Security.txt: Make Vulnerabilities Easier to Report
We all know that all software has bugs and that security is hard, but somehow we are still surprised when we see new vulnerabilities. Vulnerability A bug, flaw, weakness, or exposure of an application, system, device, or service that could lead to a failure of confidentiality, integrity, or availability. In 2020, there were 18,395 vulnerabilities reported, which means about 50 new vulnerabilities are reported every day. These numbers only include what has been reported to...
An Overview of Best Practices for Security Headers

Many decisions go into the process of creating a secure website. One of these decisions is selecting which HTTP security headers to implement. Today, we’ll dive into the most important HTTP security headers and the best practices that will strengthen your website’s security. Table of Contents The Security Headers HTTP Strict Transport Security (HSTS) Content-Security-Policy (CSP) X-XSS-Protection X-Frame-Options Referrer-Policy X-Content-Type-Options Permissions-Policy Configuring a Security Header Nginx Apache IIS Firebase Learn More About Security Headers The...
Spreading Some Okta Love to the DevOps World

Hello Oktaverse! So finally, I have landed at Okta on my second attempt 😉. I’m so excited about this new chapter in my career journey and can’t wait to see what’s in store. But first, introductions. Who am I I’m from the south of India, a village in Kerala to be specific, but I grew up in Chennai since my parents moved there looking for work when I was 12. I like to call myself...
From Ops To Advocacy

Hi, I’m edunham, and I’m an infra person. Our buzzwords include DevOps, Cloud Operations, and Site Reliability Engineering, though if you ask any two of us about the difference between those terms, you’ll get at least three answers. Whatever name it’s wearing, doing ops well requires not only the “how” of changing systems, but also the “why” of making the right changes. Although I’ve always loved helping spread the information that my colleagues need in...
Secure Access to AWS EKS Clusters for Admins
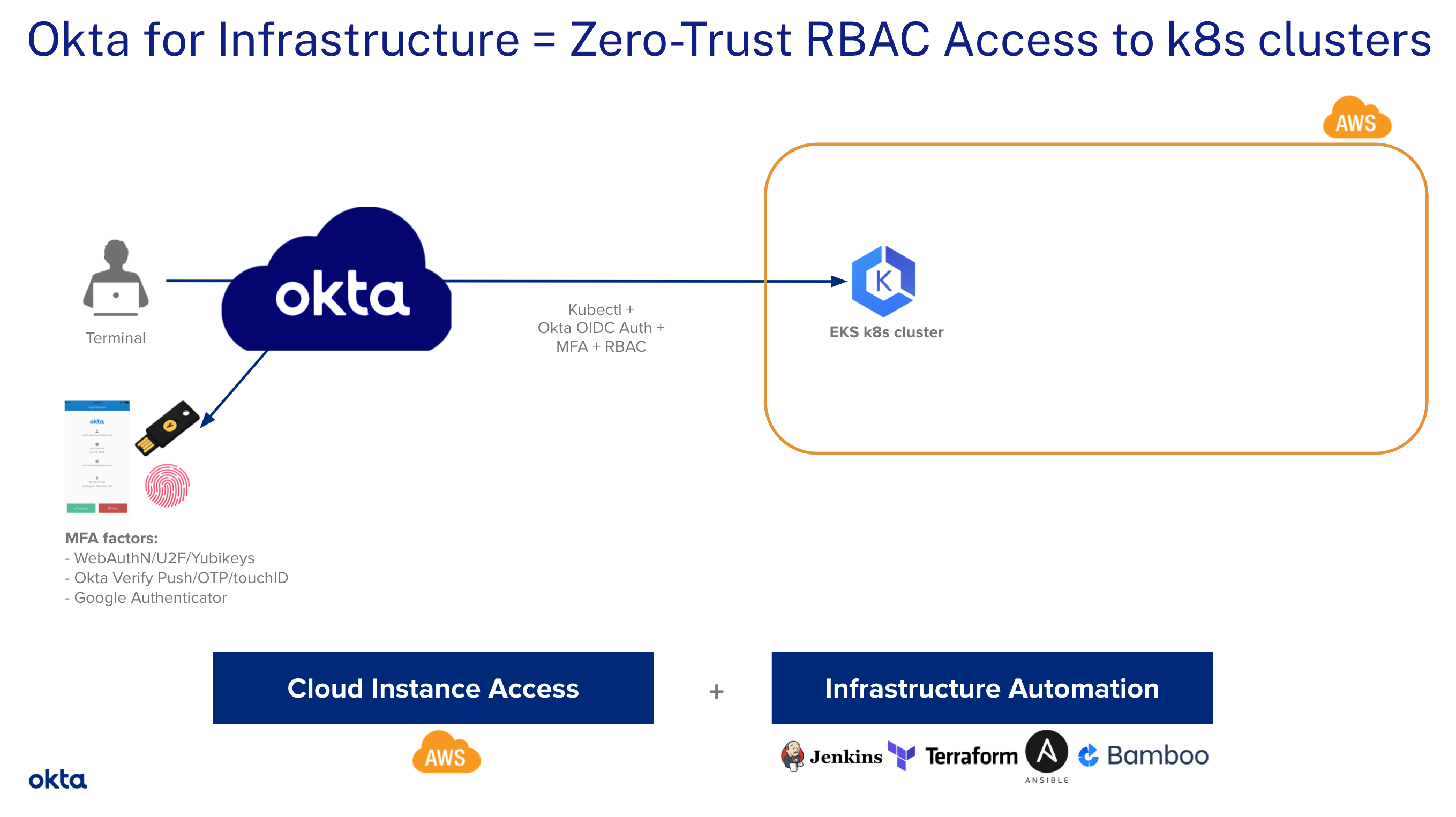
In this tutorial, we will leverage OpenID Connect (OIDC) to allow our DevOps team to securely access their EKS clusters on AWS. We use Role Based Access Control (RBAC)] to enforce the least privilege required without the need to configure AWS IAM roles. 😎 We’ll highlight the steps to manually enable an OIDC provider on your EKS clusters. At the end of this tutorial, we’ll point to resources you can leverage to automate all those...
Okta Developer Plan Changes

