On this page
Google Authenticator integration guide
This guide shows you how to integrate Google Authenticator into your authentication use cases using the embedded SDK.
Learning outcome
Understand the Google Authenticator flow.
What you need
- Google Authenticator installed on a mobile device
Sample code
Why choose Google Authenticator
Google Authenticator is an authenticator app developed by Google that's used to verify the identity of a user. The app is often used with a password to strengthen user accounts from security attacks. This approach is considered more secure than other authenticators such as SMS. It's resistant to SIM swap attacks, and it doesn't require a cellular or wireless network to use. Setup can be as easy as a snapshot of a QR Code.
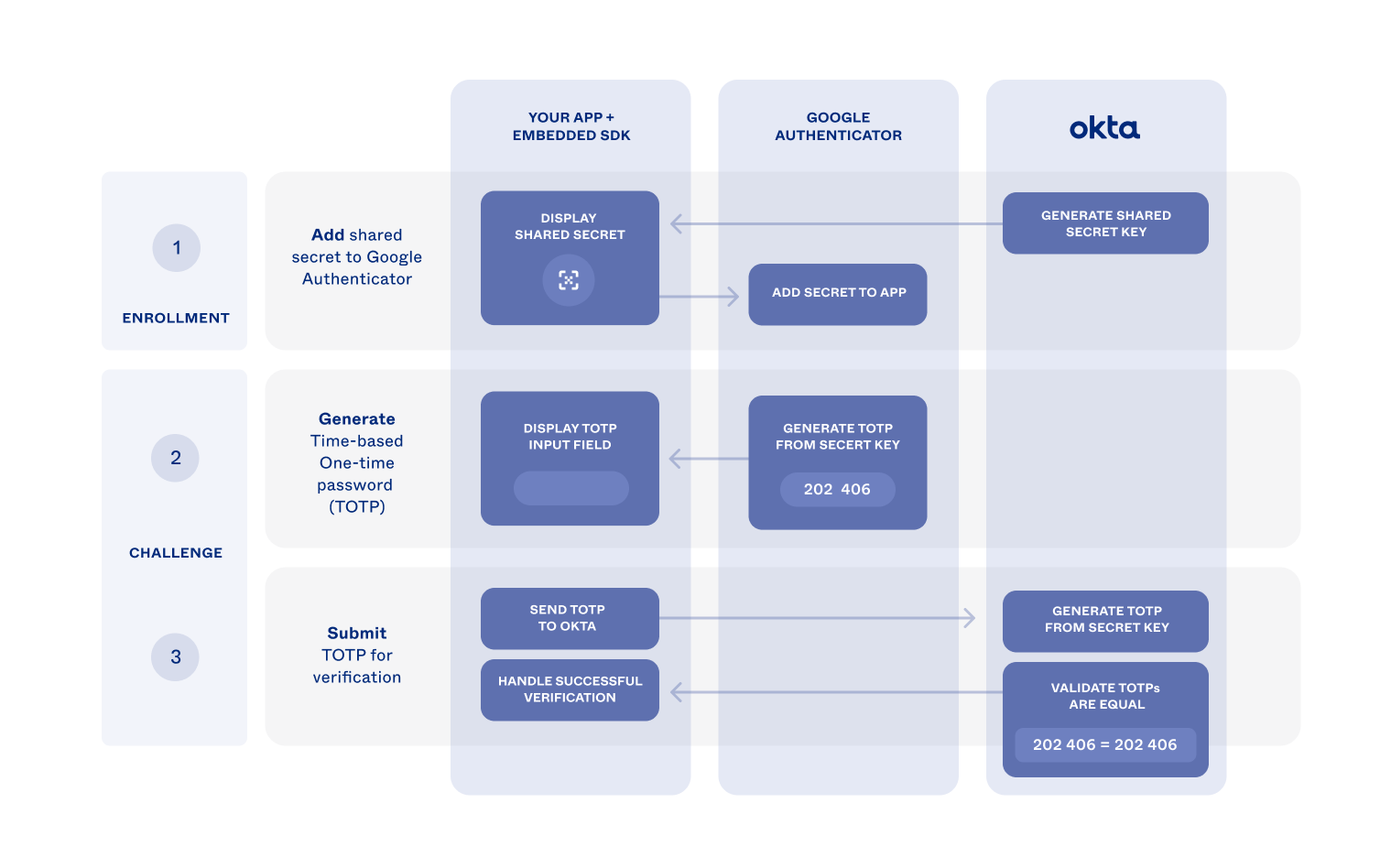
Authentication flow
After a user is enrolled in Google Authenticator, the Service Provider (for example, a website) presents a challenge. The challenge asks for a time-based one-time passcode (TOTP) during authentication. Google Authenticator generates the TOTP, and the user submits it to the Service Provider for verification. The Service Provider independently generates the password and validates that the submitted password is identical to the generated one.
A shared key linking the Google Authenticator app and Service Provider allows for both entities to generate the same password. The Service Provider generates the shared key. Then the Service Provider adds the key to the app during enrollment.
As the Service Provider, you can provide Google Authenticator support to your users. Enable Google Authenticator in your Okta org. Use the embedded SDK to build support for it in your app.
The following diagram illustrates how the Google Authenticator enrollment and challenge flows can work in your app.
Update configurations
Before you can start using Google Authenticator, create an Okta org app as described in
Add Google Authenticator to your org
First, add Google Authenticator to your org and enable it.
- Open the Admin Console for your org.
- Choose Security > Authenticators to show the available authenticators.
- If the Google Authenticator isn't in the list:
- Click Add Authenticator.
- Click Add on the Google Authenticator tile, and then click Add in the next dialog.
- Select the Enrollment tab.
- Check that Google Authenticator is set to either Optional or Required in the Eligible Authenticators section of the default policy.
- If Google Authenticator is set to Disabled, click Edit for the default policy.
- Select Optional from the dropdown box for the Google Authenticator, and then click Update Policy.
Set your app integration to use Google Authenticator
New apps are automatically assigned the shared default app sign-in policy (opens new window). This policy has a catch-all rule that allows a user access to the app using either one or two factors, depending on your org setup. In production, it becomes evident when you can share your authentication needs between apps. Okta recommends that you create a policy specifically for your app for testing purposes.
Open the Admin Console for your org.
Choose Security > Authentication Policies to show the available app sign-in policies.
Click Add a Policy.
Give the policy a name, and then click Save.
Locate the catch-all rule of the new policy and select Actions > Edit.
Select Allowed after successful authentication.
Set User must authenticate with to Password + Another factor.
For Possession factor constraints
- Verify that Device Bound is selected.
- Verify that Google Authenticator is listed in the box under Additional factor types. If it isn't listed, check that the authenticator has been enabled using steps 4 and 5 of Add Google Authenticator to your org.
- Click Save.
Select the Applications tab for your newly created policy, and then click Add App.
Find your app in the list and click Add next to it.
Click Close.
Verify that the app is now listed in the Applications tab of the new policy.
Install Google Authenticator
Install the Google Authenticator app on your mobile device using either the Google Play (Android) or the Apple App Store (iOS).
Integrate SDK for authenticator enrollment
Summary of enrollment flow
The following summarizes the Google Authenticator enrollment flow using a user sign-in use case.
Integrate SDK for authenticator challenge
Summary of challenge flow
The following summarizes the Google Authenticator challenge flow using a user sign-in use case.