Introducing xaa.dev: A Playground for Cross App Access
AI agents are quickly becoming part of everyday enterprise development. They summarize emails, coordinate calendars, query internal systems, and automate workflows across tools.
But once an AI agent needs to access an enterprise application on behalf of a user, things get complicated.
How do you securely let an AI-powered app act for a user without exposing credentials, spamming consent prompts, or losing administrative control?
This is the problem Cross App Access (XAA) is designed to solve.
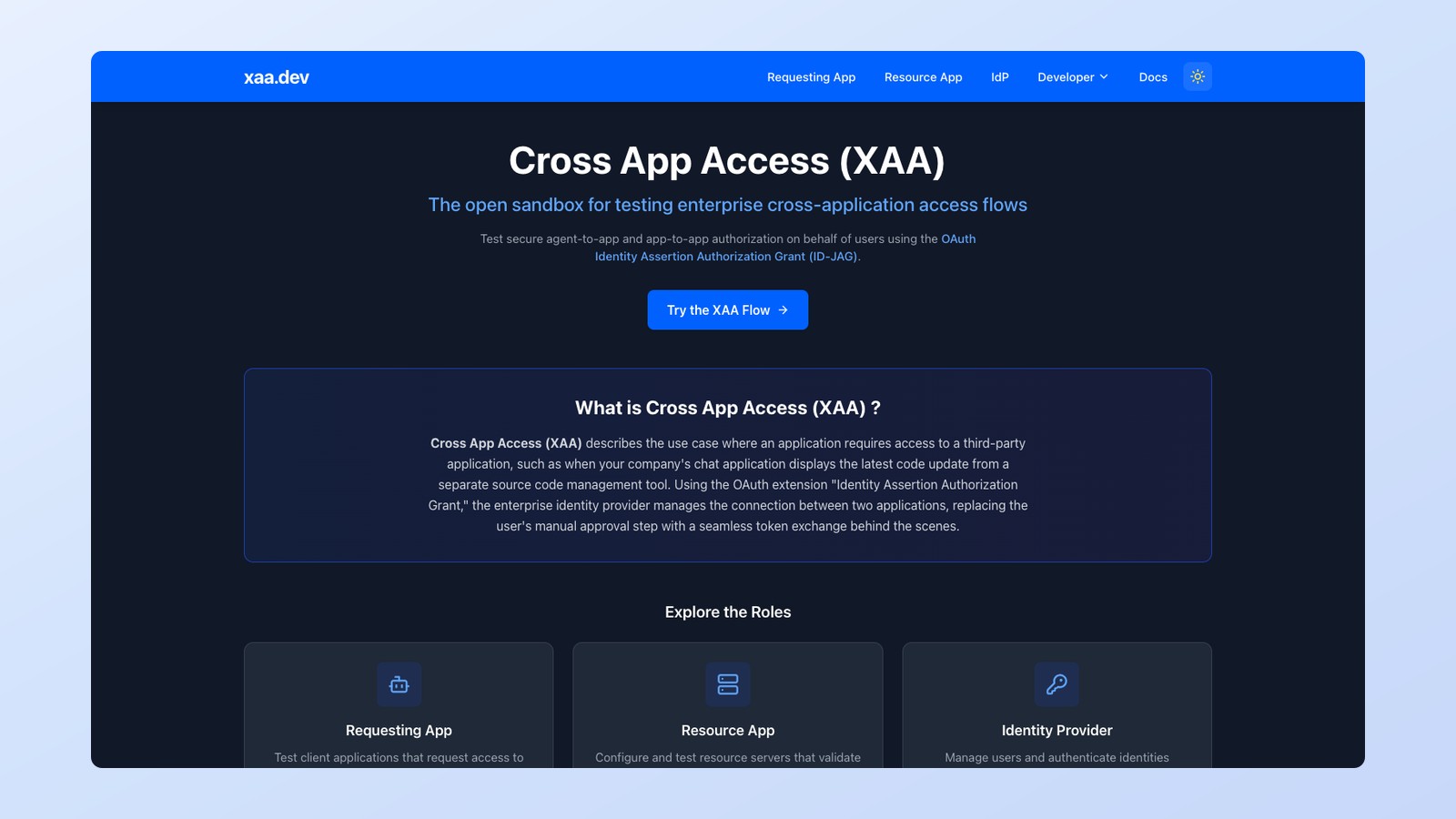
Today, we’re introducing xaa.dev, a free, open playground that lets you explore Cross App Access end-to-end. No local setup. No infrastructure to provision. Just a working environment where you can see the protocol in action.

Note: xaa.dev is currently in beta. We’re actively developing new features for the next release, and your feedback helps shape what comes next.
Table of Contents
- What is Cross App Access?
- The problem: testing XAA is hard
- What you can do on xaa.dev
- How to get started
- Why we built a testing site for cross app access
- Inspect the XAA flow
- Learn more
What is Cross App Access?
Cross App Access refers to a typical enterprise pattern: one application accesses another application’s resources on behalf of a user.
