Performance Testing with Apache Bench

Every web developer I know is concerned with the performance of their web applications. How fast will my app load? Will it handle a lot of users? How well will it lots of data? Will it scale? These are just some of the questions that developers ask themselves but very rarely have any idea how to test. Generally, when performance testing, most developers worry about “load testing”, or how an app will perform under load....
Tutorial: Develop Apps with Secure WebSockets in Java

WebSockets is a modern transport layer technology that establishes a two-way communication channel between a client and a server, perfect for low-latency, high-frequency interactions. WebSockets tend to be used in collaborative, real-time or event-driven applications, where traditional client-server request-response architecture or long polling would not satisfy requirements. Use cases include stock trading and shared dashboard applications. In this tutorial, I’ll give you a quick overview of the WebSockets protocol and how it handles messages with...
Secure and Scalable: An Introduction to JAMStack

If you’re a web developer, chances are you have heard the term “JAMstack.” Curiously, JAMstack isn’t a solution to prevent clogged printers, something to eat on toast, or a way to make music. However, by the time you finish reading this tutorial, you’ll understand JAMstack and its benefits, and learn one approach to implementing JAMstack for yourself. Let’s get ready to JAM. The “JAM” in JAMstack stands for JavaScript, APIs, and Markup. JAMstack’s pattern of...
Painless Node.js Authentication
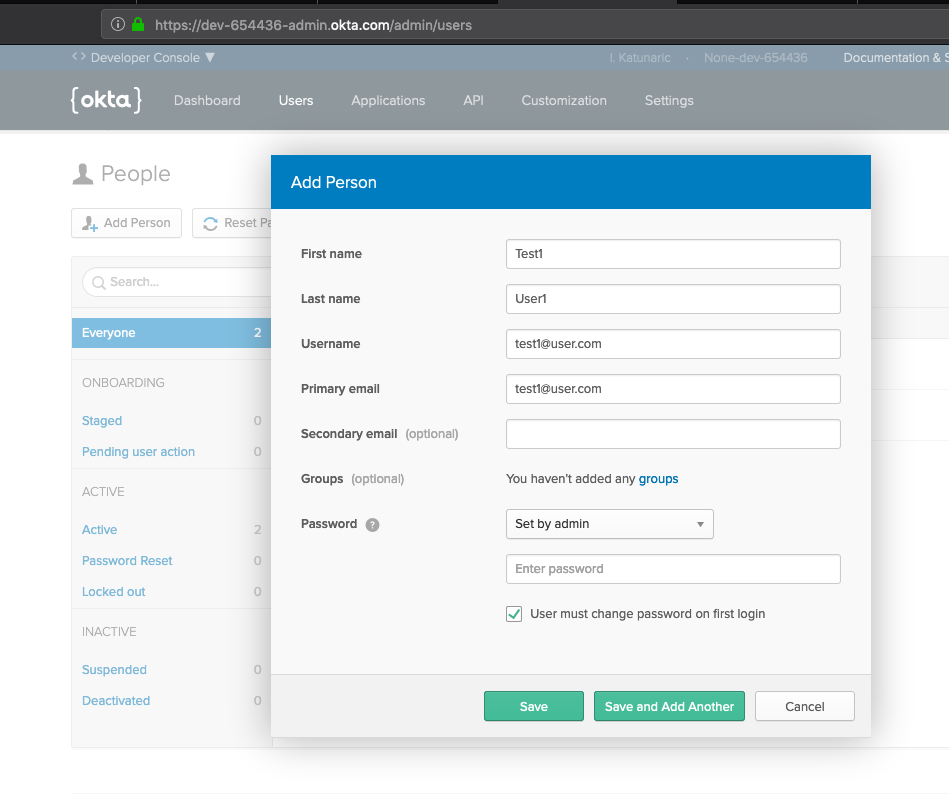
User authentication is a critical component of just about every web application. Unfortunately, while authentication is a core part of all websites, it can still be difficult to get right. Despite the Node.js community being around for a while, there still aren’t a lot of simple, foolproof ways to authenticate users in Node.js applications. In this article I’m going to explain how to build a Node.js application that authenticates users in a best practices way....
JWTs in React for Secure Authentication

Although authentication is a common requirement for web apps, it can be difficult to get it right, especially if you’re by yourself or part of a small team. That’s why many sites choose to use OAuth 2.0 to let a third-party handle authentication for them. They just need to know how to decode a JSON Web Token (JWT), rather than how to store a bunch of user information and pray they aren’t the next company...
How to Develop a Quarkus App with Java and OIDC Authentication

Quarkus is a container-first Kubernetes Java framework designed to have a super-fast start-up time and low memory usage. The container-first strategy emphasizes packaging the runtime environment along with the application code, allowing both to be tightly optimized and avoiding the endless updates and configuration problems that can come along with monolithic server systems. Quarkus was built from the beginning to support compilation to native code for use with Graal/SubstrateVM but also supports the good old...
Build a Simple CRUD App with Java and JSF

JavaServer Faces (JSF) is a Java framework for building Web applications, centered on components as the building blocks for the user interface. JSF benefits from a rich ecosystem of tools and vendors, as well as out of the box components and libraries that add even more power. Why use JSF instead of JavaServer Pages (JSP)? There are two primary reasons: First, JSF has more templating capabilities, since it doesn’t write your view directly as it...
Get Started with the ELK Stack

