On this page
Self-service registration
Note: A request context for the browser client is required when a server-side web app uses an embedded SDK as a proxy between itself and Okta. This context contains values (geolocation, IP address, and user agent) that inform a secure response. However, these values are currently taken from the server rather than the client. As a result, network zones and behaviors that drive their conditions based on these request context values don’t currently work.
Enable a self-registration flow in your app using the embedded SDK.
Learning outcomes
- Configure your Okta org for self-service registration.
- Set up the password, email, and/or phone authentication factors.
- Set up and send a verification email during new user registration.
What you need
- An app that uses the embedded Identity Engine SDK
- Okta org already configured for a multifactor use case
- Identity Engine SDK set up for your own app
Sample code
Overview
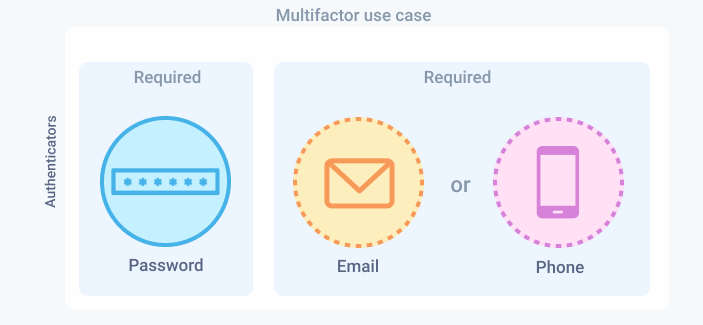
Self-service registration allows users to sign up to an app by themselves. In this use case, the user must register with a password, email, and/or phone factors. Enable self-service registration for the app in your Okta org and then build the self-service registration flow in your app.
Configuration updates
Configure your Okta org to accept self-registration with the password, email, and/or phone factors.
- See .
- Create a user profile policy (opens new window).
- Set the Email and Phone authenticators as optional enrollment factors.
Set the email and phone authenticators as optional enrollment factors
- Go to Security > Authenticators to view the available authenticators.
- Select the Enrollment tab.
- Click Edit under Default Policy.
- Go to the Effective factors section of the Edit Policy dialog and set Email and Phone to Optional.
- Click Update Policy.
Summary of steps
Integration steps
Send a confirmation email even if the authenticator is disabled
Even when only the password factor is required for an Okta app, you can still send a confirmation email.
To replicate this scenario:
- Configure your org following the steps described in .
- Set your app's app sign-in policy to require only the password factor.
- In the Admin Console, go to Applications > Applications.
- Select your app, and then go to the Sign On tab.
- In the User authentication section, click Edit.
- Set App sign-in policy to Password only, and click Save.
- Set your app's Initiate login URI to its sign-in URI. By setting this value, the email verification link for new user enrollment redirects the user to the URL provided in the Initiate login URI field.
- Select the General tab.
- In the General Settings section, click Edit.
- Set Initiate login URI to your Sign-in Redirect URI, and click Save.
- Make email verification mandatory in your default user profile policy.
- Go to Security > User Profile Policies.
- Click the pencil icon next to the Default policy.
- Ensure that Required before access is granted is selected for Email Verification.
During new user registration, there are no factors required other than the password. However, email verification is set to Required in the profile enrollment configuration. In this case, the user receives an email that uses the Registration - Activation email template. The user clicks the link in the activation email and is redirected to the sample app's home page.