Spring Native in Action with the Okta Spring Boot Starter

In the fall of 2020, the Spring team released a new experimental Spring Native project that gave Spring developers hope for faster startup times. Spring Native is all about converting your Spring applications to native executables. It leverages GraalVM to make it happen. This announcement was huge because the new kids on the block, Micronaut and Quarkus, produced native executables by default. I was really excited about Spring Native when I first heard about it....
How to Write Cleaner, Safer Code with SonarQube, Docker and .NET Core

When it comes to code quality and code security, SonarQube is your teammate! This analysis tool is pretty straightforward to use, especially with some help from Docker. In this post, I’ll show you how to run a Docker container with SonarQube to analyze the code of a simple ASP.NET Core 3.0 application. Code analysis is a critical component of app development because it can identify security issues and other tricky bugs that might be overlooked...
How to Build a Flask SCIM Server Configured for Use with Okta

At a very high level, the SCIM (System for Cross-Identity Management) protocol exists to provision and sync users and groups across various, independent systems. There is some room for nuance in the SCIM spec. In this post we will take a look at some basic SCIM operations. We’ll peek under the hood at the flow between Okta and a SCIM server built in Flask using PostgreSQL as our app database. Even if you’re not a...
Developer Day 2021: Celebrating the Future of Identity

It’s been a big year for Okta and Auth0. Our two companies have officially joined forces over the past few months, and we are excited about the chance to shape the future of identity together. It’s great to celebrate our combined developer communities at the first Developer Day event. I look forward to exploring more ways we can collaborate with our Auth0 counterparts and far-flung global communities through future events and activities. On Tuesday, 8/24,...
Command Line Login with the OAuth Device Grant

Even if you’ve never heard of the OAuth 2.0 Device Authorization Grant, formerly known as the Device Flow, you’ve probably seen it in action on a smart TV or other streaming device. The Device Authorization Grant is commonly used on devices with limited keyboard input ability. The process allows you to log in to an account more easily via a separate browser on your laptop, mobile phone, or other companion rich-input device. For instance, if...
Centralize Authentication at the Gateway with Apache APISIX and OpenID Connect

Apache APISIX is a dynamic, real-time, high-performance API gateway, providing rich traffic management. The project offers load balancing, dynamic upstream, canary release, circuit breaking, authentication, observability, and many useful plugins. In addition, the gateway supports dynamic plugin changes along with hot-plugging. The OpenID Connect plugin for Apache APISIX allows users to replace traditional authentication mode with centralized identity authentication mode via OpenID Connect. NOTE: This post originally appeared on the Apache APISIX blog. Table of...
How to Prevent Reactive Java Applications from Stalling

Modern applications must work smoothly on high loads and with a high number of concurrent users. Traditional Java applications run blocking code and a common approach for scaling is to increase the number of available threads. When latency comes into the picture, many of these additional threads sit idle, wasting resources. A different approach increases efficiency by writing asynchronous non-blocking code that lets the execution switch to another task while the asynchronous process completes. Project...
Join the Okta Identity Engine Early Access Hackathon 2021 Challenge

Amaze us! Build something unique and wonderful with early access to our new Okta Identity Engine Limited GA release. Here’s how you can get involved. You’re invited to participate in the Okta Identity Early Access Hackathon, which is happening now! Our virtual hackathon began on August 3 and will run till September 14, 2021. You still have more than a month to take the new Okta Identity Engine (OIE) out for a spin and share...
Using AWS Toolkit for Visual Studio

