On this page
Set up an Okta app
This guide covers some SDK-specific instructions for how to set up an app. Then, you can run the Identity Engine sample apps or integrate the SDK or Widget into your own app.
Note: For introductory information about setting up an Okta org, see Set up your org.
Learning outcomes
Get a new app set up and ready for various use cases.
What you need
Overview of the embedded identity solutions
Okta provides two embedded identity solutions:
- Embedded SDK only: A highly customizable solution that provides native language support for various identity use cases.
- Embedded Widget + SDK: A quick and easy to set up solution that moves most of the heavy lifting to Okta. The amount of code that you need to write is small. However, many of the most advanced identity use cases (for example, social sign-in, multifactor authentication) are supported out of the box.
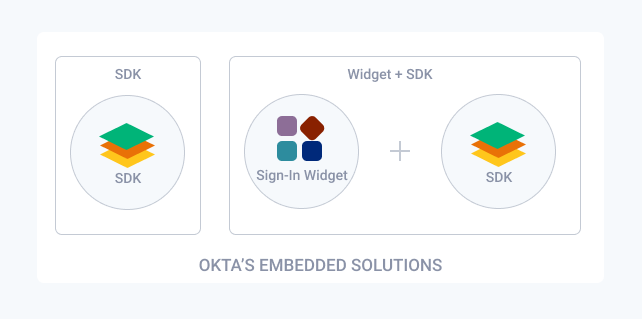
This guide shows you how to set up your Okta org to support the embedded SDK or the embedded widget with SDK solutions. Ensure that you get set up with Okta and set up your Okta org for your use case before you
Note: You can use direct authentication with your apps in Identity Engine rather than an embedded SDK. This enables you to directly authenticate users rather than delegating authentication to Okta Identity Providers and authorization servers through an HTTP redirect in a browser. Direct authentication is beneficial in scenarios where there's a high degree of trust between the user and the app. It's also beneficial where browser-based flows aren't feasible, like with mobile apps. See the
/challengeendpoint (opens new window), the/oob-authenticateendpoint (opens new window), and the newgrant_typesfor the/tokenendpoint (opens new window) to help tailor authentication to your specific use cases. Also, for information on how to set up each new grant type, see Implement by grant type.
Get set up
Sample apps are provided for each solution to show you exactly how to integrate the SDK and Sign-In Widget into your own app. Before you can run the sample apps or integrate embedded authentication into your own app, you need to do the following:
- Create your Okta account.
- Verify that the Interaction Code grant type is enabled.
- Update the default custom authorization server.
- Create an app.
After you've created your app, you need to set up your Okta org for your use case.
Create an app
Create an app integration that represents the app you want to add authentication to with Okta:
Go to Applications > Applications in the Admin Console.
Click Create App Integration.
Select OIDC - OpenID Connect as the Sign-in method.
Enter an app name.
Select the Refresh Token checkbox.
Click Advanced in the Grant type section and ensure that the Interaction Code checkbox is selected.
Note: If the Interaction Code checkbox doesn’t appear, the Interaction Code grant type isn’t enabled for your org. To enable it, go to Settings > Account > Embedded widget sign-in support. See Verify that the Interaction Code grant type is enabled.
Set Sign-in redirect URIs to
Set Controlled Access to Allow everyone in your organization to access.
Click Save.
Note the Client ID value (and if applicable, the Client secret value) on the General tab. You need it later in your embedded solution.
Note: New apps are automatically assigned the default app sign-in policy, which requires a user to verify their identity with two factors. To view or change this policy, select the Sign On tab, and then locate the User Authentication section.
Set up your Okta org for your use case
After you create your app integration in your Okta org, configure your app and org to support the use cases that you're implementing:
- For a password-optional use case, see Set up your Okta org for a password-optional use case
- For a multifactor use case, see Set up your Okta org for a multifactor use case
- For a social sign-in use case, see Set up your Okta org for a social IdP use case
Set up your Okta org for a social IdP use case
Use this section to set up your Okta org and app to support Facebook IdP use cases that are available in this embedded authentication guide. If you want to implement a use case with another social IdP, see Add an external identity provider. Review the list of Okta-supported social IdPs and instructions on how to configure them for social login with Okta.
