Set Up the Private Key JWT Flow in Three Python Commands

The Private Key JWT flow is one of the more complicated OIDC flows to set up. At Okta, it’s commonly used to get OAuth4Okta access tokens which enable you to perform managementr tasks on your org. If you already know HOW it works and just want to get to the code, click here to skip ahead. If you’re looking to gain a better understanding of how it works, here’s a high level explanation: Once you’ve...
Native SSO: Desktop and Mobile Apps Single Sign-On

When you hear SSO (Single Sign-On), you probably immediately think of web apps, and how you only need to sign into one web app first, then all other web apps give you seamless access. Unfortunately, for desktop and mobile applications (often referred to as “native apps”), the seamless web SSO experience (also referred to as native SSO) has not caught on. This is partly due to the lack of an industry standard or best practice...
What You Need to Know about Angular v13

Angular v13 has arrived! And with it come a lot of exciting new features and updates. Angular continues to improve runtime performance, decrease compilation time, promote good software development practices, enhance developer experience, and keep up to date with dependencies such as TypeScript and RxJS. Is anyone else excited about RxJS v7?! 🤩 Let’s take a look at a few of the many new exciting features in Angular v13 with some code examples using authentication....
How to Secure Your Kubernetes Cluster with OpenID Connect and RBAC
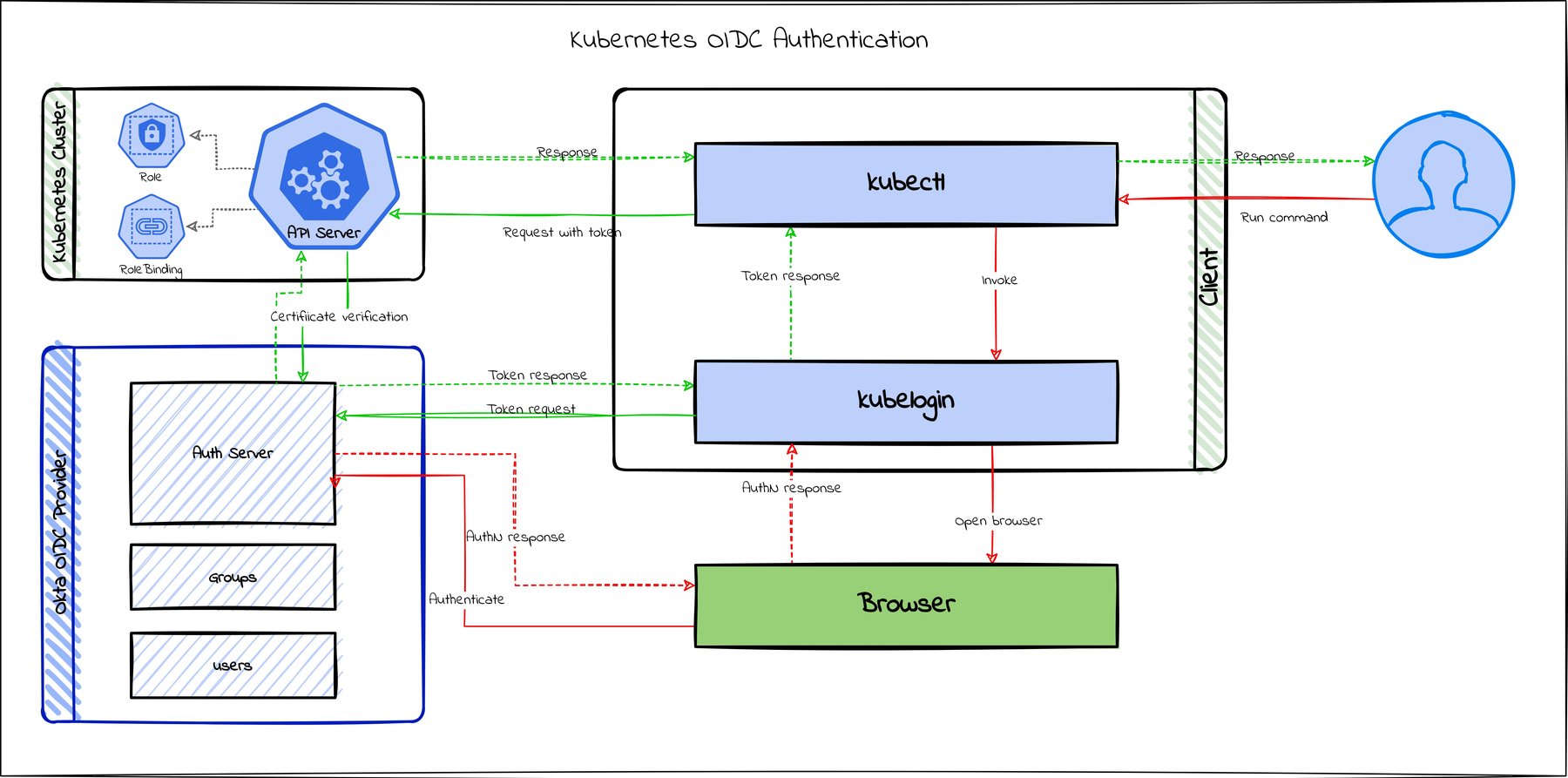
A Kubernetes (k8s) cluster comprises worker machines called nodes and a control plane consisting of the API server, scheduler, etcd, controller manager, and in the case of a PaaS (platform as a service), the cloud controller manager. The containers deployed to the cluster run in pods on the worker nodes. At the same time, the control plane takes care of scheduling, responding to requests, and managing the cluster. When you communicate with a Kubernetes cluster,...
Java Records: A WebFlux and Spring Data Example

