Build Single Sign-on for Your ASP.NET MVC App

So you’re interested in using single sign-on (SSO) for your ASP.NET MVC apps? You’ve come to the right place. There are lots of reasons for using SSO for custom apps owned by the same organization. Better user experience. Less development time. Improved security. Those are all great reasons. Another thing I love about SSO is that it can enable upgrading a large codebase a piece at a time instead of all at once. How so?...
10 Myths About Java in 2019

Java turned 24 years old on May 23, 2019. That’s pretty old for a programming language. The fact that it’s still widely used and runs many of the world’s largest organizations is nothing short of incredible. But it has a unique impression problem among languages in that it means two very distinct things: Java the language and Java the runtime. Many developers, of course, think Java is old and therefore shouldn’t be used. And yet...
Secure Your ASP.NET Core App with OAuth 2.0

Do you ever wish you had a virtual scrap of paper you could use to write notes in the cloud? I’ll show you how to build a simple ASP.NET Core app to keep track of your notes, plus how to use .NET Core’s OAuth 2 authentication middleware to secure access to your app so your personal notes are kept private. Note: In May 2025, the Okta Integrator Free Plan replaced Okta Developer Edition Accounts, and...
Use Azure Cosmos DB with Your ASP.NET App

Cosmos DB is a planet-scale database capable of holding billions of records (“documents” using Cosmos jargon) without significant detriment to performance. In this article, you will learn how to use Azure Cosmos DB - a key-value store solution - your ASP.NET app instead of a relational database. To demonstrate their differences, check out a simple example query using both a relational database and Cosmos DB. When you query a relational database you get back a...
Build a REST API Using Java, MicroProfile, and JWT Authentication
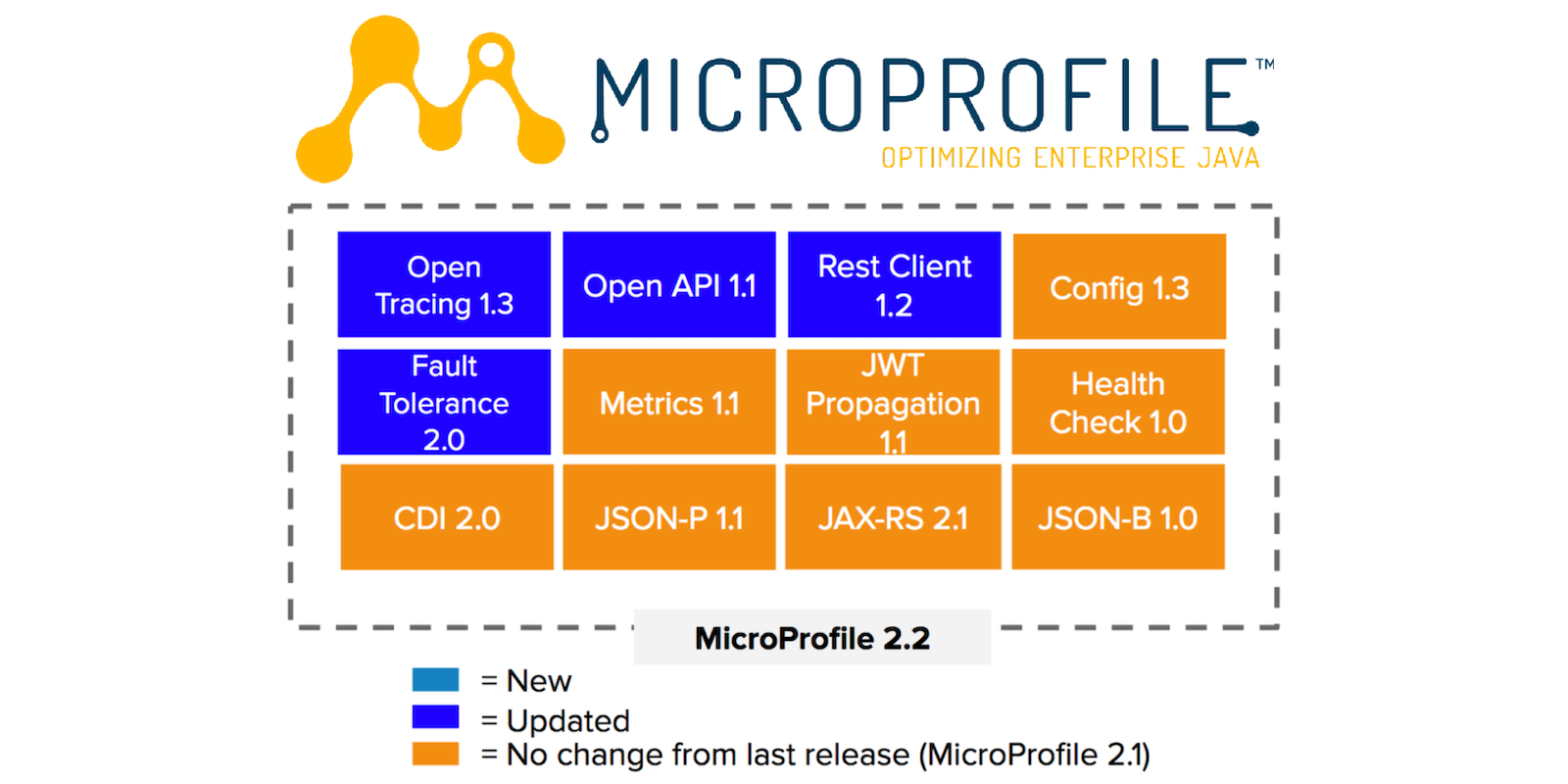
In this post, you will learn how to build a simple REST API using Eclipse MicroProfile and secure it using JSON Web Token (JWT) authentication. You’ll also use a free developer account from Okta to configure an OAuth 2.0 / OpenID Connect (OIDC) application as the OAuth provider, with role-based authorization. That was a lot of jargon. Let’s define a few of the terms (and introduce a few more!). Note: In May 2025, the Okta...
Software Development is a Creative Endeavor

