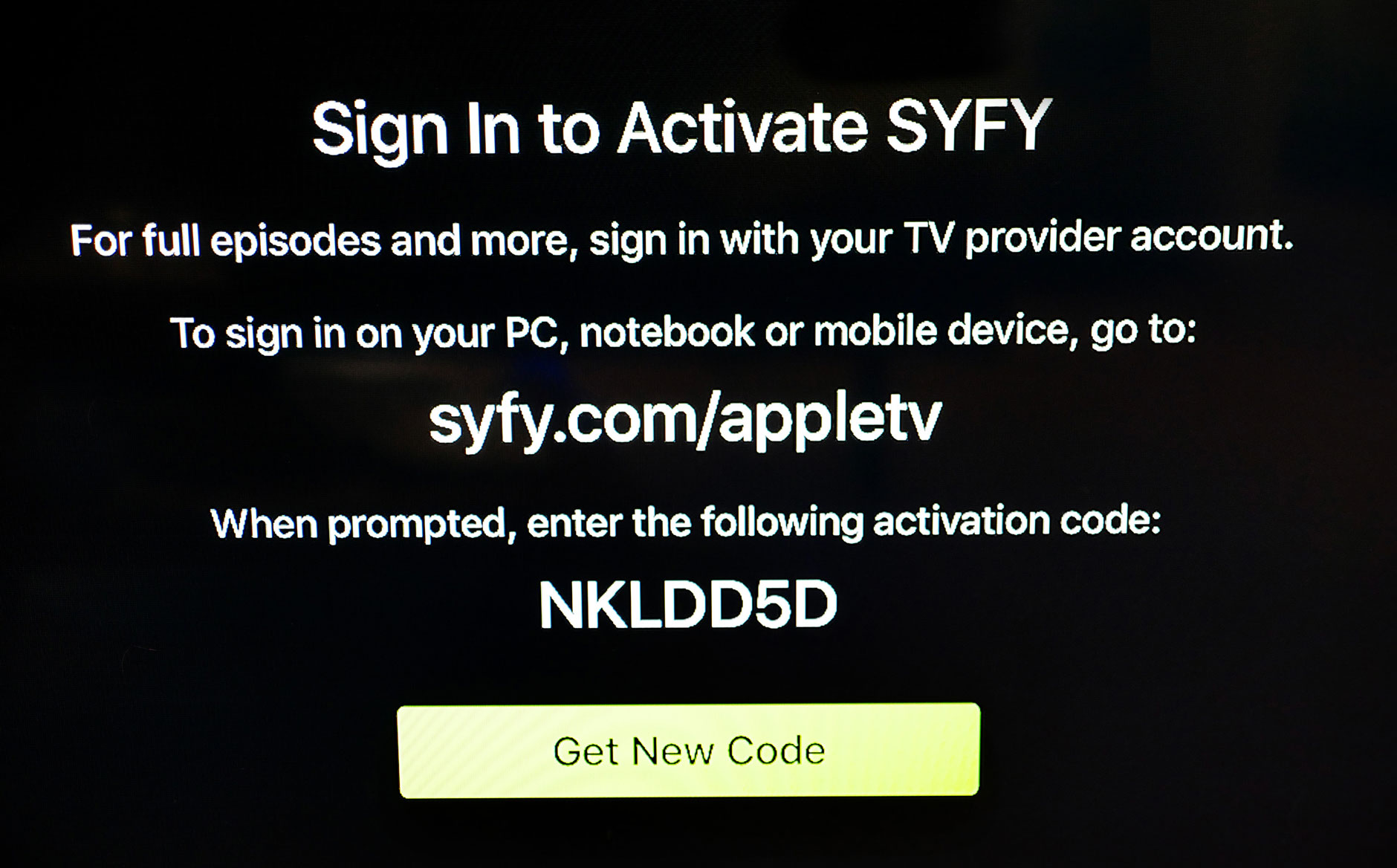
You may not have heard of the Device Flow before, but you’ve probably used it if you have an Apple TV, Roku or Amazon FireTV! The OAuth 2.0 Device Flow is used to log in to a device using OAuth when the device doesn’t have a browser, or also when the device has limited keyboard input ability. The Apple TV is a great device, but it’s missing a browser, which means it can’t do a...
Create a Secure Spring REST API

“If it is useful, it will be modified.” Those words of wisdom came from a QA teacher of mine, to explain that all software evolves when it becomes useful to someone, and for as long as it is useful. We all know this. Users ask us for new features, bug fixes and changes in domain logic every day. As any project (especially a monolith) grows it can begin to become difficult to maintain, and the...
OAuth 2.0 for Native and Mobile Apps

These days, when you hear someone talking about OAuth, it is likely they mean OAuth 2.0. Previous versions of the standard are deprecated. OAuth is an authorization framework that enables you to work with external systems in a secure way using digital identifiers called tokens. One type of token is called an access token. Its function is to allow you to exercise APIs securely. The API service can use the access token to determine if...
Angular 7: What's New and Noteworthy + OIDC Goodness

