Authentication Patterns for PHP Microservices

Microservices are an increasingly popular architecture, as they allow you to split application development into smaller, easier-to-manage pieces. However, microservices introduce complexity when it comes to implementing authentication. Generally, you only need to worry about one point of ingress for auth with a traditional monolithic application. Still, there are multiple ways to set things up with microservices and just as many authentication patterns to suit. In this tutorial, you’ll see how to build a small...
Happy Holidays!

As the holiday season gets into full swing, the Developer Advocacy team at Okta has sat down around our virtual table to chat about things we’re grateful for across our various technical communities. Deepu: I’m so thankful for Linux accepting Rust as another language for the Kernel and I’m thankful for all the backing it is getting from big names. I’m sure this will lead to Linux becoming more secure as more and more code...
Build and Secure GraphQL APIs with Laravel
GraphQL’s popularity has grown among frontend and backend developers alike. It allows frontend teams to request only the data they need while preventing an explosion of backend endpoints, since all operations can go through one simple endpoint for all models being worked on. In this tutorial, you will learn how to set up a GraphQL API with Laravel, a free open-source PHP web application framework. You’ll then secure the API so that it’s only accessible...
What We Learned About Game Security at PAX West 2021
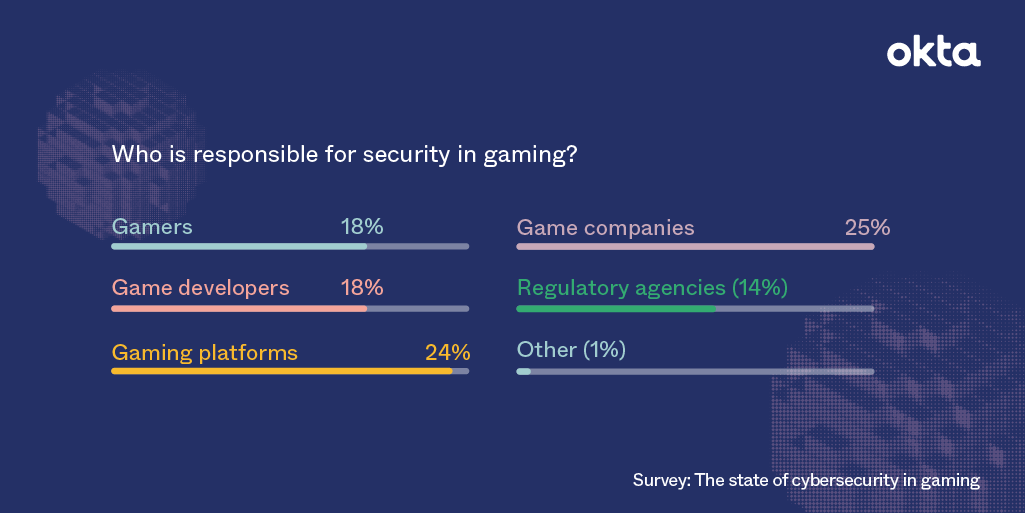
When it comes to security, there seems to be a disconnect in gaming. Where other industries have embraced an all-for-one and one-for-all approach to combating security threats, most gaming and entertainment companies seem largely happy to go it alone. This isn’t just conjecture. At Okta, we were curious about how developers and gaming companies approached security, so this past autumn we decided to take advantage of the return of PAX West, Penny Arcade’s iconic gaming...
Five Anti-Patterns with Secrets in Java

Most applications require some sort of secret or password to enable access: database connection info, API keys, OAuth client secrets, and JWT keys, to list some examples. Dealing with secrets in your projects is always a chore, and it’s often done wrong. In this post, I’ll describe five common problems, which you can think of as anti-patterns (the opposite of a best practice) and I’ll offer suggestions to help you avoid these issues. Table of...
Loading Components Dynamically in an Angular App

Businesses have unique and complex needs. In addition to the user or organization-specific data to show, there might be a need to display different views and content conditionally. The conditions might include the user’s role or which department they belong to. The information about a user might be part of the authenticated user’s ID token as a profile claim. In Angular, you can show different components or even parts of templates conditionally using built-in directives...
Build an Electron App with JavaScript and Authentication

Electron is one of the most popular desktop frameworks today. Electron uses HTML, JavaScript, and CSS for its front end and Node.js for its backend. This design enables developers to quickly write and easily maintain cross-platform applications between their desktop and web applications. Since Electron uses Node on the backend, it also has access to the entire npm ecosystem that Node developers have come to rely on. Even though it is built on Node, Electron...
How to Secure Your Kubernetes Clusters With Best Practices
Kubernetes has become an unavoidable part of a software infrastructure these days. If you are an enterprise or medium/large company, chances are you are already running Kubernetes clusters for your workloads. If you are a DevOps engineer, there is a good chance you are maintaining either an on-prem Kubernetes cluster or a PaaS like Amazon EKS, Microsoft AKS, or GKE. But regardless of how you run your Kubernetes clusters, you need to make sure that...
Full Stack Java with React, Spring Boot, and JHipster

If you search for “Full Stack Java” on the internet, you’ll likely find a lot of recruiting, courses, and jobs. Being a full stack developer can be exciting because you can create the backend and frontend of an app all by yourself. There is business logic and algorithms as well as styling, making things look good, and securing everything. It also pays pretty well. Today, I’m going to show you how you can be a...
Getting to Know GooseClip: Interview with an Okta Hackathon Winner

Okta Early Access Hackathon revisited In August, Okta’s developer relations team invited intrepid developers to participate in the virtual Okta Identity Engine Early Access Hackathon, and challenged them to build a working app with our limited availability new customer identity and access management (CIAM) platform. A month or so after, judges convened, winners were announced, and thousands of dollars in prizes were distributed. Kudos to hundreds of participants, and props to all involved. In October,...