Get Groovy with Gradle

In the Java world, there are two main build systems: Gradle and Maven. A build system chiefly manages potentially complex webs of dependencies and compiles the project. It also packages the compiled project along with all the resources and meta files into the final .war or .jar file. For simple builds, the choice between Maven and Gradle is pretty much one of personal taste, or perhaps the taste of your CTO or technical manager. They...
PHP Authorization with OAuth 2.0 and Okta

User account management, authorization, and access control can be difficult to implement for many web developers. At the same time, they are critical cornerstones of application security – any mistake can lead to data leaks, financial losses, and legal troubles. Successful web applications inevitably grow to a stage where simple user authorization is no longer sufficient and certain features have to be made available only to certain users. There are a variety of ways to...
The Best Travel Tips for People In Tech

Here on the Okta Developer Relations team, we travel a lot (like, a lot) and we’ve learned a few things to make it easy. We’ve tried out countless suggestions over the years and I’ve rounded up the very best ones from my team to share with software developers getting their travel groove on. It’s all about making the trip less stressful and more enjoyable, and these tips are sure to get you well on your...
Secure Reactive Microservices with Spring Cloud Gateway
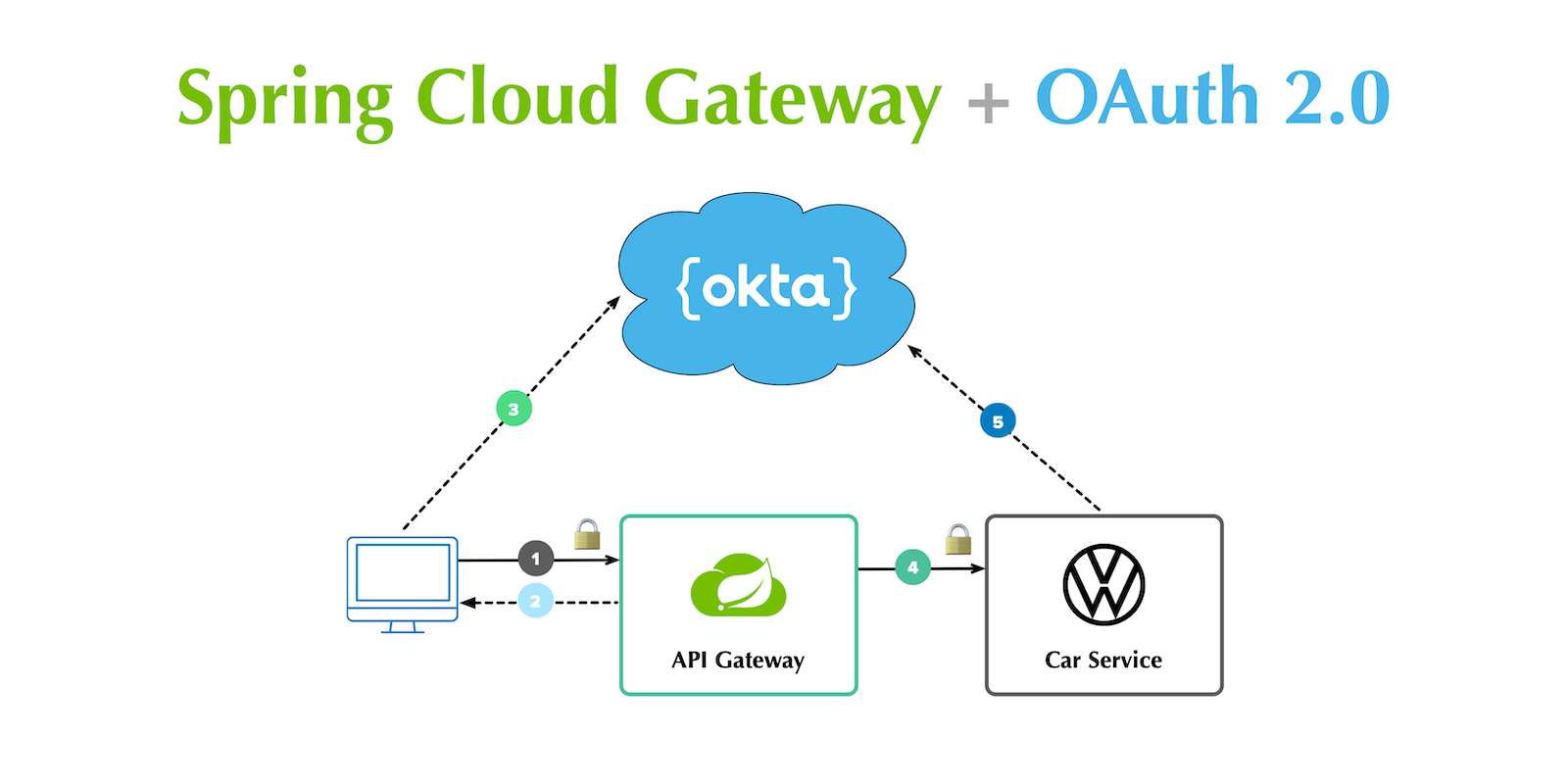
So you wanna go full reactive, eh? Great! Reactive programming is an increasingly popular way to make your applications more efficient. Instead of making a call to a resource and waiting on a response, reactive applications asynchronously receive a response. This allows them to free up processing power, only perform processing when necessary, and scale more effectively than other systems. The Java ecosystem has its fair share of reactive frameworks, including Play Framework, Ratpack, Vert.x,...
5 Minute Serverless Functions in Azure without an IDE