Angular 7 was released earlier this quarter and I’m pumped about a few of its features. If you’ve been following Angular since Angular 2, you know that upgrading can sometimes be a pain. There was no Angular 3, but upgrading to Angular 4 wasn’t too bad, aside from a bunch of changes in Angular’s testing infrastructure. Angular 4 to Angular 5 was painless, and 5 to 6 only required changes to classes that used RxJS....
Spring Boot 2.1: Outstanding OIDC, OAuth 2.0, and Reactive API Support

Spring Boot 2.1 was recently released, eight months after the huge launch of Spring Boot 2.0. The reason I’m most excited about Spring Boot 2.1 to me is its improved performance and OpenID Connect (OIDC) support from Spring Security 5.1. The combination of Spring Boot and Spring Security has provided excellent OAuth 2.0 support for years, and making OIDC a first-class citizen simplifies its configuration quite a bit. For those that aren’t aware, OIDC is...
Build a Web App with Spring Boot and Spring Security in 15 Minutes
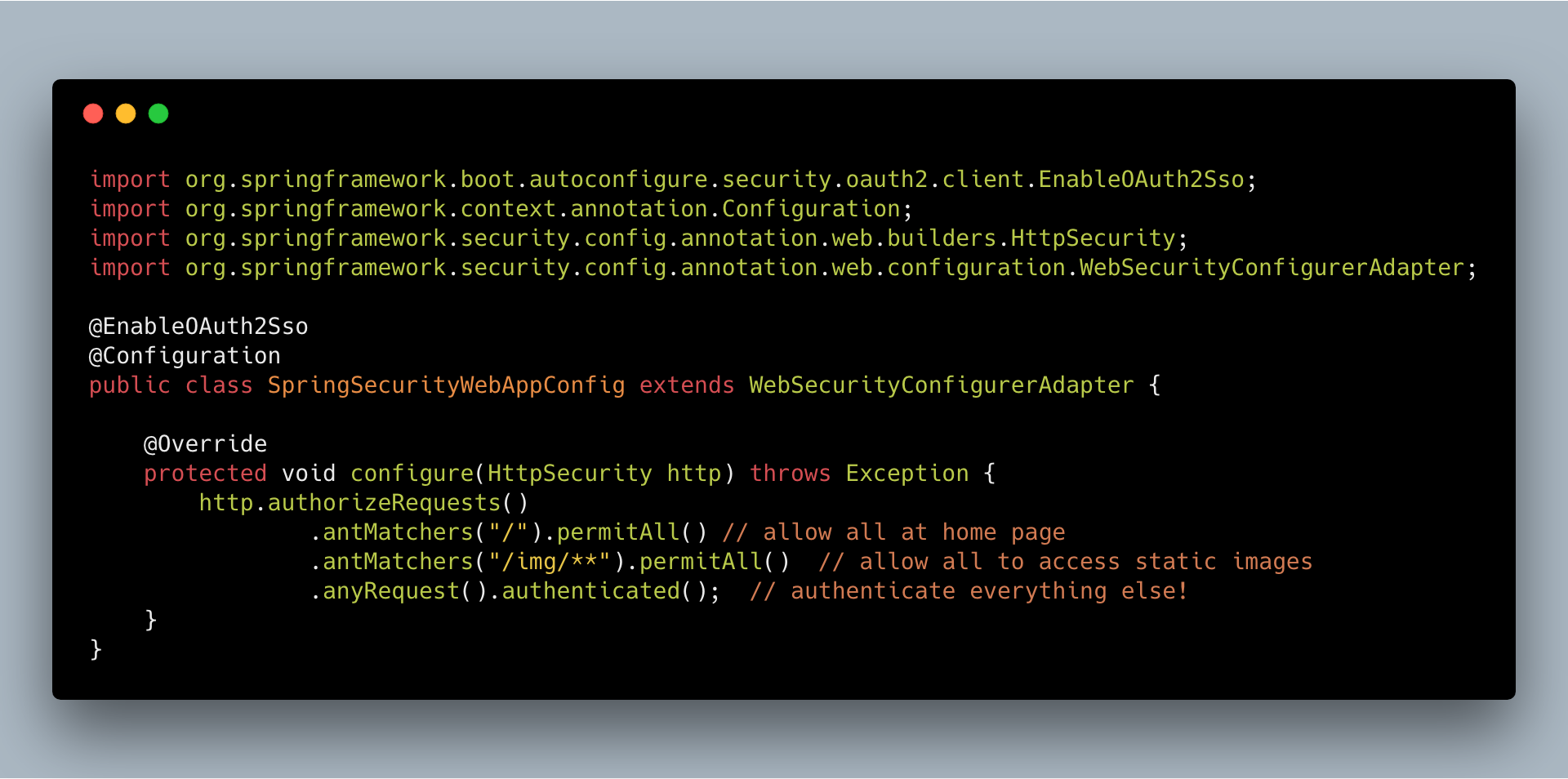
Developers know that securing web apps can be a pain. Doing it right is tough. The worst part is that “right” is a moving target. Security protocols change. Vulnerabilities are found in dependencies and patches are released. Tons of often complex boilerplate code has to be generated. The software-as-service paradigm has proliferated over the last decade, and while I love reinventing the wheel as much as the next developer (because, clearly, I’m gonna write it...
Build a Simple REST API with Node and OAuth 2.0
JavaScript is used everywhere on the web - nearly every web page will include at least some JavaScript, and even if it doesn’t, your browser probably has some sort of extension that injects bits of JavaScript code on to the page anyway. It’s hard to avoid in 2018. JavaScript can also be used outside the context of a browser, for anything from hosting a web server to controlling an RC car or running a full-fledged...
Secure Server-to-Server Communication with Spring Boot and OAuth 2.0
Most OAuth 2.0 guides are focused around the context of a user, i.e., login to an application using Google, GitHub, Okta, etc., then do something on behalf of that user. While useful, these guides ignore server-to-server communication where there is no user and you only have one service connecting to another one. The OAuth 2 client credentials grant type is exclusively used for scenarios in which no user exists (CRON jobs, scheduled tasks, other data...
Build a Basic CRUD App with Vue.js and Node
I’ve danced the JavaScript framework shuffle for years starting with jQuery, then on to Angular. After being frustrated with Angular’s complexity, I found React and thought I was in the clear. What seemed simple on the surface ended up being a frustrating mess. Then I found Vue.js. It just felt right. It worked as expected. It was fast. The documentation was incredible. Templating was eloquent. There was a unanimous consensus around how to handle state...
Secure a Spring Microservices Architecture with Spring Security and OAuth 2.0