Perform the following configurations after you create an app to set up the Facebook IdP and your Okta org:
- Create a Facebook app in Facebook.
- Set up the Facebook test user.
- (Optional) Switch your Facebook app to Live mode—this step isn't required if you want to remain in Facebook Development mode.
- Create the Facebook Identity Provider in Okta.
- Add an Identity Provider routing rule in Okta.
Create a Facebook app in Facebook
- Go to Facebook for Developers (opens new window) and click the Login link. If you don't have an account, create one.
- Use these Facebook instructions (opens new window) as a guide to create a Facebook app. When you create the Facebook app, ensure that you select None as the app type.
- Select the app that you created from the Facebook Apps (opens new window) page.
- Scroll to the Add a product section on the App Dashboard page and click the Set up link in the Facebook Login tile.
- Select Web as the platform type on the first set up page.
- Set the value for Site URL to
https://{yourOktaDomain}/oauth2/v1/authorize/callback(for example:https://integrator-12345678.okta.com/oauth2/v1/authorize/callback). - Click Save, Continue, and then click Next until you finish.
Configure Facebook settings
- Click Facebook Login (under products) in the left navigation menu, and then click Settings.
- Locate Client OAuth Settings on the Settings page and add the following URLs for the Valid OAuth Redirect URIs field:
https://{yourOktaDomain}/oauth2/v1/authorize/callback(for example,https://integrator-12345678.okta.com/oauth2/v1/authorize/callback). - Click Save Changes at the bottom of the page.
- Expand Settings on the left side of the page, and then click Basic.
- Save the App ID and the App Secret values so you can add them to your Okta org's Identity Provider settings.
Set up the Facebook test user
A test account is required to test Facebook sign-in in Development mode. Facebook automatically creates one test user for you. Perform the following steps to find, set the password, and save this user's information.
- From the Facebook App Dashboard page, click Roles and then click Test Users.
- Click Edit for the test user and select Change the name or password for this test user.
- In the Edit Test User dialog box, set a password in the New Password and Confirm New Password fields.
- Click Save.
- Save the test user's email and password for testing social IdP sign-in use cases with Okta and Facebook.
Switch your Facebook app to Live mode
Note: This section is optional.
By default, your Facebook app is in Development mode. This means that only the test user and the user that you used to sign in and create the Facebook app can use the app. As a result, you can only use these users when you test your Facebook sign-in use cases.
If you would like to sign in any public Facebook user, you need to set the Facebook app to Live mode. To switch your Facebook app to Live mode, perform the following steps:
- From the Facebook App Dashboard page, click Settings and then click Basic.
- Specify a value in the Privacy Policy URL field for your app. If you don't have a privacy URL, you can temporarily use:
https://www.okta.com/privacy-policy/. - Click Save Changes at the bottom of the page.
- At the top of the App Dashboard page, use the App Mode toggle to switch the app from In development to Live mode.
- In the Switch to Live Mode dialog box, click Switch Mode.
Create the Facebook Identity Provider in Okta
To connect your org to Facebook, you need to add and configure the Facebook IdP in Okta. The following steps assume that you've created and configured your Facebook app. Ensure that you have the Facebook App ID and App Secret values available.
- In the Admin Console, go to Security > Identity Providers.
- Click Add Identity Provider, and then select Add Facebook.
- Enter a name (for example, Facebook IdP) on the Add Identity Provider - Facebook page.
- Keep the default SSO Only option for the IdP Usage field.
- Specify the Facebook App ID as the Client ID, and the Facebook App Secret as the Client Secret.
- Keep the default values for public_profile and email in the Scopes field, and click Add Identity Provider.
Add an Identity Provider routing rule in Okta
The final step is to add the created Facebook IdP to the routing rule.
Go to Security > Identity Providers in the Admin Console.
Click the Routing Rules tab on the Identity Providers page, and then click Add Routing Rule.
Specify the Rule Name (for example: Facebook and Okta Rule).
Select the Facebook Identity Provider that you created from the THEN Use this identity provider dropdown list. Since Okta is the default IdP, the two values should be:
- Okta
- Facebook Identity Provider (IdP)
Click Create Rule.
Click Activate at the prompt. Your new rule appears above the Default Rule in the routing rule list. This top position signifies that the setting in your new rule overrides the Default Rule.