Amazon Web Services is one of the most popular cloud computing platforms on the planet. There’s a good chance you will need to work in an AWS environment, which means publishing to one of their web server services like Elastic Beanstalk. The AWS platform is enormous, and this can be an intimidating task for a developer. Luckily, Amazon has released their AWS Toolkit for Visual Studio 2013-2015 and AWS Toolkit for Visual Studio 2017-2019, which...
Web Forms Migration to Blazor in .NET Core
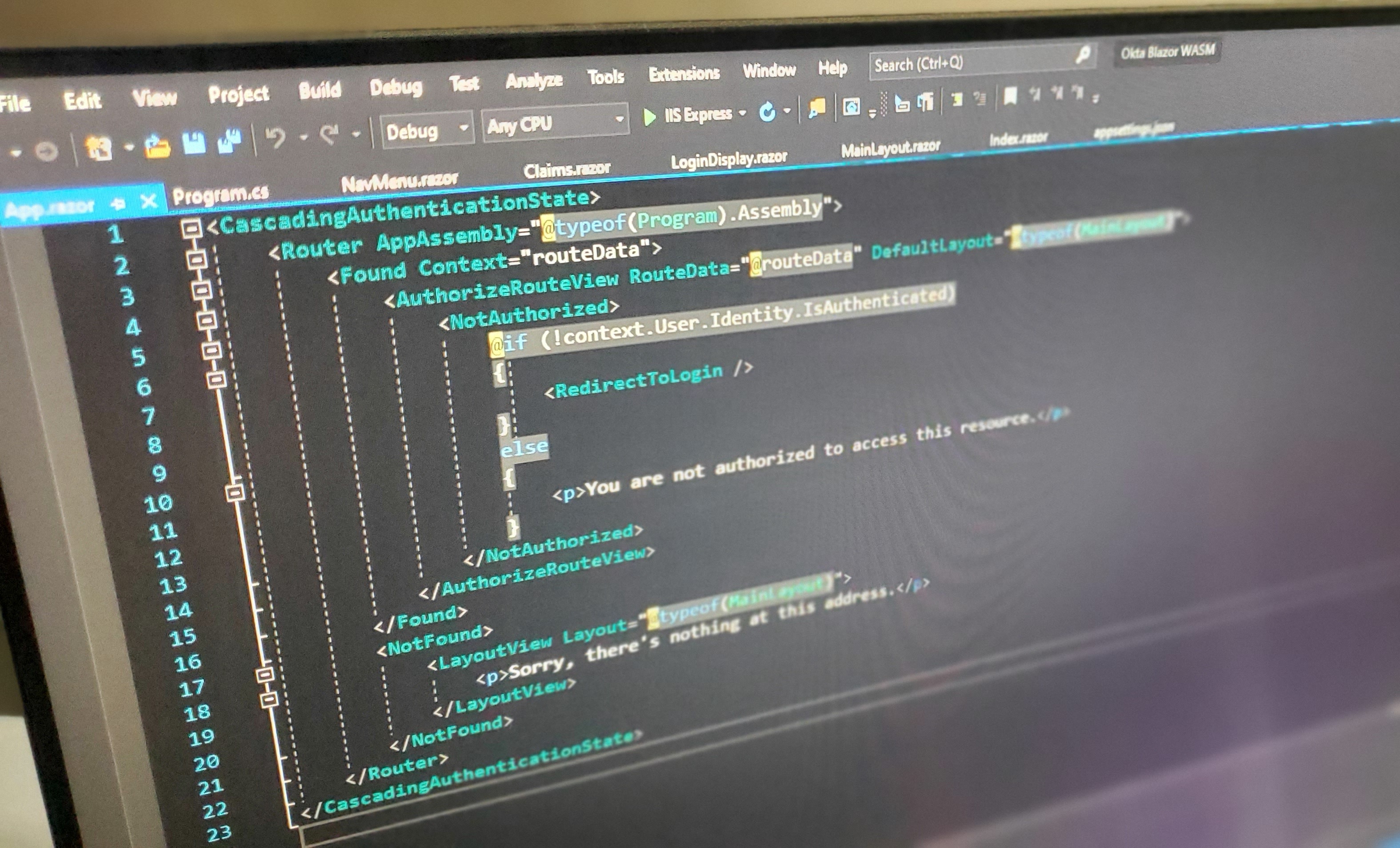
ASP.NET Web Forms framework has been the cornerstone technology of .Net for web development since the release of .Net Framework in 2002. ASP.NET Web Forms includes a layer of abstraction for developers so that you don’t need to care about HTML, JavaScript, or any other front-end technology. It provides a development flow similar to building desktop apps, a way for developers to build a web page by drag and drop, an event-driven programming model, and...