For example:
- An internal AI assistant fetching updates from a project management system
- A workflow engine booking meetings through a calendar API
- An agent querying internal data sources to complete a task
Traditionally, OAuth consent flows handle this. That approach works well for consumer-based apps, but it creates friction in enterprise environments where organizations require workforce oversight:
- Applications and their access levels are centrally managed
- IT teams need visibility into trust relationships
- Access must be revocable without user involvement
Cross App Access shifts responsibility from end users to the enterprise identity layer.
Instead of prompting users for consent, the Identity Provider (IdP) issues a signed identity assertion called an ID-JAG (Identity JWT Authorization Grant). This assertion cryptographically represents the user and the requesting application. Resource applications trust the IdP’s assertion and issue access accordingly.
The result:
- No interactive consent screens making application access seamless for employees
- Clear, auditable trust boundaries
- Complete administrative control over app-to-app access
For a deeper dive into why this matters for enterprise AI, read more about Cross App Access in this post:
Manage user and non-human identities, including AI in the enterprise with Cross App Access
The problem: testing XAA is hard
XAA is built on an emerging OAuth extension called the Identity Assertion JWT Authorization Grant – an IETF draft that Okta, along with public and industry contributors, has been actively contributing to. It’s powerful, but it’s also new, and new protocols need experimentation.
Here’s the challenge: to test XAA locally, you’d need to spin up:
- An Identity Provider (IdP)
- An Authorization Server for the resource application
- The resource API itself
- A requesting application (the agent or client app)
That’s hours (or days) of configuration before you can even see a single token exchange. Most developers give up before getting to the interesting part.
xaa.dev changes that.
We pre-configured all the components so you can focus on understanding the flow, not debugging dev environments. Go from zero to a working XAA token exchange in under 60 seconds.
Launch the playground. It’s free and requires no signup.
What you can do on xaa.dev
The playground gives you hands-on access to every role in the Cross App Access flow:
Requesting App
Step into the shoes of an AI agent or client application. Authenticate a user, request an ID-JAG from the IdP, and exchange it for an access token at the resource server.
Resource App
See the other side of the transaction. Watch how a resource server validates the identity assertion, verifies the trust relationship, and issues scoped access tokens.
Identity Provider
We’ve built a simulated IdP with pre-configured test users. Log in, see how ID-JAGs are minted, and inspect the cryptographic claims that make XAA secure.
Resource MCP Server
Connect your AI agents using the Model Context Protocol (MCP). The playground provides a ready-to-use MCP server that acts as a resource application, letting you test how AI agents can securely access protected resources through the Cross App Access flow.
Bring your own Requesting App
The built-in Requesting App is great for learning, but the real power comes when you test with your own application, whether it’s a traditional app or an MCP client. Register a client on the playground, grab the configuration, and integrate it into your local app. This lets you validate your XAA implementation against a working IdP and Resource App without spinning up your own infrastructure. The playground documentation walks you through the setup step-by-step.
How to get started
Getting started with xaa.dev takes less than a minute:
Step 1: Open the playground
Visit xaa.dev. No account required.
Step 2: Explore the components
The playground has three components (Requesting App, Resource App, and Identity Provider), each with its own URL. Visit any component to see its configuration and understand how it participates in the XAA flow.
Step 3: Follow the guided flow
Walk through the four steps of the XAA flow: User Authentication (SSO), Token Exchange, Access Token Request, and Access Resource. Inspect the requests and responses at each step to see exactly how XAA works under the hood.
That’s it. No local tools installations, Docker containers, environment variables, or CORS headaches.
Watch this walkthrough video of the playground if you’d like a guided tour:
Why we built a testing site for cross app access
XAA is built on an emerging IETF specification, the Identity Assertion JWT Authorization Grant. As enterprise AI adoption accelerates, there’s a clear need: developers want to understand XAA, but the barrier to entry is too high.
xaa.dev lowers the barrier. It helps you:
- Learn faster – See the protocol in action before writing any code
- Build confidently – Understand exactly what tokens to expect and validate
- Experiment safely – Test edge cases without affecting production systems
Inspect the XAA flow
XAA is how enterprise applications will securely connect in an AI-first world. Whether you’re building agents, integrating SaaS tools, or just curious about modern OAuth patterns, xaa.dev gives you a risk-free environment to learn. Check it out and let us know how it works for you!
Learn more
Ready to go deeper? Check out these resources:
- Checkout Cross App Access Integration in Okta – Securing AI-driven access together
- Build Secure Agent-to-App Connections with Cross App Access – Hands-on implementation guide
- Identity Assertion JWT Authorization Grant (IETF Draft) – The specification behind XAA
Have questions or feedback? Reach out to us on Twitter, join the conversation on the Okta Developer Forums, or drop a comment below. We’re actively improving xaa.dev based on developer input – your feedback shapes what we build next.
Follow us on Twitter and subscribe to our YouTube channel for more content on identity, security, and building with Okta.
Okta Developer Blog Comment Policy
We welcome relevant and respectful comments. Off-topic comments may be removed.