Every time I tell someone I am a software developer, they almost inevitably reply with, “You must be super smart, then.” I don’t feel any smarter than most other people. Truthfully, I feel dumber than most people I meet. To be fair, I do meet a lot of software developers. The preconception is that I am some sort of technical wiz, especially good at math. I assure you I am not. While I have a...
Use Spring Boot and MySQL to go Beyond Authentication

In this post, we will walk through how to build a simple CRUD application using Spring Boot, MySQL, JPA/Hibernate and Okta OpenID Connect (OIDC) Single Sign-On (SSO). The Java Persistence API (JPA) provides a specification for persisting, reading, and managing data from your Java object to relational tables in the database. The default implementation of JPA via Spring Boot is Hibernate. Hibernate saves you a lot of time writing code to persist data to a...
Is GitHub Package Registry the npm Killer?

GitHub recently announced a new feature, GitHub Package Registry, currently in beta. It’s designed to allow GitHub users to publish and distribute packages of their software directly on GitHub instead of relying on an external system. At a glance, GitHub Package Registry has the following features and benefits. Supports multiple package clients: npm, Maven, NuGet, RubyGems, and Docker images Supports public and private packages Supports pre-release packages Can use webhooks and GitHub Actions to customize...
The Top 5 DevOps Automation Tools .NET Developers Should Know
Not too long ago, deployments were done by hand - manually pushed to a physical server somewhere in a building your company owned. The software engineering world has come a long way since then, and we have more options than ever get our code and data live, automatically. Here are a few tools every C#/.NET developer should know that can help with that process, vetted by some of the best software leaders in the business....
Decode JWTs in C# for Authorization

There are two main steps in securing an application: authentication and authorization. Authentication is easy enough. A user enters a username and password (maybe even a second factor) to prove (authenticate) who they are. Authorization is a little less cut and dried. There are lots of factors that go into what an authenticated user is authorized to do. First, you need some information about the user that just authenticated. Many modern web apps use JSON...