Articles tagged vulnerabilities
Security.txt: Make Vulnerabilities Easier to Report
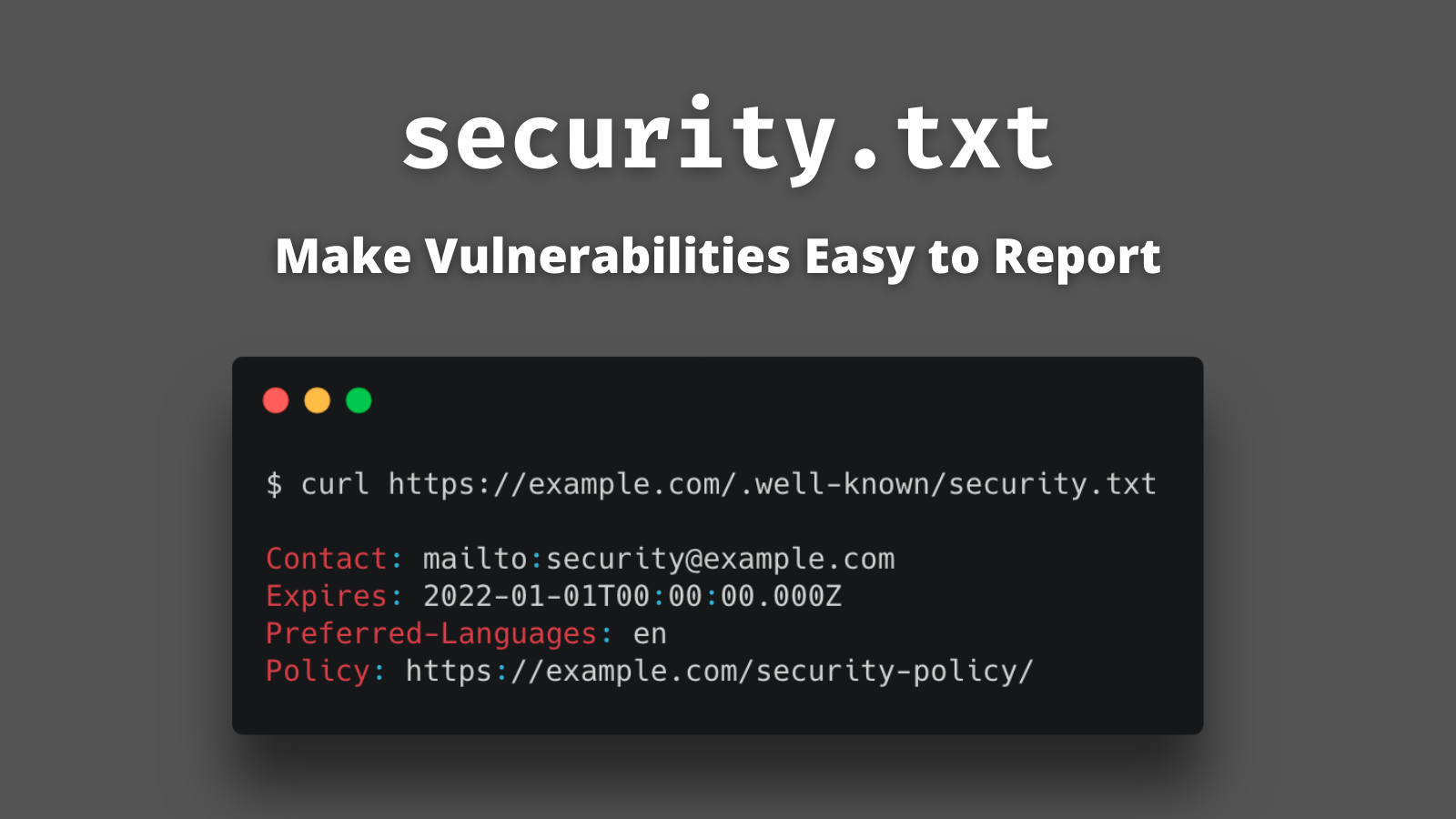
We all know that all software has bugs and that security is hard, but somehow we are still surprised when we see new vulnerabilities. Vulnerability A bug, flaw, weakness, or exposure of an application, system, device, or service that could lead to a failure of confidentiality, integrity, or availability. In 2020, there were 18,395 vulnerabilities reported, which means about 50 new vulnerabilities are reported every day. These numbers only include what has been reported to...
A Developer Guide to Reporting Vulnerabilities

Many of us are not familiar with vulnerability reporting and how it is different from reporting a regular bug. Frequently, I’ve seen people report vulnerabilities or potential security issues incorrectly. A public bug tracker or Stack Overflow is NOT the right tool; developers need to handle vulnerabilities differently and should not disclose them until the project/vendor fixes them. In this post, you will learn basics about vulnerabilities, how they relate to Common Vulnerabilities and Exposures...
Combat Side-Channel Attacks with Cross-Origin Read Blocking

As if developers didn’t have a big enough task securing web applications from software-layer attacks, they now have to contend with another threat: hardware-layer vulnerabilities. These complex cybersecurity flaws were introduced long before many modern developers began coding and extend from the inner workings of a computer’s silicon to a web application’s code. If exploited, hardware-layer vulnerabilities can result in leaked information from the web browser to an attacker. Luckily, Cross-Origin Read Blocking (CORB) is...