Microsoft Azure makes it incredibly easy to get a basic API/microservice up and running quickly! If you are unfamiliar with building serverless architecture in the Microsoft ecosystem, using Azure Functions has become a quick way to get back-end code up and running that is easy to understand and usable for anyone. In this tutorial, we will set-up an API endpoint using the HTTP Trigger invocation that you can use with any front-end site. I use...
Combat Side-Channel Attacks with Cross-Origin Read Blocking

As if developers didn’t have a big enough task securing web applications from software-layer attacks, they now have to contend with another threat: hardware-layer vulnerabilities. These complex cybersecurity flaws were introduced long before many modern developers began coding and extend from the inner workings of a computer’s silicon to a web application’s code. If exploited, hardware-layer vulnerabilities can result in leaked information from the web browser to an attacker. Luckily, Cross-Origin Read Blocking (CORB) is...
Implement the OAuth 2.0 Authorization Code with PKCE Flow

Imagine two levers that are inversely connected. That is, as one goes up, the other goes down. One lever is User Experience and the other is Security. It’s not a perfect analogy, but most developers can attest that as user experience goes up, security goes down. Take browser history syncing for example. I can start a session with my bank on Firefox mobile and pick up right where I left off on Firefox desktop. From...
Make Java Tests Groovy With Hamcrest

My favorite way to test Java code is with Groovy. Specifically, writing tests in Groovy with Hamcrest. In this post, I’ll walk through how to test a simple Spring Boot application with these tools. Groovy is an optionally typed dynamic language for the JVM, and can be compiled statically. That is a mouthful and I’ll explain this as we go, but for now think of Groovy as Java with lots of sugar. Groovy is a...
Welcome, Brian Demers

I’m excited to announce that I’ve joined Okta’s Developer Relations team! I’ve been working on Okta’s awesome Developer Experience team for the last couple years so I’m not exactly a new face around here. 😉 Who is Brian? As a young kid, I took things apart. Either to see how they worked or just see what was inside. This habit was made worse when I found computers and started fixing them. Anyone else miss the...
How to Work with Angular and MySQL

The MySQL database has been a reliable workhorse for web applications for many years. It is the M in the LAMP stack, and powers a huge number of web servers across the world. MySQL is also a relational database, with data stored in tables with strict data definitions. Rows in tables correspond to data entries and rows in one table can be referenced from another table through their index. Plenty of literature covers the fundamentals...