Building a microservices architecture with Spring Boot and Spring Cloud can allow your team to scale and develop software faster. It can add resilience and elasticity to your architecture that will enable it to fail gracefully and scale infinitely. All this is great, but you need continuous deployment and excellent security to ensure your system stays up-to-date, healthy, and safe for years to come. With Spring Security and its OAuth 2.0 support, you have everything...
Secure your SPA with Spring Boot and OAuth
If you have a JavaScript single-page application (SPA) that needs to securely access resources from a Spring Boot application, you likely want to use the OAuth 2.0 implicit flow! With this flow your client will send a bearer token with each request and your server side application will verify the token with an Identity Provider (IdP). This allows your resource server to trust that your client is authorized to make the request. In OAuth terms...
Play Zork, Learn OAuth
In the early ’80s, some of the best “video” games were text-based adventures. These games would print out descriptive text of your surroundings and you would interact with the game using simple, but natural language commands like: “go north” or “take sword”. Fast forward some 30 years and a specification for an authorization framework called OAuth 2.0 was published. This framework allows an application to receive a token from an external party (like Okta) that...
Add Role-Based Access Control to Your App with Spring Security and Thymeleaf
User management functions are required by a wide variety of apps and APIs, and it’s a common use-case to partition access to parts of an application according to roles assigned to a user. This is the basis of role-based access control (RBAC). Okta manages these roles with groups. Users can belong to one or more groups. With the Okta Spring Security integration, these groups are automatically mapped to roles that can be called out in...
What's in a Token? – An OpenID Connect Primer, Part 3 of 3
In the previous two installments of this OpenID Connect (OIDC) series, we dug deep into the OIDC flow types and saw OIDC in action using a playground found at: https://okta-oidc-fun.herokuapp.com/. In this third and final installment, we’ll look at what’s encoded into the various types of tokens and how to control what gets put in them. JWTs, have the benefit of being able to carry information in them. With this information available to your app...
OIDC in Action – An OpenID Connect Primer, Part 2 of 3
In the first installment of this OpenID Connect (OIDC) series, we looked at some OIDC basics, its history, and the various flow types, scopes, and tokens involved. In this post, we’ll dive into the mechanics of OIDC and see the various flows in action. The token(s) you get back from an OIDC flow and the contents of the /userinfo endpoint are a function of the flow type and scopes requested. You can see this live...
Identity, Claims, & Tokens – An OpenID Connect Primer, Part 1 of 3
In the beginning, there were proprietary approaches to working with external identity providers for authentication and authorization. Then came SAML (Security Assertion Markup Language) – an open standard using XML as its message exchange type. Then, there was OAuth and OAuth 2.0 – also open as well as being a modern, RESTful approach to authorization using JSON as its medium. And now, the holy grail of “secure delegated access” OpenID Connect (henceforth OIDC), which runs...
What the Heck is OAuth?
There’s a lot of confusion around what OAuth actually is. Some people think OAuth is a login flow (like when you sign into an application with Google Login), and some people think of OAuth as a “security thing”, and don’t really know much more than that. I’m going to show you what OAuth is, explain how it works, and hopefully leave you with a sense of how and where OAuth can benefit your application. What...