On this page
Protect your API endpoints
Add a layer of authorization to your web services with Okta API Access Management.
Learning outcomes
- Configure a web API to use Okta
- Define which endpoints require authorization and which don't
- Enable Cross-Origin Resource Sharing (CORS) for the API
- Test the API is secure
What you need
- An Okta Integrator Free Plan org (opens new window)
- Postman (opens new window) to test the API
Sample code
Note: Several standalone tools can send requests to APIs and allow you to inspect the responses. Our documentation uses Postman and offers Postman Collections (opens new window) to test its APIs more efficiently with a GUI. It also includes HTTP requests as text for those who prefer to use a terminal utility such as cURL (opens new window).
Overview
Background services and third-party APIs that access your APIs require the same levels of authentication and authorization (opens new window) as users who access your web apps. However, a machine-to-machine sign-in flow is silent and requires no user interaction. Use Okta to grant the correct level of access to your APIs on your behalf.
This quickstart contains the following tasks:
- Check that API Access Management is enabled
- Create and configure a new web API to use Okta
- Configure different levels of access for different endpoints
- Enable CORS for your API
- Test your API is secure
Tip: You need your Okta org domain to follow this tutorial. It looks like
integrator-123456.okta.com. See Find your Okta domain. Where you see{yourOktaDomain}in this guide, replace it with your Okta domain.
Note: For a similar use case where Okta secures a machine-to-machine sign-in flow between a background service app and the Okta APIs, rather than a service app and your own API, see Implement OAuth for Okta with a service app
Check that API Access Management is enabled
API Access Management (API AM) is the feature in your org that allows Okta to secure your APIs. When enabled, API AM allows you to create an authorization server that establishes a security boundary for your APIs. All new developer orgs have API AM enabled by default, but it’s optional for production orgs. Check that it’s enabled in your org as follows:
- Open the Admin Console for your org.
- Sign in to your Okta organization (opens new window) with your administrator account.
- Click Admin in the upper-right corner of the page.
- Go to Security > API to view the API AM area.
If no Authorization Servers tab exists, API AM isn’t enabled in your org. Contact your support team to enable this feature in your org or create an Okta Integrator Free Plan org (opens new window).
Note your authorization server name and audience
This tutorial uses the default custom authorization server to secure your API. Make a note of its name and audience value to configure your API:
- From the API AM area in the Admin Console, select the Authorization Servers tab.
- Go to the entry for the default server and make a note of two values.
- Audience:
api://default. - Authorization Server Name:
default.
- Audience:
Where you see {yourAudience} and {yourAuthServerName} in this guide, replace with api://default and default, respectively.
Note: You can either create a custom authorization server or use the default to protect your APIs. In either case, you need an appropriate license to use them in production. If you're using a custom authorization server other than
default, you must use theidof the authorization server rather than thename.
For further information, see Authorization servers.
Create and configure a new web API to use Okta
Now that you have an authorization server and noted how to identify it, complete the following steps:
- Create an API project.
- Add the required packages to your project.
- Configure your API to use Okta.
- Create two endpoints to secure.
Create an API project
Add the required packages to your project
Configure your API to use Okta
Earlier you noted your authorization server name and audience. Add these and your Okta domain to your API's configuration.
Create two endpoints to secure
Create two endpoints in your project that cover two different use cases:
api/whoami—a protected endpoint (access-restricted API)api/hello—an endpoint that anonymous users can access (unsecured API)
Configure different levels of access for different endpoints
In many APIs, all endpoints require authorization. There may be a mix of protected and unprotected endpoints in others. These examples show you how to assign protected and unprotected access to an endpoint.
Require authorization for all endpoints
Allow anonymous access for specific routes
Configure access on a per-route basis to allow a mix of protected and anonymous endpoints.
Enable CORS for your API
Enable Cross-Origin Resource Sharing (CORS) (opens new window) only if the API is being called from an app or API hosted on a different domain. For example, if your API is hosted on api.example.com while your app is accessing it from example.com, you must enable CORS.
Test that your API is secure
You can now test if your endpoint security works as intended. To do this, complete the following steps:
- Create an API services integration to represent another machine or service attempting to make requests to the API.
- Create a custom scope for the API for the authorization server to assign to the API integration.
- Run your API.
- Use Postman (opens new window) to
Create an API Services integration
When another machine or service (rather than users) consumes an API, it uses the Client Credentials flow (opens new window) to identify itself and request an access token. Create an API services integration that has this flow enabled.
- Open the Admin Console for your org.
- Go to Applications > Applications to view the current app integrations.
- Click Create App Integration.
- Select API Services as the Sign-in method, and click Next.
- Enter an integration name, and click Save.
The configuration page for the new API services integration appears. Make a note of two values that you use to request your access token:
- Client ID: Found on the General tab in the Client Credentials section.
- Client Secret: Found on the General tab in the Client Credentials section.
Moving on, where you see {yourClientId} and {yourClientSecret} in this guide, replace them with your client ID and client secret.
Create a custom scope for the API
Scope is a way to limit an app's access to your API. An access token must include a list of the scopes an app integration can perform. Create a custom scope to query both endpoints for the API.
- Go to Security > API to view the API AM area.
- Select the Authorization Servers tab.
- Go to the entry for the default server and click its name.
- Select the Scopes tab and click Add Scope.
- Enter a name for the scope. For example, "AccessAll".
- Click Create.
- Ensure that the table contains the new scope.
Run Your API
Now, start your server to get your API running.
Leave your API running locally (or deployed if desired) and proceed to the next step.
Test with Postman
Start Postman if it's not open already. First, you request an access token from Okta and then check your APIs are protected correctly.
Request an access token for the API
Make an HTTP POST request to /token (opens new window) using the client ID and secret you noted earlier.