When defining classes for a simple aggregation of values, Java developers have traditionally relied on constructors, accessors, equals(), hashCode() and toString(), an error-prone practice that has low value and shifts the focus away from modeling immutable data. Java records were introduced as a first preview in JDK 14 in order to simplify how we write data carrier classes. The second preview came in JDK 15 and the finalized feature arrived in JDK 16. A summary...
Kubernetes To The Cloud With AWS: Deploying a Node.js App to EKS

Since 2013 when it was released to the public, Docker has become an industry-standard tool for development teams to package applications into small executable containers. A year later, Kubernetes was released by Google to manage large amounts of containers, and provide features for high availability (HA) and auto-scaling. While Kubernetes adds many benefits to your container management, you might find the process of setting up Kubernetes within your on-premise infrastructure quite challenging, especially on the...
Build a Secure SPA with React Routing
When building an SPA (single page application) with React, routing is one of the fundamental processes a developer must handle. React routing is the process of building routes, determining the content at the route, and securing it under authentication and authorization. There are many tools available to manage and secure your routes in React. The most commonly used one is react-router. However, many developers are not in a situation where they can use the react-router...
The Things to Keep in Mind about Auth
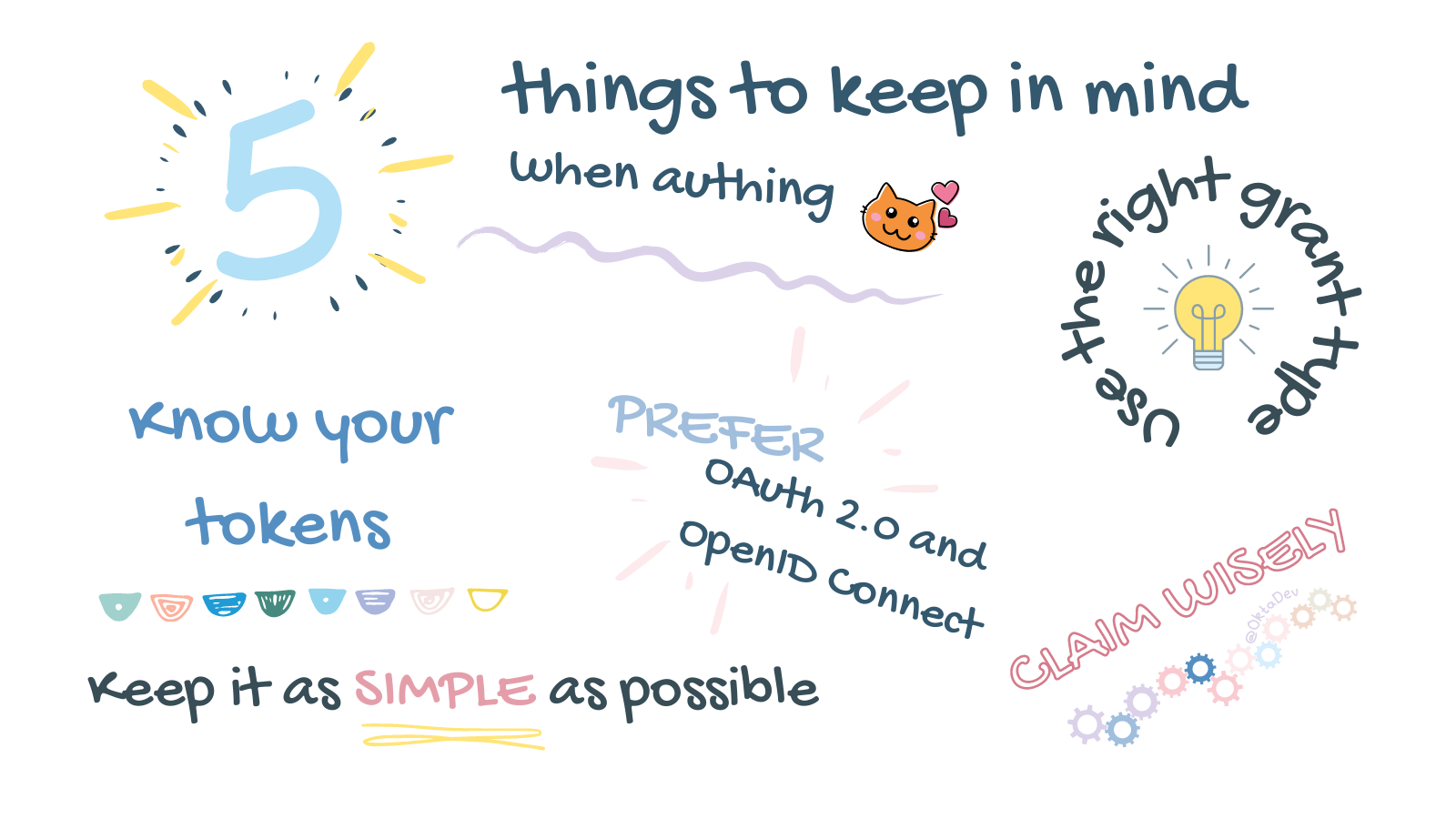
There’s a lot of information out there about adding authentication to your app, which is helpful! But also overwhelming. It can be hard to find relevant and up-to-date information. Security best practices and technologies change, so refreshing your understanding and keeping up with current best practices is a good thing. Here are some notes I took while I reviewed my knowledge and applied my experience implementing auth. Prefer OAuth 2.0 and OpenID Connect If you’re...
Oktanaut Tanay, Reporting for Duty

Greetings Oktaverse! I’m Tanay 🖖 I have been following Okta for many years, and I am very excited to finally join you all and get a chance to serve this wonderful community. First things first, here’s a picture of me so that you can recognize me and say hi the next time we meet. 👇 Who I am and what I’ve done so far I started my journey into the world of tech communities and...
A Quick Guide to Angular and GraphQL
Over the past five years, GraphQL has established itself as the most popular alternative to REST APIs. GraphQL has several advantages over traditional REST-based services. First of all, GraphQL makes the query schema available to the clients. A client that reads the schema immediately knows what services are available on the server. On top of that, the client is able to perform a query on a subset of the data. Both of these features make...