Good design principles require that microservices architectures are observable, and provide a centralized monitoring tool. This tool allows development teams to verify the overall system health, inspect logs and errors, and get feedback after deployments. So what is the Elastic (or ELK) Stack and why it is an excellent option to meet this need? In this tutorial post, you will learn how to … Set up and run the ELK stack in Docker containers Set...
How to Create a Simple Symfony Application with Authentication

Symfony is not the most popular or loved PHP framework, but it’s arguably the most mature, flexible, and reliable. Since its initial release, Symfony has evolved into a set of loosely-coupled, high-quality components that can be chosen individually or combined to create powerful applications, without the compromise of bloat or huge runtime overhead. These components are also widely used outside the context of the framework, as stand-alone modules or sitting at the bottom of other...
How to Build a Maven Plugin
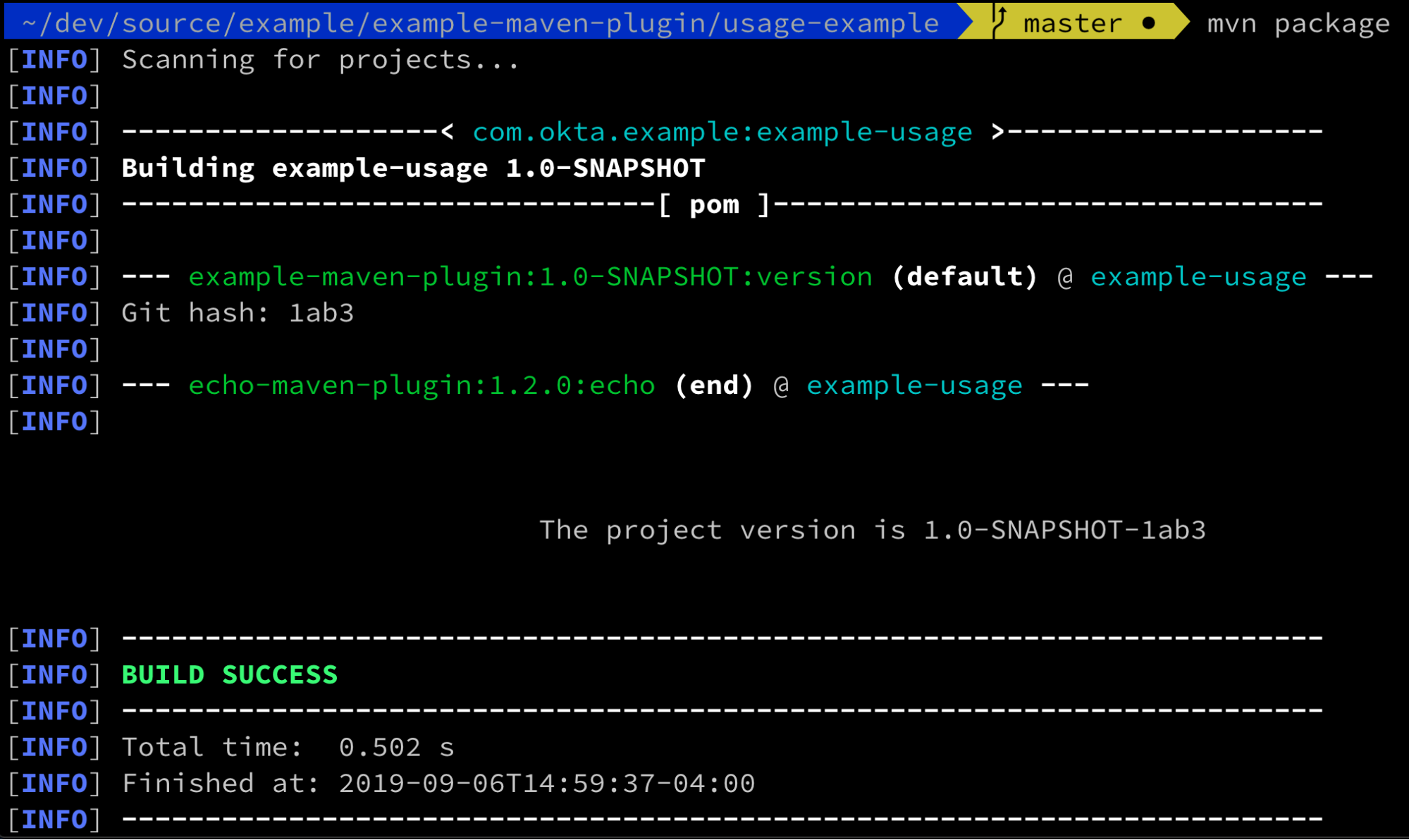
Apache Maven is still the most popular build tool in the Java space, thanks to the popularity of its ecosystem of plugins. It’s easy to find an existing plugin to do almost anything your application needs, from ensuring your source files have license headers, to validating binary compatibility between versions. Occasionally though, you need to write a custom plugin to fulfill a requirement in your product. In this tutorial, I’m going to show you how...