An Update on Our Developer Offering As many of you may know, Okta completed the acquisition of Auth0 in May of 2021. We’ve since been busy, working out how our products will work together to help developers provide the best experiences for their users. If you joined us for Developer Day, you saw Okta and Auth0 showcase interesting projects happening at our companies and in our communities. In the months since the Auth0 acquisition, one...
Learn How to Build a Single-Page App with Vue and Spring Boot

In this tutorial, you are going to create a single-page application (SPA) that uses a Spring Boot resource server and a Vue front-end client. You’ll see how to configure Spring Boot to use JSON Web Tokens (JWT) for authentication and authorization, with Okta as an OAuth 2.0 and OpenID Connect (OIDC) provider. You’ll also see how to bootstrap a Vue client app with the Vue CLI and how to secure it using the Okta Sign-In...
Session Clustering for OAuth 2.0 Applications

A common OAuth 2.0 question we get: "How do I deal with OAuth in a load-balanced application?" The short answer: There’s nothing specific about session clustering for OAuth. The longer answer is—you likely still need to worry about cluster session management. This post will discuss how an OAuth login relates to your application’s session. And we’ll build a simple, secure, load-balanced application to demonstrate. Note: In May 2025, the Okta Integrator Free Plan replaced Okta...
Announcing the Okta Identity Early Access Hackathon Winners

Back in early August, in partnership with DevPost, we announced the Okta Identity Early Access Hackathon, and invited developers everywhere to "build something awesome with the Okta Identity Engine (OIE) Limited GA release." Our aim was to give participants the chance to explore the new platform with its new capabilities for customer identity and access management. In exchange, we hoped to gain early stage feedback and a feel for what engaged the dev community worldwide....
Spring Native in Action with the Okta Spring Boot Starter

In the fall of 2020, the Spring team released a new experimental Spring Native project that gave Spring developers hope for faster startup times. Spring Native is all about converting your Spring applications to native executables. It leverages GraalVM to make it happen. This announcement was huge because the new kids on the block, Micronaut and Quarkus, produced native executables by default. I was really excited about Spring Native when I first heard about it....