Select + in the Postman workbench to open a new request tab.
Select GET and change it to POST.
Enter
https://{yourOktaDomain}/oauth2/{yourAuthServerName}/v1/tokenfor the URL.Note: If you're using a custom authorization server other than
default, use the authorization serveridin place of the{yourAuthServerName}placeholder.In the Params tab, create two key-value pairs:
- Key:
grant_type, Value:client_credentials - Key:
scope, Value:{yourCustomScope}
- Key:
Select the Authorization tab, and then select Basic Auth for type.
Enter
{yourClientId}for Username and{yourClientSecret}for Password.Select the Headers tab and add two new headers:
- Name: Cache-Control and Value: no-cache
- Name: Content-Type and Value: application/x-www-form-urlencoded
Click Send to receive an access token.
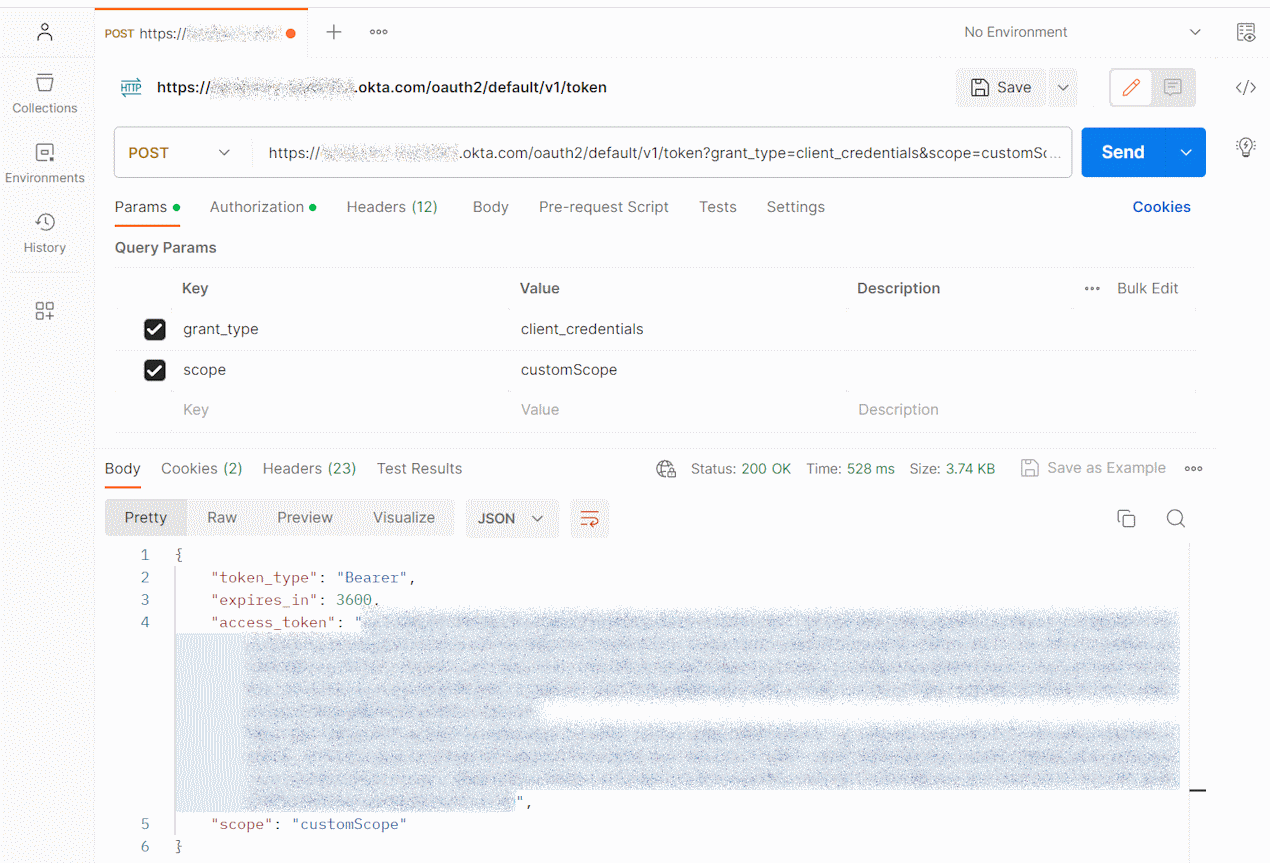
Copy the value returned in the
access_tokenobject field and use it for testing your API in the next section.
Query the hello and whoami endpoints
Now you can test your secured API endpoints. First, test the \whoami endpoint, which requires authorization:
- Select + in the Postman workbench to open a new request tab.
- Enter for URL.
- Select the Authorization tab, and then select the Bearer Token for type.
- Enter the token that you received earlier for Token.
- Click Send.
- Ensure that you received a
200 OKresponse. - Select the Authorization tab, and then select No Auth for type.
- Ensure that you received a
401 Unauthorizedresponse.
Now test the hello endpoint that doesn't require authorization:
- Select + in the Postman workbench to open a new request tab.
- Enter for URL.
- Select the Authorization tab, and then select the Bearer Token for type.
- Enter the token that you received earlier for Token.
- Click Send.
- Ensure that you received a
200 OKresponse. - Select the Authorization tab, and then select No Auth for type.
- Ensure that you still receive a
200 OKresponse.
Next steps
Learn more about the concepts introduced in this guide:
- API Access Management
- Authorization servers
- OAuth 2.0 Client Credentials flow
- Test the Okta REST APIs using Postman
- Define your own custom OAuth 2.0 scopes, claims, and access policies to support authorization for your APIs.
- Customize tokens returned from Okta from custom claims